Delving into the realm of Kubernetes security, we explore the intricacies of Pod Security Policies (PSPs). These policies are pivotal in fortifying your Kubernetes clusters, offering a robust layer of defense for your containerized applications. PSPs act as gatekeepers, dictating the security parameters under which pods can operate, ensuring a consistent and secure environment across your deployments.
This exploration will illuminate the fundamental purpose of PSPs, their key components, and how they control pod creation. We’ll examine the critical attributes that define a PSP’s behavior, like `privileged`, `runAsUser`, and `volumes`, along with the security contexts they enforce. Furthermore, we’ll discuss best practices for implementation, troubleshooting common issues, and the transition to newer security mechanisms.
Introduction to Kubernetes Pod Security Policy (PSP)
Kubernetes Pod Security Policies (PSPs) are a crucial mechanism for enforcing security best practices within a Kubernetes cluster. They provide a means to control the security context of pods, thereby limiting the potential impact of security breaches and enhancing the overall security posture of the cluster. PSPs are designed to be flexible and allow administrators to define a range of security constraints.
Fundamental Purpose of a PSP
The fundamental purpose of a Pod Security Policy is to control the security settings of pods. This control is achieved by defining a set of rules that pods must adhere to in order to be scheduled on a node. If a pod definition violates the constraints specified in the applied PSP, the pod will not be created.
Definition of a PSP
A Pod Security Policy (PSP) is a cluster-level resource that defines a set of permissions and restrictions that pods must abide by to be accepted by the Kubernetes API server. PSPs act as admission controllers, evaluating pod specifications against defined rules. The policies encompass various security aspects, including privileged execution, user and group IDs, volume types, and more.
Core Goals of PSPs Regarding Pod Security
PSPs aim to achieve several core goals related to pod security:
- Reduce the Attack Surface: PSPs limit the capabilities available to pods, thereby reducing the potential attack surface. By restricting privileged access and the use of sensitive features, PSPs minimize the impact of a compromised pod.
- Enforce Security Best Practices: PSPs allow administrators to enforce security best practices across the cluster. This ensures consistency in security configurations and prevents pods from being deployed with insecure settings.
- Enhance Isolation: PSPs promote pod isolation by controlling resource access and security contexts. This isolation helps to prevent pods from interfering with each other or accessing sensitive information.
- Improve Compliance: PSPs can be used to meet compliance requirements by enforcing specific security configurations. They provide a mechanism to ensure that pods adhere to security standards and regulations.
- Prevent Privilege Escalation: PSPs prevent privilege escalation by controlling the user and group IDs under which pods run, and by preventing the use of capabilities that could allow a pod to gain more privileges than necessary. For example, a PSP can restrict the `NET_ADMIN` capability, preventing pods from modifying network configurations.
Key Components and Attributes of a PSP
Kubernetes Pod Security Policies (PSPs) are defined by a set of attributes that control the security context of pods. These attributes dictate the permissions and capabilities a pod has, thereby limiting its potential impact if compromised. Understanding these attributes is crucial for securing a Kubernetes cluster. The attributes cover aspects such as user and group IDs, volume types, and the ability to run privileged containers.
Privileged Attribute
The `privileged` attribute determines whether a pod can run containers with elevated privileges. This essentially grants the container almost unrestricted access to the host machine’s resources. Enabling this can be risky.The `privileged` attribute, when set to `true`, allows a container to have the same access as processes running directly on the host. This includes the ability to access and modify the host’s kernel, devices, and network configuration.
This level of access presents a significant security risk because a compromised container with privileged access could potentially compromise the entire host.
RunAsUser Attribute
The `runAsUser` attribute controls the user ID under which the container processes run. This attribute is critical for defining the user context within the container. It allows you to specify the user ID, and it can also enforce the use of a specific user or prevent running as a root user.Setting `runAsUser` effectively restricts the user ID under which processes inside the container execute.
This helps to reduce the attack surface. For example, if a pod runs as a non-root user, an attacker who gains access to the pod will be limited in what they can do. The `runAsUser` attribute can take several forms:
- MustRunAs: Requires the pod to run as a specific user ID.
- MustRunAsNonRoot: Enforces that the pod cannot run as the root user (UID 0).
- RunAsUser: Specifies a range of acceptable user IDs.
Volumes Attribute
The `volumes` attribute defines which volume types a pod is allowed to use. Restricting volume types helps to limit the potential for privilege escalation and access to sensitive data.The `volumes` attribute provides control over the types of volumes that pods can mount. This attribute is essential for preventing unauthorized access to host resources or sensitive data. For example, if a PSP denies the use of `hostPath` volumes, a pod cannot mount directories from the host’s filesystem.
Security Contexts Enforced by PSPs
PSPs enforce various security contexts on pods, covering aspects such as user and group IDs, the use of privileged containers, and volume access. These contexts work together to create a layered security approach.The security contexts enforced by PSPs are multifaceted, impacting how pods interact with the underlying infrastructure. They are applied at the pod level, ensuring that the containers within a pod adhere to the defined security constraints.
