The digital landscape is constantly evolving, and businesses are increasingly turning to the cloud to enhance agility, scalability, and cost-efficiency. At the forefront of this shift lies rehosting, often referred to as “lift and shift” cloud migration. This approach offers a rapid path to the cloud by simply moving existing applications and their associated infrastructure with minimal modifications. This method is attractive due to its speed and simplicity, offering a compelling starting point for cloud adoption.
This comprehensive exploration will dissect the intricacies of rehosting. We will define the core principles, explore its key characteristics, and delve into the advantages it offers, while also addressing the inherent challenges. We’ll navigate the step-by-step process, examine the tools and technologies employed, and provide insights into cost optimization and security considerations. Through case studies and future trend analysis, this analysis aims to equip you with a thorough understanding of rehosting’s role in modern cloud migration strategies.
Defining Rehosting (Lift and Shift) Cloud Migration
Rehosting, often referred to as “lift and shift,” is a cloud migration strategy that involves moving applications and their associated data from an on-premises environment or a legacy infrastructure to a cloud environment with minimal changes. This approach prioritizes speed and simplicity, aiming to replicate the existing infrastructure in the cloud with a focus on maintaining functionality.
Fundamental Concept of Rehosting
The fundamental concept of rehosting centers around replicating the existing application environment in the cloud. This means taking the application’s components—servers, databases, network configurations, and other dependencies—and moving them to a cloud provider’s infrastructure. The goal is to achieve a like-for-like migration, minimizing code modifications and refactoring efforts. This approach is particularly appealing when time-to-market and rapid cloud adoption are critical priorities.
Concise Definition for a Technical Audience
Rehosting, or lift and shift, is a cloud migration strategy characterized by the relocation of an application’s workload, including its associated operating systems, databases, and application code, to a cloud infrastructure without significant architectural changes. The primary objective is to expedite migration by reducing the need for code modifications and infrastructure redesign. This is often achieved by using cloud-compatible virtual machine images or containerization technologies.
Core Principles Driving the Lift and Shift Approach
The lift and shift approach is guided by several core principles that shape its implementation and success.
- Minimizing Application Changes: The core tenet is to avoid or minimize changes to the application code and architecture. This reduces the risk of introducing new bugs or compatibility issues during migration. This approach is often ideal for applications that are complex, poorly documented, or where the original source code is unavailable.
- Prioritizing Speed of Migration: The primary driver is to expedite the migration process. By avoiding significant architectural changes, the time required for assessment, planning, and execution is considerably reduced. This allows organizations to quickly realize the benefits of cloud computing.
- Leveraging Existing Infrastructure Investments: Lift and shift aims to reuse the existing infrastructure investments. By migrating the existing workloads, organizations can continue to use their existing operating systems, databases, and other software components without the need for immediate refactoring.
- Reducing Risk: The lift and shift strategy minimizes the risk of disrupting the existing application functionality. Since the application is moved with minimal changes, the risk of introducing new issues or breaking existing functionality is significantly lower.
- Focusing on Cost Optimization (Initially): While not always the primary goal, lift and shift can offer immediate cost benefits by leveraging the cloud provider’s infrastructure and potentially reducing on-premises hardware and maintenance costs. However, long-term cost optimization often requires subsequent optimization efforts.
Key Characteristics of Rehosting
Rehosting, often referred to as “lift and shift,” is a cloud migration strategy that involves moving applications and their associated infrastructure from an on-premises environment to the cloud with minimal or no changes to the application’s code. This approach prioritizes speed and ease of migration, making it a suitable option for specific scenarios.
Core Principles of Rehosting
Rehosting is characterized by several key principles that define its implementation and effectiveness. These principles differentiate it from other cloud migration approaches.
- Minimal Code Changes: The primary goal is to move the application as-is, reducing the need for code refactoring or rewriting. This approach aims to maintain the application’s functionality and behavior without significant alterations.
- Infrastructure Replication: The existing infrastructure components, such as servers, databases, and networks, are replicated in the cloud environment. This involves creating equivalent resources in the target cloud platform.
- Rapid Migration: Rehosting prioritizes speed of migration, often offering the fastest path to the cloud compared to other strategies. This is because the application’s structure and functionality remain largely unchanged.
- Cost-Effectiveness (Initial): In the initial stages, rehosting can be cost-effective due to the reduced need for development and testing. However, ongoing costs might vary depending on cloud resource utilization.
Scenarios Favoring Rehosting
Rehosting is most advantageous in specific situations where its strengths align with project goals and constraints. Understanding these scenarios helps in determining its suitability.
- Legacy Applications: Applications that are difficult or costly to refactor, such as those built on older technologies or with complex dependencies, are well-suited for rehosting.
- Time-Sensitive Migrations: When there’s a pressing need to migrate to the cloud quickly, rehosting offers a faster route compared to approaches requiring extensive code modifications.
- Disaster Recovery and Business Continuity: Rehosting can facilitate the creation of a cloud-based disaster recovery site, allowing for quick failover in case of an outage.
- Limited Cloud Expertise: Organizations with limited in-house cloud expertise may find rehosting easier to implement as it minimizes the need for specialized cloud-native development skills.
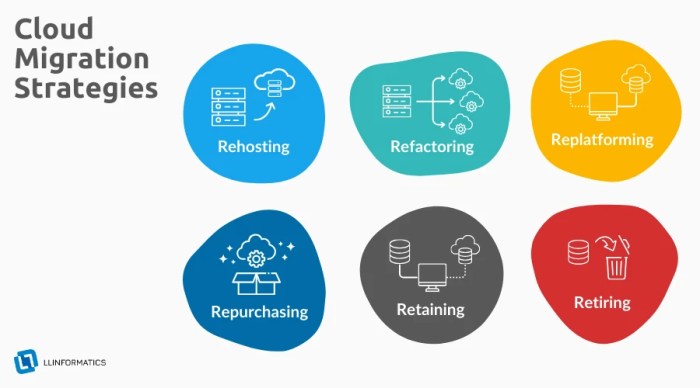
Comparison with Refactoring and Other Strategies
Comparing rehosting with other cloud migration strategies reveals its distinct advantages and disadvantages, helping to make informed decisions.
