Understanding what is a landing zone in a cloud environment is fundamental for organizations embracing cloud computing. It serves as the foundational architecture, the pre-configured and secure environment from which all cloud-based resources and applications are launched. Think of it as the meticulously planned infrastructure that welcomes your digital assets, providing a secure and efficient framework for operations.
This structured approach to cloud deployment offers significant advantages, including enhanced security, streamlined governance, and optimized cost management. By establishing a well-defined landing zone, organizations can significantly reduce the complexities associated with cloud adoption, enabling them to focus on their core business objectives while maintaining control and compliance within their cloud environment.
Defining a Cloud Landing Zone
A cloud landing zone represents a well-architected, secure, and scalable foundation for deploying and operating workloads in a cloud environment. It encompasses a set of pre-configured resources, policies, and configurations that streamline the onboarding process and ensure adherence to best practices from the outset. The primary goal is to provide a consistent and repeatable framework, enabling organizations to rapidly deploy applications and services while minimizing risk and maximizing efficiency.
Core Concept and Primary Function
The core concept of a cloud landing zone centers on establishing a standardized and automated environment. This environment is designed to facilitate the deployment of applications and services in a secure, compliant, and operationally efficient manner. The primary function is to act as a control plane, providing a consistent set of governance, security, and operational guardrails across all deployed workloads.
It essentially pre-configures the infrastructure components needed to support various applications.
Analogy for Non-Technical Audiences
Imagine a new city. Before anyone can build a house or open a business, the city needs a foundation. This foundation includes things like roads, utilities (water, electricity, internet), and basic services like police and fire departments. A cloud landing zone is similar to this city foundation. It sets up the essential infrastructure and services needed before any applications (houses and businesses) can be deployed in the cloud.
It provides the necessary framework for security, access control, and operational management, ensuring that everything runs smoothly and securely from the start.
Benefits of Implementing a Landing Zone
Implementing a cloud landing zone offers significant advantages across several key areas. These benefits contribute to improved security posture, reduced operational costs, and enhanced operational efficiency.
- Security: A landing zone strengthens security by establishing a robust security baseline. This includes pre-configured security controls, such as network segmentation, identity and access management (IAM) policies, and data encryption. This proactive approach minimizes the attack surface and reduces the risk of security breaches. For example, a landing zone might enforce multi-factor authentication (MFA) across all user accounts, significantly reducing the likelihood of unauthorized access.
- Cost Optimization: Landing zones contribute to cost optimization by promoting resource efficiency and cost management. They often include pre-configured cost allocation tags and budget alerts, enabling organizations to track and control cloud spending effectively. Moreover, automated infrastructure deployment and management, which is a core component of a landing zone, can reduce the need for manual intervention, lowering operational costs. A practical illustration is the use of reserved instances or spot instances, which are frequently integrated into landing zone configurations to optimize compute costs.
- Operational Efficiency: Landing zones streamline operational processes, leading to increased efficiency and faster time-to-market. They provide a consistent and automated approach to deploying and managing infrastructure, reducing manual effort and the potential for errors. This standardization simplifies operational tasks, such as patching, monitoring, and incident response. An example of this is automated infrastructure-as-code (IaC) deployments, allowing for the rapid and repeatable provisioning of resources.
Key Components of a Landing Zone
A cloud landing zone is a foundational element for any cloud environment, and its effectiveness hinges on the integration of several key components. These components, working in concert, provide the necessary infrastructure, security, and governance to support various workloads and applications. A well-designed landing zone streamlines deployment, enhances security posture, and facilitates efficient management.
Identity and Access Management (IAM)
Identity and Access Management (IAM) forms the bedrock of security within a cloud landing zone, controlling who can access resources and what actions they can perform. It is critical for enforcing the principle of least privilege, where users are granted only the necessary permissions to perform their tasks. This minimizes the attack surface and reduces the potential impact of security breaches.
- User Authentication and Authorization: IAM systems provide mechanisms for verifying user identities (authentication) and determining their access rights (authorization). This typically involves the use of usernames and passwords, multi-factor authentication (MFA), and potentially integrations with existing on-premises identity providers (e.g., Active Directory).
- Role-Based Access Control (RBAC): RBAC is a crucial element, allowing administrators to assign predefined roles to users or groups. Each role defines a set of permissions, such as the ability to create virtual machines, modify network configurations, or access specific data. This simplifies access management and ensures consistency across the environment. For example, a “Network Administrator” role might have permissions to manage virtual networks and security groups.
- Identity Federation: IAM facilitates identity federation, allowing users to access cloud resources using their existing credentials from an on-premises identity provider. This streamlines user onboarding and simplifies access management by centralizing identity management.
- Monitoring and Auditing: IAM solutions provide comprehensive logging and auditing capabilities, tracking user activities and access attempts. This information is essential for security investigations, compliance reporting, and identifying potential security threats.
Network Configuration and Security Groups
Network configuration and security groups are fundamental for controlling network traffic and securing resources within the landing zone. They define how resources communicate with each other and with the outside world, playing a critical role in isolating workloads and preventing unauthorized access.
- Virtual Networks (VPCs): Virtual Private Clouds (VPCs) or equivalent network constructs provide logically isolated networks within the cloud environment. These networks offer a private address space and enable segmentation of resources. Within a VPC, different subnets can be created to further isolate resources based on function or security requirements.
- Subnets and Routing: Subnets divide the VPC into smaller, manageable segments. Routing tables define how network traffic is directed between subnets and external networks. Properly configured routing is crucial for enabling communication between resources and ensuring secure access.