- User and Group IDs: Controlling the user and group IDs under which containers run, preventing them from running as root or accessing sensitive host resources.
- Privileged Container Restrictions: Preventing pods from running containers with elevated privileges, limiting the potential damage from compromised containers.
- Volume Type Restrictions: Restricting the types of volumes a pod can mount, limiting access to host resources or sensitive data.
- Capabilities: Controlling the Linux capabilities granted to containers, such as the ability to mount filesystems or perform network configuration.
Comparison of PSP Attributes
The following table provides a comparison of key PSP attributes, including their descriptions, examples, and potential impact.
| Attribute Name | Description | Example | Impact |
|---|---|---|---|
privileged | Determines whether a pod can run containers with elevated privileges. | privileged: false | Restricts the container’s access to the host’s resources, reducing the risk of compromise. |
runAsUser | Specifies the user ID under which the container processes run. | runAsUser: | Prevents the container from running as root, limiting the damage an attacker can do. |
volumes | Defines the volume types a pod is allowed to use. | volumes: | Restricts access to host resources and sensitive data by limiting the types of volumes that can be mounted. |
allowedCapabilities | Defines the Linux capabilities allowed for the container. | allowedCapabilities: | Grants specific permissions to the container, enabling fine-grained control over its behavior. |
How PSPs Control Pod Creation
Pod Security Policies (PSPs) play a crucial role in enforcing security best practices within a Kubernetes cluster by controlling the creation of pods. They act as admission controllers, intercepting pod creation requests and validating them against a set of predefined rules. This validation process ensures that pods adhere to the security requirements specified in the PSP, preventing the deployment of potentially insecure configurations.
Validating Pod Specifications
PSPs meticulously scrutinize pod specifications during the creation process. This validation involves checking various aspects of the pod configuration against the policy’s defined constraints. If a pod specification violates any of these constraints, the pod creation request is rejected, and an error message is returned. This mechanism helps to prevent the deployment of pods that could potentially compromise the security posture of the cluster.The validation process encompasses numerous checks, including:
- User and Group IDs: Ensures the pod runs with the specified user and group IDs, preventing privilege escalation.
- Privileged Containers: Controls whether a pod can run privileged containers, which have access to the host’s resources.
- Capabilities: Limits the capabilities granted to the container, such as the ability to mount filesystems or access network interfaces.
- Host Network and Ports: Restricts the pod’s access to the host’s network and ports.
- Volume Types: Determines the types of volumes the pod can mount, such as host paths or persistent volumes.
- SELinux Options: Configures the SELinux context for the pod, enhancing security.
- AppArmor Profiles: Specifies the AppArmor profile to be applied to the pod’s containers, further restricting their capabilities.
Applying a PSP to a Namespace
Applying a PSP to a namespace is essential to activate its security enforcement. This process involves associating the PSP with a service account that the pods will use. The pods created in the namespace must then use this service account to be subject to the PSP’s rules. This mechanism ensures that the policy applies to the desired scope and does not affect other namespaces that may have different security requirements.The process of applying a PSP involves these key steps:
- Create a PSP: Define the security constraints in a YAML file, specifying the desired restrictions on pod creation.
- Create a Service Account (if necessary): If pods don’t already use one, create a service account for the namespace.
- Create a Role: Define a Role that grants the service account permission to use the PSP. The Role binds the use of the PSP to a specific resource (e.g., the namespace).
- Create a RoleBinding: Create a RoleBinding to bind the Role to the service account. This grants the service account the permissions defined in the Role.
- Deploy Pods: Deploy pods in the namespace, ensuring they use the service account created in the previous steps.
For example, consider a scenario where a PSP named `restricted-psp` is created, disallowing privileged containers. To apply this policy to a namespace called `production`, the following steps would be taken:
- Create the PSP: A YAML file defines the `restricted-psp` and sets the `privileged` field to `false`.
- Create a Service Account: A service account named `production-sa` is created in the `production` namespace.
- Create a Role: A Role named `psp-use-role` is created in the `production` namespace. This role grants permission to use the `restricted-psp`.
- Create a RoleBinding: A RoleBinding named `psp-use-rolebinding` is created in the `production` namespace. This RoleBinding binds the `psp-use-role` to the `production-sa` service account.
- Deploy Pods: When deploying pods in the `production` namespace, specify `production-sa` as the `serviceAccountName`. If a pod definition attempts to use a privileged container, the admission controller will reject the pod creation request.
Understanding the `privileged` Attribute
The `privileged` attribute within a Kubernetes Pod Security Policy (PSP) offers a significant degree of control over a pod’s access to the host system. It’s a crucial aspect of pod security, but it also introduces considerable risks if misused. This section delves into the implications of using `privileged`, provides illustrative scenarios, and Artikels a cautionary approach.