- Refactoring: Refactoring involves redesigning and rewriting parts of the application to leverage cloud-native services. This approach offers improved scalability, performance, and cost optimization but requires more time and effort than rehosting. Rehosting preserves the existing application architecture, while refactoring transforms it.
- Replatforming: Replatforming involves making some changes to the application to run it on a different platform, without altering the core architecture. This can include moving to a different operating system or database. It is more involved than rehosting but less so than refactoring.
- Repurchasing: Repurchasing involves replacing the existing application with a cloud-based SaaS (Software as a Service) solution. This eliminates the need for migration, but requires selecting and implementing a new application.
- Retiring: Retiring involves decommissioning an application. This is a viable option for applications that are no longer needed.
The following table summarizes the key differences between rehosting and refactoring:
| Characteristic | Rehosting | Refactoring |
|---|---|---|
| Code Changes | Minimal | Significant |
| Migration Speed | Fastest | Slower |
| Effort | Lowest | Highest |
| Cost (Initial) | Potentially Lower | Potentially Higher |
| Cloud Optimization | Limited | High |
In a real-world scenario, a company running a legacy application on physical servers might choose rehosting to quickly move to the cloud. Later, they might refactor the application to take advantage of cloud-native services and improve scalability.
Benefits of Choosing Rehosting
Rehosting, or lift and shift, offers a compelling pathway to cloud migration, particularly for organizations seeking a rapid transition with minimal initial architectural changes. This approach presents several advantages, streamlining the migration process and offering immediate operational benefits. These advantages often translate into significant cost savings and improved agility, making it an attractive option for various business scenarios.
Speed and Efficiency Gains
The primary benefit of rehosting lies in its inherent speed and efficiency. By avoiding complex refactoring or re-architecting, the migration process is significantly accelerated. This translates to quicker time-to-market for cloud-based applications and services. This speed advantage is a direct consequence of the simplified migration strategy.
Benefits for Different Business Units
Rehosting offers tailored benefits across various business units, each experiencing specific improvements.
- IT Operations: Rehosting reduces the operational burden associated with managing on-premises infrastructure. It allows IT teams to offload infrastructure management to the cloud provider, freeing up resources to focus on strategic initiatives and innovation. For example, instead of patching servers, IT staff can focus on implementing new features.
- Finance: The cost predictability of rehosting is a key financial advantage. Organizations can often accurately estimate the costs associated with cloud infrastructure, allowing for better budgeting and financial planning. This is particularly true when leveraging cloud provider pricing models and discounts.
- Development: Rehosting accelerates the development lifecycle. Developers can quickly deploy and test applications in the cloud environment without waiting for lengthy infrastructure provisioning cycles. This leads to faster iterations and quicker release cycles.
- Business Management: Rehosting provides improved business continuity and disaster recovery capabilities. Cloud platforms offer robust backup and recovery solutions, minimizing downtime and data loss risks. This directly contributes to business resilience.
- Security: While rehosting doesn’t automatically enhance security, it can improve it by leveraging the security features offered by cloud providers. Cloud providers often offer advanced security services, such as intrusion detection and prevention systems, that are more difficult and costly to implement on-premises.
Challenges and Considerations in Rehosting
Rehosting, while offering a rapid path to cloud adoption, presents several challenges that organizations must carefully consider. Successful rehosting projects require meticulous planning, comprehensive assessment, and proactive mitigation strategies. Failure to address these challenges can lead to performance degradation, security vulnerabilities, and increased operational costs.
Common Challenges Encountered During Rehosting Projects
Rehosting initiatives often encounter a series of hurdles that can impede progress and impact the overall success of the migration. These challenges span technical, operational, and organizational aspects.
- Application Complexity and Dependencies: Applications often have complex interdependencies with other applications, databases, and infrastructure components. Understanding and replicating these dependencies in the cloud environment is crucial. For example, a monolithic application may rely on specific network configurations, shared storage, or legacy APIs that are not directly compatible with the target cloud platform. Migrating such applications requires detailed analysis and potentially refactoring or re-architecting to ensure proper functionality.
- Data Migration and Synchronization: Migrating large datasets efficiently and securely to the cloud can be a significant challenge. Data integrity, downtime during migration, and data synchronization between on-premises and cloud environments must be carefully managed. Strategies such as using database migration services, bulk data transfer tools, or change data capture (CDC) techniques are often employed. For instance, a retail company with a large transactional database needs to minimize downtime during the migration process to avoid disruption to its online sales operations.
- Network Configuration and Connectivity: Establishing secure and reliable network connectivity between the on-premises environment and the cloud is critical. This involves configuring virtual private networks (VPNs), direct connections, or other networking solutions to ensure secure data transfer and application access. The performance of the migrated applications depends on the network latency and bandwidth.
- Skill Gap and Training: Rehosting requires specialized skills in cloud technologies, migration tools, and cloud platform management. Organizations may need to upskill existing IT staff or hire external consultants to overcome skill gaps. This includes training on cloud-specific services, security best practices, and cost optimization strategies.
- Cost Management and Optimization: Cloud environments offer various pricing models, and it’s essential to understand the cost implications of rehosting. Organizations must monitor resource utilization, optimize instance sizes, and leverage cost-saving features offered by the cloud provider. Without proper cost management, rehosting can lead to unexpected expenses.