- Security Groups (Firewalls): Security groups act as virtual firewalls, controlling inbound and outbound traffic to resources. They define a set of rules that specify which traffic is allowed or denied based on source IP address, port number, and protocol. Security groups are typically associated with individual resources, such as virtual machines or database instances.
- Network Address Translation (NAT): NAT enables resources within a private subnet to access the internet while hiding their private IP addresses. This enhances security by preventing direct access to internal resources from the public internet.
Essential Components and Their Functions
Below is a table summarizing the key components of a landing zone and their primary functions.
| Component | Function | Description | Example |
|---|---|---|---|
| Identity and Access Management (IAM) | Manages user identities and access permissions. | Controls who can access resources and what actions they can perform, enforcing the principle of least privilege. | Creating users, assigning roles, and managing multi-factor authentication (MFA). |
| Network Configuration | Defines the network infrastructure and connectivity. | Creates virtual networks (VPCs), subnets, and routing configurations to enable communication and isolate resources. | Setting up a VPC with public and private subnets for web servers and database servers, respectively. |
| Security Groups | Controls network traffic to and from resources. | Acts as virtual firewalls, defining rules to allow or deny traffic based on source, destination, port, and protocol. | Allowing HTTP (port 80) and HTTPS (port 443) traffic to web servers while blocking all other traffic. |
| Governance and Compliance | Establishes policies and enforces compliance requirements. | Implements policies for resource tagging, cost management, and security best practices. | Enforcing a policy that requires all resources to be tagged with cost centers and application owners. |
Purpose and Benefits of a Landing Zone
A cloud landing zone serves as the foundational blueprint for a secure, scalable, and well-governed cloud environment. Its primary purpose revolves around streamlining cloud adoption, ensuring operational efficiency, and minimizing risks associated with cloud deployments. The benefits are multifaceted, impacting governance, application deployment speed, and cost optimization.
Primary Goals of a Cloud Landing Zone
The core objectives of a cloud landing zone are multifaceted, encompassing security, governance, and operational excellence. These goals are interwoven to create a stable and reliable cloud foundation.
- Security: Establishing robust security controls is paramount. This includes implementing identity and access management (IAM) policies, network segmentation, and data encryption. The landing zone should enforce security best practices from the outset, minimizing the attack surface and protecting sensitive data. For instance, a landing zone might mandate the use of multi-factor authentication (MFA) for all user accounts and automatically encrypt all data at rest.
- Governance: A well-defined landing zone enforces organizational policies and regulatory compliance. This includes defining roles and responsibilities, establishing clear processes for change management, and implementing automated monitoring and auditing. This ensures consistent application of governance policies across all cloud resources. For example, a landing zone might automatically enforce tagging policies to facilitate cost allocation and resource tracking, or it may automatically log all API calls for auditing purposes.
- Operational Efficiency: The landing zone streamlines operational processes, reducing manual effort and promoting automation. This includes automating infrastructure provisioning, configuration management, and patching. Automation not only reduces the potential for human error but also allows for faster deployment cycles and improved resource utilization. An example is using Infrastructure as Code (IaC) to automate the creation of virtual machines, networks, and storage.
- Scalability and Resilience: The design of a landing zone should consider scalability and resilience from the beginning. This includes utilizing services that can automatically scale based on demand and implementing redundancy to ensure high availability. For instance, a landing zone might leverage auto-scaling groups to automatically adjust the number of virtual machines based on CPU utilization, or it may utilize multi-region deployments to ensure application availability even in the event of a regional outage.
Simplifying Cloud Governance and Compliance
A cloud landing zone significantly simplifies cloud governance and compliance efforts by providing a standardized and automated approach to policy enforcement. This ensures that all cloud resources adhere to organizational and regulatory requirements.
- Centralized Policy Enforcement: A landing zone enables centralized policy enforcement through automated configuration management tools. This ensures that security policies, access controls, and other governance rules are consistently applied across all cloud resources. This eliminates the risk of inconsistent configurations and reduces the administrative overhead associated with manual policy enforcement. For example, a landing zone can automatically apply a specific security group configuration to all new virtual machines.
- Automated Compliance Checks: Landing zones often include automated compliance checks that verify adherence to regulatory requirements such as HIPAA, PCI DSS, or GDPR. These checks can identify and remediate non-compliant configurations, reducing the risk of penalties and data breaches. For instance, a landing zone might automatically scan for vulnerabilities and misconfigurations, generating reports and alerting administrators to potential issues.
- Standardized Auditing and Logging: A well-designed landing zone provides standardized auditing and logging capabilities. This enables organizations to track all cloud activities, identify security incidents, and demonstrate compliance to auditors. This includes logging user activity, system events, and API calls. For example, a landing zone might automatically forward all logs to a centralized security information and event management (SIEM) system for analysis and alerting.
- Improved Resource Tagging and Organization: Landing zones often incorporate automated resource tagging and organization. This allows organizations to easily track and manage cloud resources, allocate costs, and identify ownership. This simplifies governance and compliance by providing a clear understanding of the cloud environment. For instance, a landing zone might automatically tag all resources with information such as the department, application owner, and cost center.
Facilitating Faster Application Deployment
A cloud landing zone accelerates application deployment by providing a pre-configured, automated, and standardized environment. This allows development teams to focus on building applications rather than configuring infrastructure.
- Infrastructure as Code (IaC): Landing zones typically utilize Infrastructure as Code (IaC) to automate the provisioning and configuration of cloud resources. This enables developers to quickly and easily deploy applications by defining infrastructure requirements in code. This reduces the time and effort required to set up the infrastructure needed for new applications. For instance, a developer can deploy a new web application by simply providing a configuration file that specifies the desired resources, such as virtual machines, databases, and load balancers.