Impact of the `privileged` Attribute on Pod Security
The `privileged` attribute, when set to `true`, grants a pod the same level of access to the host machine as processes running directly on the host. This means the pod can perform operations that typically require root privileges, potentially bypassing security restrictions imposed by the Kubernetes cluster.
- Bypassing Security Measures: A privileged pod can access and modify any part of the host’s file system, network configuration, and device drivers. This bypasses many of the security controls designed to isolate pods from the underlying infrastructure.
- Security Vulnerabilities: If a privileged pod is compromised, an attacker gains complete control over the host node. This can lead to data breaches, denial-of-service attacks, and lateral movement within the cluster and potentially to other connected systems.
- Increased Attack Surface: The use of `privileged` significantly expands the attack surface. Any vulnerability in the pod’s container image, or in the applications running within the pod, can be exploited to compromise the entire host.
- Difficult Auditing: Activities within a privileged pod are harder to audit because they can bypass standard logging and monitoring mechanisms. This makes it difficult to detect and respond to security incidents.
Scenarios Where Using `privileged` Might Be Necessary and the Associated Risks
There are limited, legitimate use cases for the `privileged` attribute. However, even in these scenarios, the risks must be carefully considered and mitigated.
- Infrastructure Management: Certain infrastructure components, such as network plugins or storage drivers, may require privileged access to configure the host’s network interfaces or manage storage devices.
- Container Runtime Daemons: Running container runtime daemons (like Docker itself, for specific operations) within a pod may necessitate privileged access.
- Debugging and Troubleshooting: In specific situations, for example, advanced debugging of network issues, a privileged pod may be used to access network namespaces or inspect host resources.
Associated Risks:
Even in these legitimate scenarios, the risks associated with using `privileged` are substantial:
- Escalation of Privileges: A vulnerability in the pod’s application can allow an attacker to escalate their privileges and gain full control over the host.
- Container Escape: A compromised container can potentially “escape” its isolation and access the host, leading to data theft or system compromise.
- Misconfiguration: Incorrectly configured privileged pods can lead to security vulnerabilities, such as unauthorized access to sensitive data or denial-of-service attacks.
Warning Message for Pod Creation with `privileged` Set to True
To mitigate the risks, a clear and concise warning message should be displayed when a user attempts to create a pod with the `privileged` attribute set to `true`. This message serves as a crucial reminder of the security implications.
Here is an example of a warning message:
WARNING: The `privileged` attribute is set to `true`. This grants the pod full access to the host’s resources, potentially bypassing security restrictions. Use with extreme caution. Consider alternatives such as specific capabilities or hostPath volumes. Review your Pod Security Policy configuration and the implications before proceeding.
This warning message should be displayed prominently during pod creation attempts, perhaps integrated into the Kubernetes API server’s response or within a custom admission controller. The warning should also include information on alternatives to the `privileged` attribute, such as using specific capabilities (e.g., `CAP_NET_ADMIN`), hostPath volumes (for limited host file system access), or more restrictive Pod Security Policies. This encourages users to explore less privileged options and minimize the security risks.
Controlling User and Group IDs with PSPs
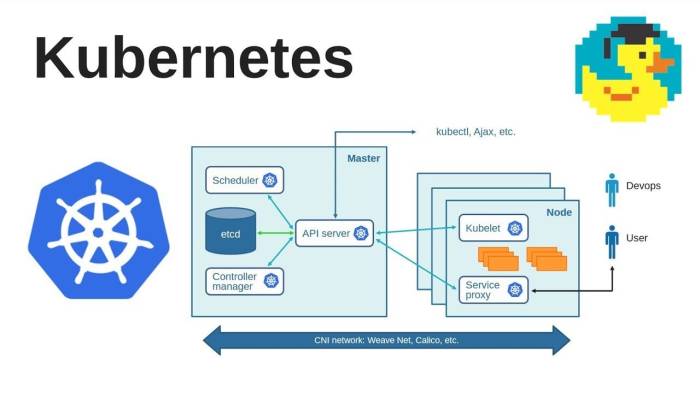
Pod Security Policies (PSPs) provide granular control over the security context of pods, including the user and group IDs under which they run. This capability is crucial for enhancing security by restricting the privileges a pod possesses, thereby limiting the potential impact of security breaches. By carefully configuring user and group ID settings within a PSP, administrators can significantly reduce the attack surface and improve the overall security posture of their Kubernetes clusters.
Configuring User and Group IDs with PSPs
PSPs allow administrators to define the user and group IDs that a pod is permitted to run as. This is achieved through the `runAsUser` and `runAsGroup` attributes within the PSP definition. These attributes offer various options to specify the permitted user and group IDs, enabling administrators to enforce strict security policies.
- `runAsUser`: This attribute controls the user ID that the container process will run as.
- `runAsGroup`: This attribute controls the group ID that the container process will run as.
The `runAsUser` and `runAsGroup` attributes can be configured using different strategies:
- `MustRunAs`: Specifies a fixed user ID or group ID that the pod must run as.