- Security and Compliance: Ensuring the security and compliance of the migrated applications and data is paramount. This involves implementing appropriate security controls, such as access controls, encryption, and vulnerability scanning, and adhering to relevant industry regulations.
Potential Compatibility Issues with the Target Cloud Environment
Rehosting projects frequently encounter compatibility issues that necessitate careful planning and remediation. These issues can stem from differences in operating systems, software versions, and infrastructure services between the on-premises environment and the target cloud platform.
- Operating System Compatibility: Applications designed for specific operating systems (e.g., Windows Server, Linux distributions) may not be fully compatible with the target cloud’s operating system versions or configurations. This may require updating the operating system, reconfiguring the application, or using compatibility layers.
- Software Version Conflicts: Applications often depend on specific versions of software libraries, frameworks, and middleware. Compatibility issues can arise if the cloud environment does not support the required versions or if there are conflicts with other software components.
- Database Compatibility: Migrating databases to the cloud may involve compatibility issues with the target cloud’s database services (e.g., Amazon RDS, Azure SQL Database). Differences in database versions, features, and configurations can necessitate database schema changes, data type mapping, or application code modifications. For instance, an application using a specific SQL Server feature might not be fully compatible with the cloud-based managed SQL Server service.
- Hardware Virtualization Differences: The virtualization technologies used in the on-premises environment (e.g., VMware, Hyper-V) may differ from those used by the cloud provider. This can lead to compatibility issues with virtual machine configurations, drivers, and resource allocation.
- Network and Storage Configuration: Applications may rely on specific network configurations (e.g., IP addresses, DNS settings) and storage configurations (e.g., SAN, NAS). These configurations may need to be adapted to the cloud environment, potentially requiring changes to the application code or infrastructure setup.
- API and Service Dependencies: Applications often rely on APIs and services provided by the on-premises infrastructure. Migrating these dependencies to the cloud may require replacing them with cloud-native services or reconfiguring the application to interact with cloud-based alternatives.
Impact on Application Performance and Security After the Migration
The performance and security of applications can be significantly impacted after rehosting. Organizations must proactively address potential performance bottlenecks and security vulnerabilities to ensure a smooth transition and maintain a robust operational posture.
- Performance Degradation: Rehosting can sometimes lead to performance degradation if not properly planned and executed. This can be due to factors such as network latency, resource contention, or inefficient resource utilization. For example, an application running on a virtual machine in the cloud may experience slower response times if the underlying infrastructure is not properly provisioned or if there are network bottlenecks.
- Network Latency: Network latency between the application and its dependencies (e.g., databases, other services) can increase after migration, especially if the application is moved to a different geographic region. This can impact the application’s performance and user experience.
- Resource Constraints: If the cloud resources are not appropriately sized or configured, the application may experience resource constraints (e.g., CPU, memory, storage), leading to performance bottlenecks. Monitoring resource utilization and scaling the resources as needed are critical.
- Security Vulnerabilities: Rehosting can introduce new security vulnerabilities if the security controls are not properly configured or if the application is not updated with the latest security patches. It is essential to implement appropriate security measures, such as access controls, encryption, and vulnerability scanning.
- Data Breaches and Compliance Violations: Improperly secured cloud environments can be susceptible to data breaches and compliance violations. Organizations must ensure that they comply with relevant industry regulations (e.g., HIPAA, GDPR) and implement appropriate security measures to protect sensitive data.
- Increased Attack Surface: Moving applications to the cloud can increase the attack surface, as the application becomes accessible from the internet. Organizations must implement robust security measures, such as firewalls, intrusion detection systems, and security information and event management (SIEM) solutions, to protect against cyberattacks.
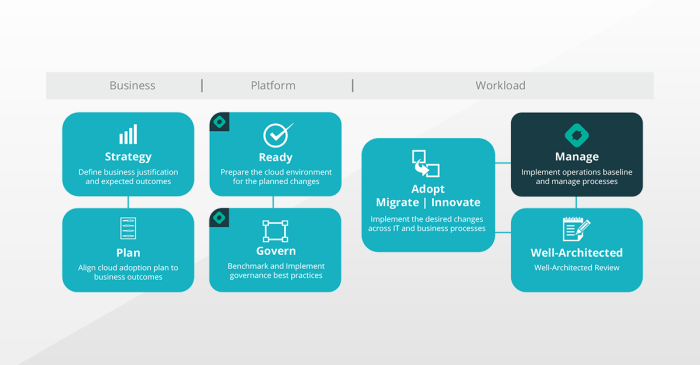
The Rehosting Process
Rehosting, often referred to as “lift and shift,” is a cloud migration strategy that involves moving applications and their associated infrastructure from an on-premises environment to a cloud platform with minimal changes. This approach prioritizes speed and simplicity, making it an attractive option for organizations seeking a rapid cloud adoption strategy. The rehosting process is not merely a technical undertaking; it requires careful planning, execution, and ongoing monitoring to ensure a successful transition and optimized performance in the cloud.
A Step-by-Step Guide for Executing a Rehosting Project
The following steps provide a structured framework for a successful rehosting project. Each stage is critical, and the order is designed to facilitate a smooth transition. Careful attention to detail at each stage minimizes risks and maximizes the benefits of cloud migration.