- Pre-configured Services: A landing zone provides a set of pre-configured services, such as networking, security, and monitoring. This eliminates the need for developers to configure these services from scratch, saving time and effort. For example, a landing zone might include a pre-configured virtual private cloud (VPC) with pre-defined security groups and network access control lists (ACLs).
- Automated Deployment Pipelines: Landing zones often integrate with automated deployment pipelines that streamline the application release process. This allows developers to automate the build, test, and deployment of applications. This reduces the risk of human error and speeds up the deployment process. For instance, a landing zone might integrate with a continuous integration and continuous delivery (CI/CD) pipeline that automatically deploys code changes to a testing environment and then to production.
- Standardized Environments: A landing zone provides standardized environments across different teams and projects. This ensures consistency and reduces the risk of compatibility issues. For example, all development teams might use the same operating system, programming languages, and development tools.
Cost-Saving Potential of a Well-Designed Landing Zone
A well-designed cloud landing zone contributes to significant cost savings through various mechanisms, including resource optimization, automated management, and improved visibility into cloud spending.
- Resource Optimization: A landing zone promotes resource optimization by enabling the efficient allocation and utilization of cloud resources. This includes utilizing right-sizing, auto-scaling, and other optimization techniques. This minimizes wasted resources and reduces overall cloud costs. For instance, a landing zone might automatically scale virtual machines up or down based on CPU utilization, ensuring that resources are only used when needed.
- Automated Cost Management: Landing zones often include automated cost management tools that help organizations track and control cloud spending. This includes features such as cost allocation tagging, budgeting, and anomaly detection. This allows organizations to identify and address cost inefficiencies proactively. For example, a landing zone might automatically generate reports that show the cost of each department or application.
- Improved Visibility into Cloud Spending: A landing zone provides improved visibility into cloud spending by providing centralized dashboards and reporting. This allows organizations to understand how their cloud resources are being used and identify areas where costs can be reduced. For instance, a landing zone might provide a dashboard that shows the cost of each cloud service and the trends in cloud spending over time.
- Reduced Operational Overhead: A landing zone reduces operational overhead by automating tasks such as infrastructure provisioning, configuration management, and patching. This frees up IT staff to focus on more strategic initiatives, reducing labor costs. For example, a landing zone might automatically patch all virtual machines on a regular schedule.
Landing Zone Design Principles
Designing a cloud landing zone necessitates adherence to a set of core principles to ensure security, scalability, and operational efficiency. These principles guide the architecture and implementation, facilitating a robust and adaptable cloud environment. Proper design anticipates future growth and changing business requirements, providing a foundation for consistent governance and control.
Best Practices for Cloud Landing Zone Design
Implementing best practices in cloud landing zone design involves a multi-faceted approach, focusing on automation, security, and infrastructure as code. These practices promote a standardized, repeatable, and easily managed environment.
- Infrastructure as Code (IaC): Define all infrastructure components, including networking, compute, and security configurations, as code. Tools like Terraform, AWS CloudFormation, or Azure Resource Manager templates enable version control, repeatability, and automated deployment. For example, a standardized network configuration with pre-defined subnets, security groups, and routing tables can be deployed across multiple regions or accounts with minimal manual intervention. This approach drastically reduces the potential for human error and speeds up deployment cycles.
- Automation: Automate all aspects of the landing zone setup, including account creation, network configuration, security policy enforcement, and application deployment pipelines. Automation minimizes manual effort, reduces the risk of misconfiguration, and allows for consistent application of security and compliance policies. Utilizing tools like AWS Control Tower, Azure Blueprints, or Google Cloud Deployment Manager can streamline the process.
- Security by Default: Implement security best practices from the outset. This includes strong identity and access management (IAM) controls, encryption of data at rest and in transit, and regular security audits. Configure security groups, network access control lists (ACLs), and web application firewalls (WAFs) to protect against common threats. Regularly update security configurations and patching.
- Centralized Logging and Monitoring: Implement centralized logging and monitoring solutions to collect and analyze logs from all cloud resources. This allows for proactive detection of security threats, performance issues, and compliance violations. Use tools like AWS CloudWatch, Azure Monitor, or Google Cloud Operations Suite for log aggregation, monitoring, and alerting.
- Multi-Account Strategy: Design the landing zone with a multi-account strategy, isolating workloads and environments (e.g., development, staging, production) into separate accounts. This provides improved security, resource isolation, and billing management. Each account can have its own security policies and access controls.
- Cost Optimization: Implement cost optimization strategies, such as right-sizing resources, utilizing reserved instances or committed use discounts, and monitoring cloud spending. Tag resources for better cost allocation and reporting. Regularly review resource utilization to identify opportunities for optimization.
- Compliance and Governance: Design the landing zone to meet regulatory and compliance requirements. Implement policies and controls to ensure adherence to industry standards, such as HIPAA, PCI DSS, or GDPR. Leverage cloud-native services like AWS Config, Azure Policy, or Google Cloud Policy to enforce compliance.
Scalable and Repeatable Design Patterns
Scalability and repeatability are key tenets of cloud landing zone design. Employing design patterns ensures that the infrastructure can accommodate growth and be consistently deployed across different environments or regions.
- Network Design: Employ a hub-and-spoke network topology. The hub acts as a central point for connectivity, security, and shared services, while spokes represent individual workloads or applications. This design facilitates centralized management of network resources and allows for isolation of workloads. For instance, a hub VPC (Virtual Private Cloud) in AWS can connect to multiple spoke VPCs via VPC peering, allowing for secure communication between them.