- `RunAsAny`: Allows the pod to run as any user ID or group ID. This is the least restrictive option.
- `MustRunAsNonRoot`: Enforces that the pod runs as a non-root user (UID greater than 0).
- `RunAsUserStrategy`: Enables custom strategies. It can be `RunAsAny`, `MustRunAs`, `MustRunAsNonRoot`.
- `RunAsGroupStrategy`: Similar to `RunAsUserStrategy`, it enables custom strategies. It can be `RunAsAny`, `MustRunAs`.
Here are some examples of how to configure `runAsUser` and `runAsGroup` within a PSP:
apiVersion: policy/v1beta1kind: PodSecurityPolicymetadata: name: restricted-pspspec: runAsUser: rule: MustRunAs ranges: -min: 1000 max: 1000 runAsGroup: rule: MustRunAs ranges: -min: 2000 max: 2000 fsGroup: rule: RunAsAny seLinux: rule: RunAsAny volumes: -'*' allowedCapabilities: -'*' privileged: false
In this example, the `restricted-psp` requires pods to run as user ID 1000 and group ID 2000.
The `fsGroup` and `seLinux` are set to `RunAsAny`, allowing for flexibility in those areas while still enforcing strict user and group ID controls. This configuration significantly reduces the risk associated with privilege escalation within the cluster.
User ID Validation Process
The process of user ID validation by a PSP involves several steps to ensure that pods adhere to the defined security policies. This process is crucial for maintaining the security and integrity of the Kubernetes cluster.
The flowchart below illustrates the process of user ID validation by a PSP.
Flowchart Description:
The flowchart starts with the creation of a pod. The pod’s security context is then evaluated against the active PSPs. The PSPs are checked for user ID restrictions (runAsUser). The validation checks the specified rule for `runAsUser`. If the pod violates the rule, the pod creation is rejected.
If the pod complies with the rule, the pod creation is allowed. This process ensures that only pods that meet the security requirements are permitted to run.
Volume Restrictions and PSPs
Pod Security Policies (PSPs) offer a crucial mechanism for controlling the types of volumes a pod can utilize within a Kubernetes cluster. This control is essential for maintaining the security and integrity of the cluster’s resources. Restricting volume types mitigates the risk of malicious actors exploiting vulnerabilities associated with specific volume plugins.
Role of PSPs in Restricting Volume Types
PSPs play a vital role in defining which volume types are permitted for use by pods. This is achieved through the `volumes` field within a PSP. This field allows administrators to specify a whitelist of allowed volume types, effectively preventing pods from using unauthorized or potentially dangerous volume plugins. This restriction is applied at the pod creation stage, ensuring that any pod attempting to utilize a disallowed volume type will fail to launch.
Security Implications of Allowing Certain Volume Types
Allowing certain volume types can introduce significant security risks. For example, the `hostPath` volume type, which allows pods to access files and directories on the host node’s filesystem, is particularly dangerous.
- HostPath: If a pod is granted access to the host filesystem via `hostPath`, a compromised pod could potentially read, write, or execute files on the host, leading to privilege escalation or data exfiltration. This poses a severe threat to the entire cluster.
- NFS, GlusterFS, and other network-based volumes: Incorrectly configured access to these volumes could expose sensitive data or allow unauthorized access to the network resources.
- FlexVolume: While FlexVolumes offer flexibility, they require careful configuration and can introduce vulnerabilities if the underlying scripts are not properly secured.
Therefore, it’s crucial to carefully evaluate the security implications of each volume type and only allow those that are absolutely necessary.
Configuring a PSP to Allow Specific Volume Types
Configuring a PSP to restrict volume types involves specifying the allowed volume types in the `volumes` field. This field accepts a list of allowed volume types. If a pod attempts to use a volume type not in this list, the pod creation will be rejected. Let’s examine examples for `emptyDir`, `configMap`, and `secret`.
Before proceeding with examples, it’s important to note the general structure of the `volumes` field in a PSP definition:
volumes:'*' # Allows all volumes (default if not specified)
- emptyDir - configMap - secret # ... other allowed volume types
In the examples below, assume a minimal PSP definition with the necessary `apiVersion`, `kind`, and `metadata` fields already defined.
- Allowing `emptyDir` Volumes:
To allow pods to use `emptyDir` volumes, the `volumes` field should include `emptyDir` in its allowed list. `emptyDir` volumes provide a temporary directory that shares the pod’s lifecycle; data within is lost when the pod is removed. This is generally a safe volume type.
volumes:-emptyDir - Allowing `configMap` Volumes:
To allow pods to use `configMap` volumes, you must include `configMap` in the `volumes` list. `configMap` volumes mount ConfigMap resources as files or directories within the pod, providing a mechanism for injecting configuration data.
volumes:-configMap - Allowing `secret` Volumes:
To allow pods to use `secret` volumes, include `secret` in the `volumes` list. `secret` volumes mount Secret resources as files or directories, providing a secure way to inject sensitive information such as passwords, API keys, and TLS certificates into pods. It is important to control which secrets a pod is permitted to access through the PSP.
volumes:-secret By combining these individual volume type specifications, administrators can create highly customized PSPs that allow only the required volume types, thus minimizing the attack surface and enhancing cluster security. For instance, a PSP could allow only `emptyDir`, `configMap`, and `secret` volumes, disallowing potentially dangerous types like `hostPath` altogether.