Stage-by-Stage Guide:
| Stage | Tasks | Considerations | Example |
|---|---|---|---|
| 1. Assessment and Planning |
|
| A financial services company, for instance, might begin by cataloging all its applications. They’d then identify those that are compatible with the target cloud provider and assess the dependencies between them. This step is critical to determine which applications can be rehosted without significant modifications and to understand how they will impact the overall infrastructure once moved. They’d also consider compliance standards such as PCI DSS or GDPR and ensure they meet the security requirements. |
| 2. Cloud Environment Setup |
|
| A retail company, after choosing a cloud provider, will create a Virtual Private Cloud (VPC) to isolate its resources. They would then set up subnets for different application tiers (e.g., web servers, database servers) and configure security groups to control network traffic. This ensures that sensitive data is protected, and that only authorized users can access the resources. |
| 3. Application and Data Migration |
|
| An e-commerce platform would likely use a tool like AWS Database Migration Service (DMS) or Azure Database Migration Service (Azure DMS) to move its databases to the cloud. Before migrating the live data, a test migration is performed to ensure that the process works as expected and that the application continues to function properly. During the migration, the system might be put in read-only mode to ensure that no transactions are missed. |
| 4. Testing and Validation |
|
| A healthcare provider will conduct rigorous testing of its migrated applications, which may include unit tests, integration tests, and end-to-end tests. They’ll verify that the application performs as expected and adheres to all relevant healthcare regulations (HIPAA). Performance tests will ensure the application can handle the expected load and user acceptance testing (UAT) will allow medical staff to use the application and provide feedback. |
| 5. Optimization and Monitoring |
|
| A manufacturing company will continuously monitor its migrated applications, utilizing tools like AWS CloudWatch or Azure Monitor. They will track key performance indicators (KPIs) such as CPU utilization, memory usage, and network latency. Based on the data, they can adjust instance sizes or network configurations to optimize performance and minimize costs. Furthermore, they would implement cost optimization strategies such as using reserved instances. |
Tools and Technologies for Rehosting
Rehosting, or lift-and-shift migration, necessitates the utilization of various tools and technologies to facilitate the seamless transfer of workloads from on-premises environments to the cloud. The selection of appropriate tools is crucial for minimizing downtime, reducing complexity, and ensuring a successful migration. These tools automate various aspects of the migration process, from assessment and planning to actual data transfer and post-migration validation.
Assessment and Planning Tools
Before initiating a rehosting project, a thorough assessment of the existing IT infrastructure is essential. Assessment tools help analyze the current environment, identify dependencies, and estimate the resources required for migration.
- Cloud Adoption Framework (CAF) tools: These tools, often provided by cloud vendors, offer frameworks and methodologies for planning and executing cloud migrations. They typically include assessment modules that analyze the on-premises environment, providing insights into application compatibility, resource utilization, and cost estimations.
- Third-party assessment tools: Tools like Cloudamize (now part of CloudHealth by VMware) and RISC Networks (acquired by Flexera) offer detailed assessments, including dependency mapping, application portfolio analysis, and cost modeling. They provide comprehensive reports that help organizations understand the scope and complexity of their migration projects.
Migration Tools
Migration tools automate the process of transferring workloads to the cloud. These tools typically offer features such as automated discovery, replication, and synchronization of data.
- AWS Migration Hub: This service from Amazon Web Services (AWS) provides a central location to track the progress of migrations and discover migration tools. It integrates with various AWS migration services, such as the AWS Database Migration Service (DMS) and AWS Server Migration Service (SMS).
- Azure Migrate: Microsoft Azure Migrate is a centralized hub for discovering, assessing, and migrating on-premises servers, databases, and applications to Azure. It offers tools for agentless and agent-based migration, supporting various operating systems and application types.
- Google Cloud’s Migrate for Compute Engine (formerly Velostrata): This tool from Google Cloud Platform (GCP) enables live migration of virtual machines to Compute Engine. It provides features like live migration, storage synchronization, and automated instance creation.
- VMware HCX: VMware HCX is a hybrid cloud mobility platform that simplifies application migration and disaster recovery across on-premises and cloud environments. It provides features like bulk migration, vMotion across clouds, and disaster recovery capabilities.
Data Transfer Tools
Efficient data transfer is critical for minimizing downtime during rehosting. Data transfer tools are designed to move large volumes of data quickly and securely.
- AWS Snowball: This service from AWS allows the transfer of large datasets by shipping physical storage devices to and from AWS. It is suitable for environments with limited network bandwidth.
- Azure Data Box: Microsoft Azure Data Box offers similar functionality to AWS Snowball, providing physical storage devices for transferring large datasets to Azure.
- Google Cloud Storage Transfer Service: This service from GCP enables the transfer of data from on-premises storage or other cloud providers to Google Cloud Storage.
Vendor-Specific Tools and Functionalities
Cloud providers offer a suite of tools tailored to their respective platforms, designed to streamline the rehosting process and leverage their specific features.
- AWS: AWS offers a comprehensive suite of tools, including the AWS Migration Hub, AWS Server Migration Service (SMS) for server migration, AWS Database Migration Service (DMS) for database migration, and AWS Snowball for data transfer. These tools are integrated to provide a seamless migration experience. For example, SMS allows for agent-based or agentless replication of on-premises servers, while DMS facilitates the migration of databases with minimal downtime.
- Azure: Azure Migrate provides a unified platform for assessing and migrating various workloads to Azure. Azure Database Migration Service assists in migrating databases. Azure Data Box offers options for offline data transfer. These tools work in concert to provide a holistic migration solution. For instance, Azure Migrate can assess on-premises virtual machines and provide recommendations for Azure virtual machine sizing and configuration.
- Google Cloud: Google Cloud provides Migrate for Compute Engine (formerly Velostrata) for live migration of VMs, and the Google Cloud Storage Transfer Service for data transfer. These tools are designed to work seamlessly with Google Cloud’s infrastructure and services. For example, Migrate for Compute Engine can migrate VMware VMs to Compute Engine with minimal downtime.