- Identity and Access Management (IAM) Patterns: Implement a centralized IAM strategy, such as using a single sign-on (SSO) solution or federated identities. Define roles and permissions based on the principle of least privilege, granting users only the necessary access to perform their tasks. Utilize IAM roles to allow applications to access other cloud resources securely.
- Automation Pipelines: Implement CI/CD (Continuous Integration/Continuous Deployment) pipelines for infrastructure provisioning and application deployment. These pipelines automate the process of building, testing, and deploying changes to the landing zone and application code. Tools like Jenkins, GitLab CI, or Azure DevOps can be used to automate these processes.
- Configuration Management: Use configuration management tools like Ansible, Chef, or Puppet to automate the configuration of servers and applications within the landing zone. This ensures consistency across all instances and reduces the risk of configuration drift.
- Data Lake Architecture: Design the landing zone to accommodate a data lake, where data from various sources can be ingested, stored, and processed. Implement data governance policies to ensure data quality and compliance. Utilize services like AWS S3, Azure Data Lake Storage, or Google Cloud Storage for storing data.
The core of automation in landing zone setup revolves around these principles:
- Infrastructure as Code: Define all infrastructure components in code, enabling version control and repeatability.
- Automated Provisioning: Automate the deployment of resources, minimizing manual intervention.
- Continuous Integration/Continuous Deployment (CI/CD): Implement pipelines for automated testing and deployment of changes.
- Configuration Management: Utilize tools to ensure consistent configuration across all instances.
Designing a Landing Zone Aligned with Industry Best Practices
Aligning the landing zone design with industry best practices ensures that the cloud environment is secure, scalable, and compliant. This involves incorporating security, governance, and operational best practices into the architecture and implementation.
- Security Baseline: Establish a security baseline that defines the minimum security requirements for all cloud resources. This baseline should include IAM policies, encryption standards, network security configurations, and monitoring and logging requirements. Continuously monitor and update the security baseline as new threats emerge.
- Governance Framework: Implement a governance framework that defines the policies, processes, and controls for managing the cloud environment. This framework should address areas such as cost management, security, compliance, and operational excellence.
- Account Structure: Establish a well-defined account structure that aligns with the organization’s business units, applications, and environments. Use a multi-account strategy to isolate workloads and improve security. Each account should have a clear purpose and ownership.
- Network Segmentation: Implement network segmentation to isolate different workloads and applications. Use VPCs, subnets, and security groups to control network traffic and prevent unauthorized access. Employ a zero-trust network model, assuming no implicit trust within the network.
- Identity and Access Management (IAM): Enforce a strong IAM strategy. Implement multi-factor authentication (MFA), use least privilege access, and regularly review and update IAM policies. Use centralized identity providers to manage user identities and access.
- Data Protection: Implement data protection measures, including encryption of data at rest and in transit, data loss prevention (DLP) policies, and regular data backups. Regularly test data recovery procedures to ensure data availability.
- Compliance Controls: Implement compliance controls to meet regulatory and compliance requirements. Use cloud-native services to automate compliance checks and generate audit reports. Regularly review and update compliance controls to address changing regulations.
- Monitoring and Alerting: Implement comprehensive monitoring and alerting to detect security threats, performance issues, and compliance violations. Use centralized logging and monitoring tools to collect and analyze logs from all cloud resources. Establish clear escalation procedures for alerts.
Security in a Cloud Landing Zone
Implementing robust security measures is paramount within a cloud landing zone to safeguard resources, data, and applications from various threats. This encompasses a layered approach, integrating multiple security services and tools to provide comprehensive protection. The goal is to establish a secure baseline environment that adheres to security best practices and regulatory compliance requirements.
Security Measures Implemented in a Landing Zone
A cloud landing zone employs a multi-faceted approach to security, encompassing identity and access management, network security, data protection, and threat detection and response. These measures are designed to mitigate risks and ensure the confidentiality, integrity, and availability of cloud resources.
- Identity and Access Management (IAM): This is a cornerstone of security, controlling who can access cloud resources and what they can do. It involves:
- Multi-Factor Authentication (MFA): MFA mandates users to provide multiple verification factors (e.g., password and a code from a mobile app) to access resources, significantly reducing the risk of unauthorized access even if credentials are compromised.
- Role-Based Access Control (RBAC): RBAC assigns permissions based on a user’s role within the organization. This principle of least privilege ensures users only have the necessary access, minimizing the potential impact of a security breach. For example, a database administrator might have full access to database services, while a developer only has read and write access to specific application data.
- Centralized Identity Providers (IdPs): Integrating with IdPs (e.g., Active Directory, Okta) allows for centralized user management and authentication, simplifying access control and reducing administrative overhead. This ensures consistent identity management across the entire cloud environment.
- Network Security: Protecting the network perimeter and internal resources is critical. This includes:
- Virtual Private Clouds (VPCs) and Subnets: VPCs provide isolated networks within the cloud, allowing for segmentation and control over network traffic. Subnets further divide the VPC, enabling fine-grained control over resource placement and network access.
- Firewalls: Firewalls (e.g., web application firewalls (WAFs), network firewalls) filter network traffic based on predefined rules, blocking malicious traffic and protecting applications from attacks. WAFs specifically protect against web-based vulnerabilities.
- Network Segmentation: Dividing the network into logical segments based on function or sensitivity reduces the attack surface. This limits the impact of a security breach by preventing lateral movement within the network.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and automatically block or alert on suspicious behavior.
- Data Protection: Protecting data at rest and in transit is a key security concern. This involves:
- Encryption: Data is encrypted at rest (e.g., using encryption keys managed by a key management service) and in transit (e.g., using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols) to protect its confidentiality.