Network Policies and PSPs Interaction

Pod Security Policies (PSPs) and Network Policies are both crucial components of Kubernetes security, but they address different aspects of pod security. PSPs focus on the capabilities and resource access of a pod itself, while Network Policies govern the communication
- to* and
- from* pods. Understanding their interaction is vital for a robust security posture.
Relationship Between PSPs and Network Policies
PSPs and Network Policies work in tandem to provide comprehensive security. PSPs restrict what a pod
- can do* within the cluster, while Network Policies control
- how* a pod can communicate with other pods and external services. This layered approach creates a defense-in-depth strategy. PSPs act as the first line of defense, limiting the potential damage a compromised pod can inflict. Network Policies then restrict the pod’s network reach, further mitigating the impact of a security breach.
Scenario: PSP and Network Policy Interaction
Consider a scenario where a PSP restricts a pod from running with the `NET_ADMIN` capability, preventing it from modifying network interfaces. Simultaneously, a Network Policy limits the pod’s outbound traffic to only a specific set of IP addresses and ports, perhaps for accessing a database.In this scenario:
- The PSP prevents the pod from manipulating network configurations, reducing the risk of network-based attacks.
- The Network Policy ensures the pod can only communicate with the permitted database, preventing it from connecting to other potentially malicious services or exfiltrating data.
This combination significantly strengthens security by limiting both the pod’s internal capabilities and its external network access.
Configuring Network Policies in Conjunction with PSPs
Configuring Network Policies alongside PSPs requires careful planning and implementation to achieve a defense-in-depth strategy. The following steps provide guidance:
- Define PSPs: Start by defining PSPs that enforce least privilege principles. Restrict capabilities, user IDs, and volume access based on the pod’s function. For example, a PSP for a web server pod might disallow privileged containers and restrict the user ID.
- Create Network Policies: Define Network Policies that specify the allowed network traffic for each pod or group of pods. Use selectors to target specific pods. For instance, a Network Policy might allow web server pods to receive traffic on port 80 and 443 from external sources and to connect to a database pod on a specific port.
- Test and Validate: Thoroughly test the PSPs and Network Policies to ensure they function as expected. Verify that pods cannot perform unauthorized actions and that network traffic is restricted according to the defined policies. Use tools like `kubectl exec` to test network connectivity and examine pod logs for any policy violations.
- Iterate and Refine: Regularly review and update the PSPs and Network Policies as the application and infrastructure evolve. Adjust the policies based on security audits, vulnerability assessments, and changes in the application’s requirements.
This layered approach ensures a more secure and resilient Kubernetes environment.
Best Practices for PSP Implementation
Implementing Pod Security Policies (PSPs) effectively is crucial for maintaining a secure and compliant Kubernetes environment. Following established best practices ensures that PSPs provide the intended level of protection without disrupting application deployments or operational workflows. This section details key considerations for creating, managing, testing, and auditing PSP configurations.
Creating PSPs: A Principle of Least Privilege Approach
The cornerstone of secure PSP implementation is the principle of least privilege. This means granting only the minimum necessary permissions required for a pod to function. This approach minimizes the potential attack surface and limits the impact of any security breaches.
- Start with a Deny-All Policy: Begin by creating a PSP that denies all pod creation requests. This forces explicit permission grants and prevents accidental deployment of pods with excessive privileges.
- Gradually Relax Restrictions: Incrementally relax the restrictions of the deny-all policy based on the specific needs of your applications. This iterative approach allows for controlled testing and validation.
- Define Specific Roles: Instead of creating broad PSPs, define PSPs for specific roles or application types. This granularity simplifies management and improves security posture.
- Leverage Labels and Selectors: Utilize labels and selectors to associate PSPs with specific namespaces or pods. This enables targeted enforcement and reduces the risk of applying overly permissive policies.
- Document Policies: Clearly document each PSP, including its purpose, the rationale behind its configurations, and the applications or users it applies to. This documentation aids in understanding, troubleshooting, and future modifications.
Testing and Validating PSP Configurations
Thorough testing is essential to ensure that PSPs function as intended and do not inadvertently block legitimate pod deployments. Testing should be conducted in a non-production environment before applying PSPs to production clusters.
- Develop Test Cases: Create a comprehensive set of test cases that cover various pod configurations, including different user IDs, group IDs, volume types, and network policies.
- Use a Dedicated Testing Namespace: Deploy test pods within a dedicated testing namespace that mirrors the structure and configurations of your production namespaces.