Comparison of Tools
The selection of a rehosting tool depends on several factors, including the size and complexity of the environment, the cloud provider chosen, and the specific requirements of the migration project. The following table provides a comparative analysis of some popular rehosting tools based on features and pricing:
| Tool | Provider | Key Features | Pricing Model |
|---|---|---|---|
| AWS Migration Hub | AWS | Centralized migration tracking, integration with other AWS migration services, assessment tools. | Free, pay-as-you-go for underlying services (e.g., DMS, SMS). |
| Azure Migrate | Microsoft Azure | Assessment, migration, and modernization capabilities, support for various workload types. | Free, pay-as-you-go for underlying services. |
| Migrate for Compute Engine | Google Cloud | Live migration of VMs, storage synchronization, automated instance creation. | Pay-as-you-go based on the compute resources used during migration. |
| VMware HCX | VMware | Hybrid cloud mobility, bulk migration, vMotion across clouds, disaster recovery. | Subscription-based, based on the number of VMs migrated. |
| Cloudamize (now part of CloudHealth by VMware) | VMware | Detailed assessment, dependency mapping, application portfolio analysis, cost modeling. | Subscription-based, based on the size and complexity of the environment. |
The pricing models can vary significantly. Some tools, like the core components of AWS Migration Hub and Azure Migrate, are offered free of charge, with users paying only for the underlying services they utilize during the migration process. Other tools, like VMware HCX and Cloudamize, are typically subscription-based, with pricing depending on the scope and scale of the migration project.
The choice of tool will influence the overall cost of the migration. The selection process should consider the specific needs of the migration, balancing functionality, and budget constraints.
Cost Analysis and Optimization in Rehosting
Rehosting, while often a faster migration strategy, demands a meticulous approach to cost management. A comprehensive understanding of associated costs, coupled with proactive optimization strategies, is crucial for realizing the full benefits of cloud migration. Failure to accurately assess and manage costs can lead to budget overruns and diminish the return on investment.
Calculating Rehosting Costs
Calculating the costs associated with rehosting requires a detailed assessment of various factors, encompassing both pre-migration and post-migration expenses. This analysis should consider both direct and indirect costs.
- Assessment and Planning Costs: These costs cover the initial assessment phase, including the analysis of existing infrastructure, application dependencies, and the development of a migration plan. This may include:
- Discovery Tools: Costs associated with using tools to discover existing infrastructure components, dependencies, and configurations.
- Consulting Fees: Expenses for engaging cloud migration consultants to assist with planning and strategy.
- Migration Tooling Costs: This category encompasses the expenses related to migration tools and software used to automate the transfer of workloads. This includes:
- Licensing Fees: Costs for licenses of migration tools, which can vary depending on the complexity of the migration and the features offered.
- Tool Training: Costs related to training personnel on the use of migration tools.
- Implementation and Execution Costs: This covers the direct costs of the actual migration process, including:
- Labor Costs: Salaries or hourly rates for the IT staff involved in the migration.
- Data Transfer Costs: Expenses for transferring data from the on-premises environment to the cloud, which can vary based on the amount of data and the chosen data transfer method.
- Cloud Infrastructure Costs: These are the ongoing costs associated with the cloud infrastructure after the migration, including:
- Compute Costs: Expenses for virtual machines, containers, or serverless functions.
- Storage Costs: Expenses for storing data in the cloud.
- Network Costs: Expenses for data transfer, bandwidth usage, and other network services.
- Operational Costs: Ongoing expenses related to managing and maintaining the migrated applications and infrastructure in the cloud, including:
- Monitoring and Management Tools: Costs for tools used to monitor the performance and health of cloud resources.
- Support and Maintenance: Expenses for cloud provider support and internal IT support.
- Contingency Costs: A budget set aside to cover unforeseen issues that may arise during the migration process. This is a crucial component to account for unexpected issues or delays.
Strategies for Optimizing Costs
Optimizing costs during and after rehosting involves implementing various strategies. These strategies aim to reduce expenses without compromising performance or security.
- Right-Sizing Resources: This involves selecting the appropriate cloud resources (e.g., compute instances, storage) based on the actual workload requirements. Over-provisioning leads to unnecessary costs, while under-provisioning can impact performance. Regularly monitoring resource utilization and adjusting resource allocation accordingly is critical.
- Leveraging Reserved Instances and Savings Plans: Cloud providers often offer discounts for committing to a specific level of resource usage over a period. Reserved instances and savings plans can significantly reduce compute costs, especially for workloads with predictable usage patterns.
- Automating Resource Management: Automating tasks such as scaling, patching, and backup/recovery can reduce operational overhead and associated costs. Infrastructure-as-code (IaC) tools can be used to automate the deployment and management of cloud resources.
- Optimizing Storage Costs: Different storage tiers offer varying costs based on access frequency. Data that is infrequently accessed can be moved to cheaper storage tiers, such as cold storage. Implementing data lifecycle policies can automate this process.
- Monitoring and Reporting: Regularly monitoring cloud resource usage and costs allows for identifying areas where optimization is possible. Cloud providers offer tools and services for cost monitoring and reporting. Analyzing these reports helps to identify cost-saving opportunities.
- Using Cloud-Native Services: Where possible, leveraging cloud-native services can reduce the need for managing infrastructure and associated costs. For example, using managed databases instead of self-managed databases can reduce operational overhead.
Cost-Saving Techniques and Impact
Implementing cost-saving techniques can significantly reduce the overall cost of rehosting. The impact of these techniques can be quantified through careful analysis.
- Example 1: Right-Sizing Virtual Machines
- Scenario: An organization is running virtual machines in the cloud that are consistently underutilized. By analyzing CPU and memory usage, the organization determines that the VMs are over-provisioned.