- Data Loss Prevention (DLP): DLP solutions monitor and prevent sensitive data from leaving the cloud environment or being accessed inappropriately.
- Data Backup and Recovery: Regular data backups and robust recovery procedures are essential to ensure business continuity in the event of data loss or a disaster.
- Threat Detection and Response: Proactive monitoring and incident response capabilities are crucial. This includes:
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing real-time threat detection and incident response capabilities.
- Vulnerability Scanning: Regularly scanning for vulnerabilities in applications and infrastructure helps identify and remediate security weaknesses before they can be exploited.
- Incident Response Plan: A well-defined incident response plan Artikels the steps to take in the event of a security incident, including containment, eradication, and recovery.
Security Services and Tools Integrated into a Landing Zone
A cloud landing zone typically integrates various security services and tools to provide comprehensive protection. These services often vary based on the cloud provider and the specific security requirements of the organization.
- Cloud Provider Native Security Services: These services are provided by the cloud provider and are designed to integrate seamlessly with other cloud services. Examples include:
- Identity and Access Management (IAM) Services: (e.g., AWS IAM, Azure Active Directory, Google Cloud IAM) manage user identities, roles, and permissions.
- Network Security Services: (e.g., AWS VPC, Azure Virtual Network, Google Cloud VPC) provide network isolation, firewalls, and other network security features.
- Security Monitoring Services: (e.g., AWS CloudWatch, Azure Monitor, Google Cloud Operations Suite) provide logging, monitoring, and alerting capabilities.
- Key Management Services (KMS): (e.g., AWS KMS, Azure Key Vault, Google Cloud KMS) manage encryption keys.
- Third-Party Security Tools: Organizations may also integrate third-party security tools to enhance their security posture. Examples include:
- Security Information and Event Management (SIEM) systems: (e.g., Splunk, Sumo Logic, Datadog) aggregate and analyze security logs.
- Vulnerability Scanners: (e.g., Tenable, Qualys, Rapid7) identify vulnerabilities in applications and infrastructure.
- Web Application Firewalls (WAFs): (e.g., Cloudflare, Imperva, AWS WAF) protect web applications from attacks.
- Endpoint Detection and Response (EDR) solutions: (e.g., CrowdStrike, SentinelOne, Microsoft Defender for Endpoint) provide endpoint security and threat detection.
Configuring Logging and Monitoring for Security Auditing
Effective logging and monitoring are crucial for security auditing, incident response, and compliance. Properly configured logging allows for the tracking of security events, while monitoring provides real-time insights into the security posture of the environment.
- Logging Configuration:
- Centralized Logging: Configure all cloud services and applications to send logs to a centralized logging platform (e.g., a SIEM system or a dedicated log management service). This enables centralized analysis and correlation of security events.
- Log Retention Policies: Define appropriate log retention policies based on regulatory requirements and organizational needs. This ensures that logs are retained for the required duration.
- Log Filtering and Aggregation: Implement log filtering and aggregation to reduce noise and focus on relevant security events. This can improve the efficiency of security investigations.
- Log Integrity: Implement measures to ensure the integrity of logs, such as using digital signatures or write-once storage. This prevents tampering with log data.
- Monitoring Configuration:
- Real-time Monitoring: Configure real-time monitoring of security events and system performance metrics. This allows for the rapid detection of security threats and performance issues.
- Alerting Rules: Define alerting rules to trigger notifications when specific security events occur. This ensures that security teams are notified of potential threats in a timely manner.
- Dashboards and Reporting: Create dashboards and reports to visualize security data and track key performance indicators (KPIs). This provides insights into the overall security posture of the environment.
- Security Auditing: Regularly review logs and monitoring data to identify security vulnerabilities, assess the effectiveness of security controls, and ensure compliance with regulatory requirements.
Security Benefits of a Landing Zone
A well-designed landing zone provides several key security benefits, improving the overall security posture of the cloud environment.
- Enhanced Security Posture: A landing zone provides a secure baseline, reducing the risk of misconfigurations and vulnerabilities.
- Improved Compliance: The landing zone facilitates compliance with industry regulations and internal security policies.
- Reduced Attack Surface: Network segmentation and access controls limit the attack surface, reducing the potential impact of a security breach.
- Simplified Security Management: Centralized security services and tools streamline security management and reduce administrative overhead.
- Faster Incident Response: Logging, monitoring, and alerting capabilities enable faster detection and response to security incidents.
- Increased Visibility: Centralized logging and monitoring provide greater visibility into security events and system performance.
- Improved Data Protection: Data encryption, data loss prevention, and backup and recovery mechanisms protect sensitive data.
Networking and Connectivity
Network configuration is a critical aspect of a cloud landing zone, establishing the foundation for secure and efficient communication between cloud resources, on-premises environments, and the internet. Proper network design ensures optimal performance, security, and compliance with organizational policies. This section will delve into the network configuration aspects, including establishing connectivity with on-premises environments, managing virtual networks and subnets, and providing a detailed overview of a typical landing zone network architecture.
Network Configuration Aspects
Cloud landing zone network configuration involves several key considerations to ensure a robust and scalable network infrastructure.
- Virtual Network Design: Defining virtual networks (VNets) and their address spaces is fundamental. This includes determining the size of the address space, the number of subnets required, and the purpose of each subnet (e.g., application tier, database tier, management subnet). The choice of address space should avoid conflicts with on-premises networks and consider future scalability.
- Subnetting and Segmentation: Subnetting allows for the logical grouping of resources based on function, security requirements, or geographical location. Segmentation enhances security by isolating different parts of the application or environment. This is achieved through the use of Network Security Groups (NSGs) or security rules that define the allowed traffic between subnets.