- Validate Pod Creation: Verify that pods with permitted configurations are successfully created and that pods with denied configurations are rejected, with clear error messages.
- Simulate Real-World Scenarios: Test scenarios that mimic real-world deployments, including updates, rollbacks, and scaling operations.
- Monitor Logs: Regularly monitor the Kubernetes audit logs for PSP-related events to identify any unexpected behavior or policy violations.
- Utilize Tools: Consider using tools like `kubectl dry-run` or policy validation tools to simulate pod creation and identify potential policy conflicts before deployment. For example:
kubectl run nginx-test --image=nginx --dry-run=client -o yaml | kubectl apply --validate=true -f -This command simulates the deployment of an nginx pod and validates the configuration against the existing PSPs.
Auditing PSP Configurations for Compliance
Regular auditing is critical to maintain compliance and ensure that PSPs remain effective over time. Auditing involves reviewing PSP configurations, monitoring policy enforcement, and identifying potential vulnerabilities.
- Establish a Regular Audit Schedule: Define a regular schedule (e.g., quarterly or bi-annually) for auditing PSP configurations.
- Review Policy Definitions: Examine each PSP to ensure that its configurations are still appropriate for the applications it governs and that they align with security best practices.
- Verify Policy Enforcement: Monitor the Kubernetes audit logs to confirm that PSPs are actively enforcing the defined policies and that there are no unexpected policy violations.
- Assess Policy Coverage: Evaluate the coverage of PSPs across all namespaces and applications to identify any gaps in protection.
- Document Audit Findings: Maintain a record of all audit findings, including any identified issues, corrective actions taken, and the dates of the audits.
- Automate Auditing: Consider automating parts of the auditing process using tools that can scan PSP configurations and identify potential vulnerabilities or compliance violations. For example, tools can be configured to check for overly permissive settings, outdated configurations, or inconsistencies with security standards.
- Use a Checklist: Employ a checklist to ensure a comprehensive audit process. An example checklist could include:
- Review of all PSPs.
- Verification of the `privileged` attribute.
- Validation of user and group ID restrictions.
- Review of volume type restrictions.
- Assessment of network policy interaction.
- Examination of audit logs for policy violations.
PSPs and Security Context
Pod Security Policies (PSPs) play a crucial role in defining the security context of a pod. They work in tandem, allowing administrators to finely control the security settings applied to pods, thereby enhancing the overall security posture of a Kubernetes cluster. This interaction ensures that pods operate within defined boundaries, minimizing the potential impact of security breaches.
Interactions Between Pod Security Policies and Security Context
The security context of a pod is a set of parameters that define the security settings for a pod and its containers. These settings include user and group IDs, capabilities, SELinux options, and more. PSPs interact with the security context by enforcing these settings. When a pod is created, the Kubernetes API server evaluates the pod’s security context against the active PSPs.
If the pod’s security context violates any of the PSP rules, the pod creation is rejected. This mechanism ensures that only pods that comply with the defined security policies are allowed to run.
Enforcing Security Context Settings
PSPs enforce security context settings by examining and validating the configuration specified in the pod’s specification. PSPs can override or restrict certain settings. For example, a PSP can:
- Restrict the user and group IDs that a pod can run as.
- Limit the capabilities a pod can request.
- Prevent the use of privileged containers.
- Enforce read-only root file systems.
By controlling these aspects of the security context, PSPs help to mitigate potential security risks.
Example: Enforcing Specific Capabilities
A PSP can be configured to allow only a specific set of capabilities, effectively limiting the privileges a pod can obtain. This is a common practice to reduce the attack surface.
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
name: restricted-capabilities-psp
spec:
privileged: false
capabilities:
add:
-NET_BIND_SERVICE
drop:
-ALL
allowPrivilegeEscalation: false
runAsUser:
rule: MustRunAsNonRoot
seLinux:
rule: RunAsAny
In this example, the PSP named `restricted-capabilities-psp` denies the use of privileged containers, allows the `NET_BIND_SERVICE` capability, and drops all other capabilities. This PSP also enforces that the pod must run as a non-root user and does not restrict the SELinux context. This is a basic example and more complex configurations are possible.
Differences Between PSPs and Pod Security Admission
Understanding the evolution of Kubernetes security mechanisms is crucial for maintaining a secure and compliant cluster. Pod Security Policies (PSPs), while once the primary method for controlling pod security, are deprecated and slated for removal. Pod Security Admission (PSA) is the successor, offering a more integrated and flexible approach. This section compares PSPs and PSA, provides a transition strategy, and offers practical recommendations.
Comparing PSPs and Pod Security Admission
The shift from PSPs to Pod Security Admission represents a significant change in how Kubernetes manages pod security. Both aim to enforce security standards for pods, but they differ in their implementation, flexibility, and integration with the Kubernetes API.
- Implementation and Enforcement: PSPs are implemented as admission controllers. They intercept requests to create pods and, based on the configured policies, either allow or deny the pod creation. PSA, on the other hand, is also implemented as an admission controller but is integrated directly into the kube-apiserver. This integration allows for more efficient and streamlined enforcement.