- Technique: Reduce the size of the VMs to match the actual workload requirements.
- Potential Impact: A 20% reduction in compute costs, leading to significant savings over time. This is based on real-world examples where companies have optimized VM sizes after migrating to the cloud.
- Example 2: Implementing Reserved Instances
- Scenario: An organization has predictable workloads that run continuously.
- Technique: Purchase reserved instances for these workloads.
- Potential Impact: Up to a 60% discount on compute costs compared to on-demand pricing, based on the specific cloud provider and instance type.
- Example 3: Utilizing Object Storage for Archival Data
- Scenario: An organization stores a large amount of infrequently accessed data.
- Technique: Move archival data to object storage, which is a cost-effective storage option for infrequently accessed data.
- Potential Impact: A significant reduction in storage costs, potentially by 80% or more, compared to using more expensive storage tiers, based on the volume of data and the chosen storage tier.
Security Implications of Rehosting
Rehosting, while simplifying the migration process, introduces new security considerations that must be carefully addressed. The cloud environment, with its inherent shared responsibility model, presents unique challenges compared to on-premises infrastructure. A thorough understanding of these implications and the implementation of robust security measures are critical to protecting rehosted workloads from threats. This section will delve into the specific security concerns associated with rehosting and Artikel best practices for maintaining a secure cloud environment.
Security Considerations in Rehosting
Migrating applications to the cloud necessitates a reassessment of security controls and practices. The cloud’s distributed nature and reliance on third-party providers introduce new attack vectors and potential vulnerabilities. Understanding these considerations is the first step in securing rehosted workloads.The shared responsibility model is a core concept. The cloud provider is responsible for the security
- of* the cloud, while the customer is responsible for the security
- in* the cloud. This means the customer bears the responsibility for securing their data, applications, and access. Failure to adequately address these responsibilities can lead to data breaches, service disruptions, and regulatory non-compliance.
Data security is a paramount concern. Data residing in the cloud must be protected from unauthorized access, modification, and disclosure. This involves implementing encryption, access controls, and robust data loss prevention (DLP) strategies. The location of data storage and compliance with relevant data privacy regulations, such as GDPR or HIPAA, must also be considered.Identity and access management (IAM) is crucial.
Controlling who has access to cloud resources and what they can do is essential for preventing unauthorized activity. This involves implementing strong authentication mechanisms, role-based access control (RBAC), and regularly reviewing user permissions.Network security is also vital. Cloud networks must be protected from external threats such as denial-of-service (DoS) attacks, malware, and unauthorized access. This requires implementing firewalls, intrusion detection and prevention systems (IDS/IPS), and network segmentation.
Security Best Practices for Rehosted Workloads
Adopting security best practices is essential for mitigating the risks associated with rehosting. These practices encompass a range of measures, from proactive security assessments to ongoing monitoring and incident response. Implementing these practices strengthens the security posture of rehosted applications.Regular security assessments should be performed. These assessments should identify vulnerabilities and misconfigurations in the cloud environment and application code. Penetration testing, vulnerability scanning, and code reviews should be conducted to identify and address potential weaknesses.Implementing robust access controls is critical.
Employing the principle of least privilege, which grants users only the necessary access to perform their tasks, minimizes the impact of potential security breaches. Multi-factor authentication (MFA) should be implemented for all user accounts to prevent unauthorized access.Data encryption should be applied. Data should be encrypted both in transit and at rest. This protects sensitive information from unauthorized access, even if the underlying infrastructure is compromised.
Encryption keys should be securely managed and rotated regularly.Continuous monitoring and logging are essential. Implementing comprehensive monitoring and logging capabilities enables the detection of security incidents and allows for timely response. Security information and event management (SIEM) systems can be used to collect, analyze, and correlate security events from various sources.Incident response plans should be developed. Having a well-defined incident response plan ensures that security incidents are handled effectively and efficiently.
The plan should Artikel the steps to be taken in the event of a security breach, including containment, eradication, recovery, and post-incident analysis.
Security Recommendations for Rehosting
The following recommendations provide a detailed guide to securing rehosted workloads. Each point emphasizes a specific aspect of security and offers practical guidance for implementation.
- Assess Existing Security Posture: Before migrating, thoroughly assess the existing security controls and vulnerabilities of the on-premises applications. This assessment should include vulnerability scanning, penetration testing, and security audits. Document all existing security measures and identify gaps that need to be addressed in the cloud environment.
- Choose a Secure Cloud Provider: Select a cloud provider that offers robust security features and complies with relevant industry standards and regulations. Evaluate the provider’s security certifications (e.g., ISO 27001, SOC 2) and its security incident response capabilities. Research their history of security breaches and assess their commitment to security best practices.
- Implement Strong Identity and Access Management (IAM): Utilize the cloud provider’s IAM services to manage user identities, roles, and permissions. Enforce the principle of least privilege, granting users only the minimum necessary access. Implement multi-factor authentication (MFA) for all user accounts, especially those with administrative privileges. Regularly review and audit user access permissions.
- Secure Network Configuration: Configure virtual networks (VPCs) with proper segmentation to isolate workloads and restrict network traffic. Implement firewalls, intrusion detection and prevention systems (IDS/IPS), and web application firewalls (WAFs) to protect against network-based attacks. Regularly monitor network traffic for suspicious activity.
- Encrypt Data at Rest and in Transit: Encrypt sensitive data both when it’s stored (at rest) and when it’s being transmitted (in transit). Utilize encryption keys managed by the cloud provider’s key management service (KMS) or a third-party KMS. Ensure data encryption adheres to industry standards (e.g., AES-256).