- Routing and Network Appliances: Configuring routing tables and deploying network appliances, such as firewalls and load balancers, is essential. Routing tables direct network traffic between subnets and external networks. Network appliances provide advanced security features, traffic management, and high availability.
- DNS Configuration: DNS (Domain Name System) plays a vital role in name resolution within the cloud environment. Proper configuration ensures that resources can be accessed by their names, simplifying management and improving usability. This often involves setting up private DNS zones for internal resources and integrating with on-premises DNS servers.
- Connectivity with External Networks: Establishing connectivity with the internet and on-premises environments is crucial. This involves configuring public IP addresses, gateways, and VPN or direct connect solutions.
Establishing Connectivity with On-Premises Environments
Establishing secure and reliable connectivity with on-premises environments is a common requirement for hybrid cloud deployments. Several methods can be employed to achieve this.
- VPN (Virtual Private Network): VPNs provide a secure, encrypted tunnel over the public internet. They are a cost-effective solution for connecting on-premises networks to the cloud. Site-to-site VPNs connect entire networks, while point-to-site VPNs allow individual devices to connect. VPNs typically use protocols like IPsec to encrypt traffic.
- Direct Connect: Direct Connect provides a dedicated, private network connection between on-premises and the cloud provider. This offers higher bandwidth, lower latency, and more consistent performance compared to VPNs. Direct Connect is typically used for workloads that require high throughput or low latency, such as data replication or real-time applications.
- ExpressRoute (Azure) / Cloud Interconnect (Google Cloud) / AWS Direct Connect: These are specific implementations of Direct Connect offered by cloud providers. They provide a managed service for establishing private connections. For example, Microsoft Azure ExpressRoute provides a dedicated, private connection to Azure, bypassing the public internet.
- Hybrid DNS: Hybrid DNS solutions are essential for resolving names across both on-premises and cloud environments. This often involves forwarding DNS queries between the on-premises DNS servers and the cloud provider’s DNS services.
Managing Virtual Networks and Subnets
Efficient management of virtual networks and subnets is essential for maintaining a well-organized and secure cloud environment.
- Subnet Allocation: Careful planning of subnet allocation is crucial. Subnets should be sized appropriately to accommodate the expected number of resources. Over-allocating can waste IP addresses, while under-allocating can lead to network outages. Consider using a CIDR (Classless Inter-Domain Routing) block that is large enough to accommodate future growth.
- Network Security Groups (NSGs): NSGs act as virtual firewalls, controlling inbound and outbound traffic at the subnet or network interface level. Implementing NSGs with granular rules is a key element of network security. This involves defining rules that allow only necessary traffic and deny all other traffic.
- Routing Tables: Routing tables define the paths that network traffic takes between subnets and external networks. Properly configuring routing tables ensures that traffic is directed to the correct destination.
- Network Address Translation (NAT): NAT allows resources within a private subnet to access the internet while hiding their private IP addresses. This can be implemented using NAT gateways or NAT instances.
- Monitoring and Logging: Monitoring network traffic and logging network events are essential for troubleshooting and security analysis. Network monitoring tools can track traffic patterns, identify bottlenecks, and detect security threats.
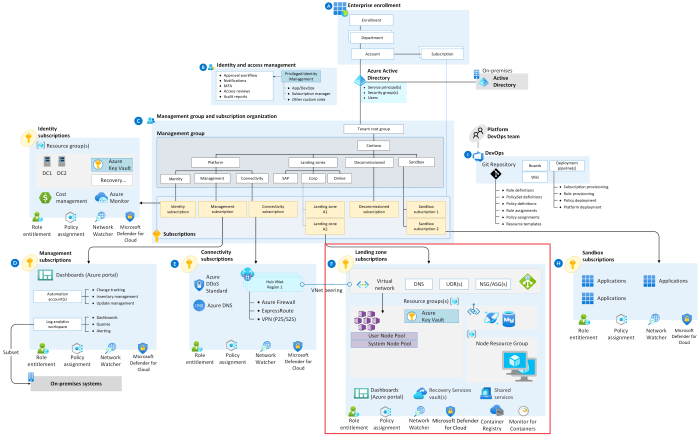
Network Architecture of a Landing Zone: Descriptive Summary for an Image
The following describes the network architecture of a typical landing zone. The architecture includes several interconnected components, demonstrating a multi-layered approach to security and connectivity.
The image depicts a cloud landing zone network architecture, with the central component being a virtual network (VNet) that serves as the foundation for the entire network. The VNet is divided into several subnets, each serving a specific purpose and designed with security in mind.
The first major component is a dedicated subnet for a VPN Gateway, which provides secure connectivity with on-premises environments. This allows for hybrid cloud deployments where resources can communicate with on-premises infrastructure. A Direct Connect gateway or a similar service provides an alternative, high-bandwidth, low-latency connection to the on-premises network, bypassing the public internet for improved performance and security.
A second subnet is dedicated to a Web Application Firewall (WAF), which is placed in front of the web application to protect against common web vulnerabilities. This is often deployed using a managed service provided by the cloud provider. Another subnet contains load balancers that distribute traffic across multiple application instances for high availability and scalability. These load balancers could be either public or internal, depending on the requirements of the application.
The application subnet is where the core application components reside. It typically contains virtual machines, containers, or serverless functions that make up the application’s functionality. This subnet is protected by Network Security Groups (NSGs) that control inbound and outbound traffic based on security rules. A private subnet is used for database servers, which further isolates them from the public internet.