- Configuration: PSPs are configured using separate `PodSecurityPolicy` objects, which are then referenced in `Role` and `RoleBinding` objects to grant permissions. PSA utilizes namespaces and labels to apply security policies. This simplifies the configuration process and makes it easier to manage policies across different namespaces.
- Flexibility and Granularity: PSPs offer a wide range of controls, allowing for fine-grained configuration. However, managing numerous PSPs and associated RBAC rules can become complex. PSA provides a more streamlined approach, with predefined security levels (e.g., `privileged`, `baseline`, and `restricted`) that offer a balance between security and ease of use. Customization is possible through profiles, but the predefined levels cover most common use cases.
- Maintenance and Future Support: PSPs are deprecated in Kubernetes v1.21 and will be removed in a future release. This means that they will no longer receive updates or bug fixes. PSA is the actively developed and supported solution for pod security.
- Error Reporting: PSPs, when rejecting a pod, provide a specific error message indicating which constraint was violated. PSA, when rejecting a pod, also provides informative error messages, indicating which security context violations occurred, helping in debugging and policy adjustments.
Transition Strategy from PSPs to Pod Security Admission
Migrating from PSPs to PSA involves several steps to ensure a smooth transition and maintain cluster security.
- Assessment: Evaluate your existing PSPs and identify the security requirements they enforce. Determine which PSA security levels (privileged, baseline, or restricted) best match your needs. Consider any custom configurations or exemptions needed.
- Namespace Labeling: Begin by labeling your namespaces with the desired PSA levels. This is the core of the transition. Start with `baseline` or `restricted` in less critical namespaces to minimize disruption.
- Testing: Thoroughly test your applications in the namespaces with PSA enabled. Verify that pods are created successfully and that security requirements are met. Address any issues related to pod creation failures or unexpected behavior.
- Policy Adjustment: Fine-tune the PSA levels as needed. You might need to create custom profiles or adjust resource requests/limits to meet specific application requirements.
- Monitoring: Monitor the cluster for any security violations or unexpected behavior. Review audit logs to understand the impact of PSA on pod creation and operation.
- PSP Removal: After verifying that PSA is functioning correctly and all applications are running as expected, remove the PSPs and associated RBAC rules. This completes the transition.
Feature Comparison Table
The following table provides a detailed comparison of PSPs and Pod Security Admission.
| Feature | PSP | Pod Security Admission | Recommendation |
|---|---|---|---|
| Configuration | Separate `PodSecurityPolicy` objects, referenced in `Role` and `RoleBinding` objects. | Namespace labels with predefined security levels (`privileged`, `baseline`, `restricted`). | Begin by labeling namespaces with the appropriate PSA level (e.g., `baseline`). |
| Enforcement | Admission controller. | Integrated admission controller in kube-apiserver. | Use PSA as the primary pod security mechanism. |
| Flexibility | Highly flexible with a wide range of controls. | Predefined levels with customization options. | Start with predefined levels and customize as needed using profiles. |
| Maintenance | Deprecated and will be removed. | Actively maintained and supported. | Prioritize the use of PSA for long-term support. |
| Error Reporting | Provides specific error messages. | Provides specific error messages. | Use the error messages to troubleshoot and adjust policies. |
| RBAC Requirements | Requires RBAC configuration for PSP usage. | RBAC configuration is generally simplified compared to PSPs. | Review and simplify RBAC configuration during the transition. |
| Security Levels | Requires manual configuration of all security controls. | Predefined levels: `privileged`, `baseline`, and `restricted`. | Utilize the predefined levels for a balanced approach to security. |
| Granularity | Fine-grained control, which can lead to complexity. | More streamlined approach, easier to manage. | Optimize policies for maintainability and clarity. |
Troubleshooting Common PSP Issues
Working with Kubernetes Pod Security Policies (PSPs) can sometimes lead to unexpected behavior or errors. Understanding and resolving these issues is crucial for maintaining a secure and functional cluster. This section Artikels common problems, provides troubleshooting steps, and offers a FAQ to address typical PSP-related challenges.
Common PSP-Related Errors
Several errors can occur when implementing and managing PSPs. Identifying the root cause of these errors is the first step toward resolution.
- Pod Creation Failures: This is a frequent issue, where pods fail to launch due to PSP restrictions. These failures can manifest as events in the Kubernetes cluster, providing valuable clues about the underlying problem.
- Unexpected Pod Behavior: Even if pods are created, they might not function as intended. This could involve permission issues, volume mounting problems, or network connectivity limitations.
- Policy Enforcement Issues: Sometimes, policies might not be enforced as expected. This can be due to misconfigurations or conflicting policies.
- Permission Denials: Users or service accounts might experience permission denials when attempting to deploy pods, preventing them from carrying out necessary operations.