- Implement Data Loss Prevention (DLP) Strategies: Implement DLP measures to prevent sensitive data from leaving the cloud environment. This can include data classification, data masking, and access control policies. Regularly monitor data movement and access patterns.
- Enable Comprehensive Logging and Monitoring: Enable detailed logging for all cloud resources and applications. Utilize a SIEM solution to collect, analyze, and correlate security events. Implement real-time monitoring and alerting for suspicious activity. Regularly review and analyze security logs.
- Establish a Robust Incident Response Plan: Develop a comprehensive incident response plan that Artikels the steps to be taken in the event of a security breach. The plan should include procedures for detection, containment, eradication, recovery, and post-incident analysis. Regularly test and update the incident response plan.
- Automate Security Processes: Automate security tasks such as vulnerability scanning, patch management, and configuration management. This reduces the risk of human error and ensures consistent security practices. Utilize infrastructure-as-code (IaC) tools to automate security configurations.
- Train and Educate Staff: Provide security training to all staff members who will be working with the rehosted applications. This training should cover cloud security best practices, threat awareness, and incident response procedures. Regularly update the training to reflect changes in the threat landscape.
Case Studies
Successful rehosting implementations offer valuable insights into the practical application of this cloud migration strategy. Examining real-world examples across diverse industries reveals the challenges, solutions, and benefits associated with rehosting. These case studies illustrate the strategic considerations and technical approaches that contribute to a successful lift-and-shift migration.
Successful Rehosting Examples Across Different Industries
Rehosting has been adopted across various sectors, each presenting unique challenges and requiring tailored solutions. The following examples highlight successful rehosting implementations in different industries:
- Healthcare: A large healthcare provider migrated its on-premises electronic health record (EHR) system to the cloud using a rehosting strategy. This involved migrating virtual machines (VMs) running the EHR software, along with the associated databases, to a cloud infrastructure-as-a-service (IaaS) platform. The primary goal was to improve system scalability, disaster recovery capabilities, and reduce on-premises infrastructure costs. The challenges included ensuring data security and compliance with healthcare regulations (HIPAA).
The solution involved implementing robust security measures, including data encryption, access controls, and regular security audits. The rehosting significantly improved system uptime and reduced operational costs.
- Retail: A major retail company rehosted its e-commerce platform to the cloud. The existing platform, hosted on physical servers, faced challenges in handling peak traffic during seasonal sales events. The rehosting project involved migrating the e-commerce application, databases, and related components to a cloud environment. The company aimed to improve platform performance, scalability, and cost efficiency. The solution included optimizing database performance, implementing auto-scaling for web servers, and leveraging cloud-based content delivery networks (CDNs).
The rehosting resulted in improved website performance, reduced infrastructure costs, and enhanced scalability to handle peak traffic loads.
- Financial Services: A financial institution migrated its legacy core banking system to the cloud using a rehosting approach. The goal was to modernize the IT infrastructure, improve business agility, and reduce operational expenses. The project involved migrating the core banking application, databases, and related services to a cloud environment. The primary challenges were ensuring data security, regulatory compliance (e.g., GDPR, CCPA), and minimizing downtime during the migration process.
The solution involved implementing advanced security measures, including multi-factor authentication, data encryption, and intrusion detection systems. The migration was executed in phases to minimize disruption to banking services. The rehosting resulted in improved system performance, enhanced security, and significant cost savings.
- Manufacturing: A manufacturing company rehosted its enterprise resource planning (ERP) system to the cloud. The company aimed to reduce the complexity of managing on-premises infrastructure, improve system performance, and enhance business continuity. The rehosting project involved migrating the ERP application, databases, and related components to a cloud environment. The key challenges included ensuring data integrity during the migration and minimizing downtime.
The solution involved using specialized migration tools, performing thorough testing, and implementing a phased migration approach. The rehosting resulted in improved system performance, enhanced data security, and reduced operational costs.
Details About the Challenges Faced and the Solutions Implemented
Each rehosting project faces unique challenges related to the specific applications, infrastructure, and industry regulations. Understanding these challenges and the solutions implemented is crucial for successful migration.
- Compatibility Issues: Legacy applications may have compatibility issues with the target cloud environment. This can involve issues with operating systems, software dependencies, or hardware configurations. Solutions involve application refactoring, testing and validation in the target cloud environment, or using compatibility tools.
- Data Migration Complexity: Migrating large databases and complex data structures can be challenging. This can involve data transformation, data integrity checks, and minimizing downtime during the migration. Solutions include using specialized data migration tools, performing thorough testing, and implementing a phased migration approach.
- Security and Compliance: Ensuring data security and compliance with industry regulations (e.g., HIPAA, GDPR, PCI DSS) is a critical concern. This requires implementing robust security measures, including data encryption, access controls, and regular security audits. Solutions involve implementing security best practices, using cloud-native security features, and engaging with compliance experts.
- Network Configuration: Configuring the network in the cloud environment to match the existing on-premises network can be complex. This involves configuring virtual networks, firewalls, and VPN connections. Solutions involve careful network planning, using cloud-native networking services, and testing the network configuration thoroughly.
- Performance Optimization: Optimizing application performance in the cloud environment may require adjustments to the application configuration and infrastructure. Solutions involve optimizing database performance, implementing auto-scaling, and using cloud-based content delivery networks (CDNs).
Summary of a Case Study, Highlighting Key Takeaways
Case Study: A global insurance company migrated its core policy administration system to the cloud using a rehosting approach. The system, running on a complex on-premises infrastructure, was facing challenges related to scalability, performance, and disaster recovery. The primary goals were to improve system performance, reduce infrastructure costs, and enhance business continuity.