Another subnet is used for jump boxes or bastion hosts, which are secure access points for administrators to manage the cloud resources. These are typically hardened and monitored to prevent unauthorized access. Finally, a management subnet contains the tools and services used for monitoring, logging, and other administrative tasks.
Each subnet has its own security rules, ensuring that traffic is allowed only where necessary. This segmentation helps isolate resources and minimize the impact of any security breaches. The architecture also includes a public subnet that allows access to internet-facing services and resources. All the components are interconnected using routing tables, which direct traffic between subnets and external networks. This architecture provides a secure, scalable, and manageable cloud environment.
Automation and Infrastructure as Code (IaC)
Automation and Infrastructure as Code (IaC) are fundamental to the successful deployment and management of a cloud landing zone. They enable efficient, repeatable, and scalable operations, transforming how infrastructure is provisioned and maintained. This section explores the role of automation, provides examples of IaC tools, and details how these tools contribute to consistency and repeatability within a cloud environment.
Role of Automation in Landing Zone Deployment and Management
Automation streamlines the entire lifecycle of a landing zone, from initial setup to ongoing management and updates. By automating tasks, organizations can reduce manual effort, minimize human error, and accelerate deployment timelines. Automation facilitates consistent configuration across environments, ensuring compliance with security policies and operational best practices. It also allows for dynamic scaling and resource allocation based on demand, optimizing resource utilization and cost.
Examples of IaC Tools for Building a Landing Zone
Several IaC tools are available to build and manage a cloud landing zone. These tools enable the definition and management of infrastructure through code, allowing for version control, collaboration, and automated deployments. The choice of tool often depends on the cloud provider and the specific requirements of the organization.* Terraform: Terraform is a popular, open-source IaC tool that supports multiple cloud providers, including AWS, Azure, and Google Cloud Platform (GCP).
It uses a declarative configuration language to define infrastructure resources. Terraform excels at managing complex infrastructure deployments and supports a modular approach, enabling the reuse of infrastructure components.
AWS CloudFormation
AWS CloudFormation is a service provided by Amazon Web Services (AWS) for defining and managing AWS infrastructure as code. It uses JSON or YAML templates to describe the desired infrastructure. CloudFormation is tightly integrated with AWS services, making it a natural choice for organizations primarily using AWS.
Azure Resource Manager (ARM) Templates
Azure Resource Manager (ARM) templates are used to define and deploy Azure resources. They are written in JSON and allow for the definition of complex Azure environments. ARM templates are tightly integrated with Azure services and provide features such as parameterization and modularity.
Google Cloud Deployment Manager
Google Cloud Deployment Manager is a service provided by Google Cloud Platform (GCP) for defining and deploying GCP resources. It uses YAML templates to describe the desired infrastructure. Deployment Manager supports a declarative approach and integrates with various GCP services.
Using IaC to Ensure Consistency and Repeatability
IaC promotes consistency and repeatability by codifying infrastructure configurations. This ensures that environments are built and managed in a standardized manner, regardless of the deployment location or time. When infrastructure is defined as code, it can be version-controlled, allowing for tracking changes, rolling back to previous states, and collaborating effectively.IaC allows for the creation of reusable modules or templates. These modules encapsulate specific infrastructure components, such as virtual networks, security groups, or databases.
Reusing these modules across different environments ensures consistency and reduces the risk of configuration drift. The infrastructure can be easily recreated at any time, providing a reliable and predictable foundation for cloud operations.IaC facilitates automated testing of infrastructure configurations. Before deploying changes to production, the infrastructure code can be tested to verify that it meets the desired specifications and security requirements.
This proactive approach reduces the likelihood of errors and ensures that changes are implemented safely.
Automation Benefits
Automation offers numerous benefits for cloud landing zone deployments and management. These benefits contribute to improved efficiency, reduced risk, and enhanced scalability.* Increased Efficiency: Automating infrastructure provisioning and management tasks reduces manual effort and accelerates deployment timelines.
Reduced Human Error
Automation minimizes the risk of human error, leading to more reliable and consistent configurations.
Improved Consistency
Automated deployments ensure consistent configurations across all environments, reducing the likelihood of configuration drift.
Enhanced Scalability
Automation allows for dynamic scaling of resources based on demand, optimizing resource utilization.
Faster Time to Market
Automated deployments enable organizations to deploy new applications and services more quickly.
Cost Optimization
Automation helps to optimize resource utilization and reduce operational costs.
Improved Compliance
Automation facilitates the enforcement of security policies and compliance requirements.
Enhanced Security
Automated security configurations and regular updates improve the overall security posture.
Version Control and Auditability
Infrastructure as code enables version control, allowing for tracking changes and auditing configurations.
Compliance and Governance
A well-architected cloud landing zone is critical for establishing and maintaining robust compliance and governance frameworks. By integrating these elements into the foundational infrastructure, organizations can effectively manage risk, meet regulatory requirements, and ensure operational consistency across their cloud environments. This proactive approach minimizes vulnerabilities and streamlines audits, ultimately leading to improved security posture and business agility.
Supporting Compliance with Industry Regulations
Cloud landing zones are instrumental in facilitating compliance with various industry regulations and standards. They provide the infrastructure and mechanisms necessary to enforce security policies, manage access controls, and maintain audit trails, all of which are essential for meeting regulatory obligations.
- Policy Enforcement: Landing zones allow for the centralized definition and enforcement of security policies, such as those related to data encryption, access control, and vulnerability management. This centralized control ensures that all resources deployed within the landing zone adhere to the defined policies, reducing the risk of non-compliance. For example, in the context of the Payment Card Industry Data Security Standard (PCI DSS), a landing zone can enforce policies requiring encryption of sensitive data at rest and in transit, and regular vulnerability scans.