Troubleshooting Steps for Common PSP-Related Errors
When encountering PSP-related errors, a systematic approach is essential for efficient troubleshooting.
- Examine Pod Events: The `kubectl describe pod
` command is invaluable. It displays events related to the pod, including errors that triggered the failure. Examine these events for clues. - Review PSP Configuration: Carefully review the PSP applied to the namespace or the service account used by the pod. Check for misconfigurations in attributes like `runAsUser`, `fsGroup`, or volume permissions.
- Check Role Bindings: Ensure that the service account or user deploying the pod has the necessary permissions to use the PSP. Review the role bindings in the namespace to confirm the correct permissions are assigned.
- Verify Security Context: Confirm that the pod’s security context aligns with the PSP’s requirements. Check the pod’s YAML definition for settings like `runAsUser`, `runAsGroup`, and `capabilities`.
- Test in a Controlled Environment: Create a test environment or a dedicated namespace to experiment with PSP configurations without affecting production workloads.
- Use Audit Logs: Kubernetes audit logs can provide insights into policy violations. They record events related to API calls, including which PSPs were evaluated and whether they denied a request.
- Utilize the Dry-Run Feature: When applying a pod manifest, use the `–dry-run=client -o yaml` flag with `kubectl apply`. This simulates the application of the pod and can reveal potential PSP violations before actual deployment.
FAQ: Solutions to Typical PSP Problems
This FAQ addresses common issues and provides practical solutions.
- Why is my pod failing to create?
- The most common reason is a PSP violation. Use `kubectl describe pod
` to check the pod events. Verify that the pod’s security context and the service account’s permissions align with the applied PSP. Examine the PSP’s configurations, such as `runAsUser`, `fsGroup`, and volume restrictions. - How can I allow a pod to run as a specific user ID?
- Configure the `runAsUser` attribute in your PSP. Set the `runAsUser` strategy to `MustRunAs` and specify the allowed user ID or range. Ensure that the pod’s security context also specifies the same user ID or falls within the allowed range. For example:
apiVersion: policy/v1beta1kind: PodSecurityPolicymetadata: name: allow-specific-userspec: runAsUser: rule: MustRunAs ranges: -min: 1000 max: 1000 ...
- How do I allow a pod to use a specific volume type?
- Configure the `volumes` attribute in your PSP. Set the `volumes` strategy to `allowed` and specify the allowed volume types (e.g., `configMap`, `emptyDir`, `persistentVolumeClaim`). If you want to allow all volume types, use the `*` wildcard. Be mindful of the security implications of allowing all volume types.
- Why is my pod unable to access a specific file or directory?
- This could be due to incorrect user or group IDs. Verify the `runAsUser` and `fsGroup` settings in your PSP and the pod’s security context. Ensure that the user ID and group ID specified in the pod have the necessary permissions to access the files and directories. Also, check the ownership and permissions of the files and directories within the volume.
- How do I debug PSP enforcement issues?
- Enable Kubernetes audit logging to capture API requests and PSP evaluation results. Examine the logs to identify the PSPs that were evaluated and the reasons for any denials. Use `kubectl describe pod` to view pod events. Verify the role bindings of the service account used by the pod.
- What are common mistakes when configuring PSPs?
- Common mistakes include:
- Overly restrictive policies: Preventing pods from performing necessary operations.
- Incorrect user and group ID settings: Causing permission problems.
- Insufficient volume restrictions: Exposing the cluster to security risks.
- Misconfigured role bindings: Preventing users from deploying pods that meet PSP requirements.
- How do I handle conflicting PSPs?
- Kubernetes evaluates PSPs in a specific order, and the first PSP that allows the pod creation takes effect. Ensure your policies are designed to work together and do not create conflicts. Carefully consider the order in which policies are applied, paying attention to the permissions granted by each PSP.
Final Summary
In conclusion, understanding and implementing Pod Security Policies is paramount for maintaining a secure Kubernetes environment. By carefully configuring PSPs, you can mitigate risks associated with pod creation and operation, safeguarding your applications from potential vulnerabilities. As Kubernetes evolves, staying informed about the latest security practices, including the shift towards Pod Security Admission, is crucial for a robust and resilient infrastructure.
FAQ Overview
What happens if a pod violates a PSP?
If a pod specification violates a PSP, the pod creation will be rejected. The Kubernetes API server will return an error message, preventing the pod from being scheduled.
Can I have multiple PSPs in a namespace?
Yes, but only one PSP can be active and applied to a pod at a time. The active PSP is determined by the order in which they are evaluated and the user’s permissions.
How do I apply a PSP to a namespace?
You apply a PSP to a namespace by creating a Role or ClusterRole that grants the necessary permissions to use the PSP and then binding that Role or ClusterRole to a ServiceAccount used by the pods in the namespace.
What is the difference between PSP and Network Policies?
PSPs focus on the security of the pod itself (e.g., user IDs, volume types), while Network Policies control network traffic to and from pods, creating an additional layer of security.