Challenges: Data migration complexity, ensuring data security and compliance, and minimizing downtime during the migration.Solutions: Utilizing specialized data migration tools, implementing robust security measures including encryption and access controls, and executing the migration in phases to minimize disruption.
Key Takeaways: Successful rehosting requires careful planning, thorough testing, and a phased migration approach. Data security and compliance are paramount. Leveraging cloud-native services can optimize performance and reduce costs.The project resulted in a 30% reduction in infrastructure costs, a 40% improvement in system performance, and enhanced disaster recovery capabilities.
Future Trends and the Evolution of Rehosting
The landscape of cloud migration is dynamic, with rehosting (lift and shift) evolving alongside advancements in cloud technology, automation, and the broader digital transformation initiatives. This evolution is driven by the need for greater agility, cost optimization, and enhanced security in managing IT infrastructure. The future of rehosting is not a static concept but a continuous adaptation to emerging trends and technologies.
Automation and Orchestration Advancements
The increasing reliance on automation and orchestration is transforming the rehosting process. These technologies streamline and accelerate migrations, reducing manual effort and minimizing human error.
- Automated Assessment and Planning: Sophisticated tools will automatically assess on-premises environments, generating detailed migration plans, including resource requirements and potential compatibility issues. This will involve machine learning algorithms analyzing application dependencies and recommending optimal cloud configurations.
- Automated Code Transformation: While rehosting primarily involves minimal code changes, automated tools will evolve to handle minor code adjustments required for cloud compatibility. This may involve automatically updating configuration files or adapting scripts to work with cloud-native services.
- Orchestrated Deployment and Management: Orchestration platforms will manage the deployment and ongoing operation of migrated applications in the cloud. This includes automated scaling, load balancing, and self-healing capabilities, ensuring high availability and performance. Tools like Kubernetes are already playing a key role and will become even more critical.
Integration with Cloud-Native Services
Rehosting will increasingly integrate with cloud-native services to leverage their capabilities and optimize application performance and cost.
- Hybrid Cloud Integration: Rehosting will become a bridge to hybrid cloud environments, where some applications remain on-premises while others are migrated to the cloud. This will require seamless integration and data synchronization between the two environments.
- Use of Serverless Computing: Applications rehosted can be refactored to utilize serverless functions for specific tasks, reducing infrastructure management overhead and improving scalability.
- Leveraging Managed Services: Migrated applications will increasingly leverage managed services such as databases, message queues, and object storage offered by cloud providers. This reduces operational complexity and improves efficiency.
Focus on Security and Compliance
Security and compliance will remain paramount in the future of rehosting. The evolving threat landscape and stringent regulatory requirements will necessitate advanced security measures.
- Automated Security Assessments: Tools will automatically assess the security posture of migrated applications, identifying vulnerabilities and recommending remediation strategies.
- Enhanced Security Monitoring: Advanced monitoring solutions will provide real-time visibility into application behavior, detecting and responding to security threats.
- Compliance Automation: Automation tools will streamline compliance with industry regulations and standards, such as GDPR, HIPAA, and PCI DSS. This includes automated policy enforcement and audit logging.
Evolution of Rehosting Methodologies
Rehosting methodologies will evolve to address specific use cases and application characteristics.
- Partial Rehosting: This involves migrating only specific components of an application to the cloud, leaving others on-premises. This approach is suitable for applications with complex dependencies or those requiring specific on-premises resources.
- Containerization and Orchestration: Containerization technologies like Docker and orchestration platforms like Kubernetes will become increasingly important in rehosting. Containerizing applications allows for easier portability and management in the cloud.
- Replatforming and Refactoring with Rehosting: While rehosting is primarily a “lift and shift” approach, it will be increasingly combined with replatforming and refactoring to optimize application performance and leverage cloud-native features. This hybrid approach allows for incremental modernization.
Impact of Emerging Cloud Technologies
Emerging cloud technologies will significantly influence the future of rehosting.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML will be used to automate migration processes, optimize resource allocation, and improve application performance in the cloud.
- Edge Computing: As edge computing becomes more prevalent, rehosting strategies will need to accommodate applications deployed at the edge. This includes considerations for data locality, low latency, and limited bandwidth.
- Quantum Computing: While quantum computing is still in its early stages, rehosting strategies may need to consider the potential impact of quantum computing on application performance and security in the future.
Summary
In conclusion, rehosting presents a powerful strategy for initiating cloud migration, offering a rapid route to the cloud with minimal disruption. While challenges such as compatibility and performance must be carefully considered, the benefits in terms of speed, efficiency, and cost savings are significant. As cloud technologies continue to advance, rehosting will evolve, adapting to new paradigms and providing businesses with an adaptable approach to harness the full potential of the cloud.
By understanding the nuances of rehosting, organizations can make informed decisions and embark on a successful cloud journey, driving innovation and achieving strategic goals.
Common Queries
What is the primary advantage of rehosting?
The primary advantage is the speed and simplicity of migrating applications to the cloud with minimal code changes, resulting in faster time-to-market.
What are the potential downsides of rehosting?
Potential downsides include potential compatibility issues, performance challenges if the underlying infrastructure is not optimized, and limited opportunities for application modernization.
Is rehosting suitable for all types of applications?
Rehosting is most suitable for applications that are relatively straightforward, monolithic, and where minimal downtime is crucial. Applications requiring significant architectural changes might benefit more from refactoring.
How does rehosting differ from refactoring?
Rehosting involves minimal code changes, simply moving the application. Refactoring involves making significant changes to the application’s code and architecture to optimize it for the cloud.
What are the cost considerations in rehosting?
Cost considerations include the cloud infrastructure costs, potential licensing costs, and the cost of migration tools and services. Optimization strategies can help manage these costs effectively.