- Access Control Management: Implementing robust access control mechanisms is crucial for compliance. Landing zones can integrate with identity and access management (IAM) systems to control who can access specific resources and what actions they can perform. This is vital for regulations like HIPAA, which mandates strict controls over patient health information. A landing zone can enforce least-privilege access, ensuring users only have the necessary permissions.
- Audit Logging and Monitoring: Comprehensive audit logging and monitoring capabilities are fundamental for demonstrating compliance. Landing zones can be configured to collect and store detailed audit logs, capturing all relevant activities within the cloud environment. This includes events like user logins, resource creation, and data access attempts. These logs can be used for forensic analysis, security incident response, and generating compliance reports. The logs are essential for proving adherence to regulations such as GDPR, which requires organizations to demonstrate accountability for data processing activities.
- Configuration Management: Maintaining consistent and compliant configurations across all resources is a key aspect of regulatory compliance. Landing zones can leverage infrastructure-as-code (IaC) to define and manage configurations, ensuring that all resources are deployed in a standardized and compliant manner. This approach minimizes the risk of misconfigurations that could lead to security vulnerabilities or non-compliance.
Examples of Governance Policies in a Landing Zone
Governance policies are the rules and guidelines that govern the use of cloud resources within a landing zone. They provide a framework for managing risk, ensuring security, and promoting operational efficiency. These policies are typically implemented through a combination of technical controls and organizational processes.
- Data Encryption Policy: This policy mandates the encryption of all sensitive data at rest and in transit. This helps protect data confidentiality and is a requirement for regulations like HIPAA and GDPR. For instance, a landing zone might automatically encrypt all data stored in cloud storage services using encryption keys managed by a central key management system.
- Access Control Policy: This policy defines who can access specific resources and the level of access they are granted. It typically enforces the principle of least privilege, granting users only the necessary permissions to perform their job functions. This is critical for protecting sensitive data and preventing unauthorized access. This could involve requiring multi-factor authentication (MFA) for all user logins and regularly reviewing and revoking access permissions.
- Network Security Policy: This policy governs network traffic and security within the landing zone. It defines rules for firewalls, intrusion detection systems, and other network security controls. This policy is designed to protect against unauthorized network access and malicious attacks. This might involve configuring a web application firewall (WAF) to protect against common web vulnerabilities or implementing network segmentation to isolate sensitive resources.
- Configuration Management Policy: This policy ensures that all resources are deployed and configured in a consistent and compliant manner. It often leverages IaC to define and manage configurations, ensuring that all resources meet security and compliance requirements. This helps prevent misconfigurations that could lead to vulnerabilities. For example, it might enforce a standard naming convention for all resources and require regular patching of operating systems and applications.
- Incident Response Policy: This policy Artikels the procedures for responding to security incidents. It defines roles and responsibilities, communication protocols, and steps for containing, eradicating, and recovering from security incidents. This is crucial for minimizing the impact of security breaches and ensuring a timely response.
Implementing Auditing and Reporting Mechanisms
Effective auditing and reporting mechanisms are essential for demonstrating compliance and monitoring the security posture of a cloud environment. These mechanisms provide visibility into the activities within the landing zone, enabling organizations to identify and address potential issues promptly.
- Centralized Logging: Implement a centralized logging solution to collect logs from all resources within the landing zone. This includes logs from operating systems, applications, network devices, and security tools. Centralized logging simplifies log analysis, security incident response, and compliance reporting. For instance, a security information and event management (SIEM) system can be used to aggregate and analyze logs from various sources.
- Automated Auditing: Automate the auditing process using tools that regularly assess the security posture of the landing zone. These tools can identify vulnerabilities, misconfigurations, and non-compliant resources. Automation reduces the manual effort required for auditing and ensures that assessments are performed consistently and frequently. Automated tools can perform vulnerability scans, configuration audits, and compliance checks.
- Reporting and Dashboards: Generate reports and dashboards that provide a clear and concise overview of the security and compliance status of the landing zone. These reports should include key metrics, such as the number of vulnerabilities, the status of compliance with regulations, and the number of security incidents. Dashboards provide real-time visibility into the security posture.
- Alerting and Notifications: Configure alerting and notification mechanisms to proactively notify relevant stakeholders of potential security threats or compliance violations. This allows for a timely response to incidents and helps prevent breaches. Alerts can be triggered based on specific events, such as unauthorized access attempts or failed login attempts.
- Regular Compliance Assessments: Conduct regular compliance assessments to ensure that the landing zone continues to meet regulatory requirements. These assessments should involve both automated and manual checks. The results of these assessments should be documented and used to identify areas for improvement.
The Role of Compliance and Governance
The following table summarizes the key aspects of compliance and governance within a cloud landing zone:
| Aspect | Description | Benefits | Examples |
|---|---|---|---|
| Policy Definition | Establishing and documenting the rules and guidelines that govern the use of cloud resources. | Ensures consistent application of security and compliance requirements. | Data encryption policies, access control policies, network security policies. |
| Enforcement Mechanisms | Implementing technical controls to enforce the defined policies. | Reduces the risk of non-compliance and unauthorized activities. | IAM, firewalls, vulnerability scanning tools, automated configuration management. |
| Monitoring and Auditing | Collecting and analyzing data to track compliance and identify potential issues. | Provides visibility into the security posture and enables proactive incident response. | Centralized logging, security information and event management (SIEM), regular audits. |
| Reporting and Remediation | Generating reports to demonstrate compliance and taking corrective actions to address identified issues. | Demonstrates accountability and ensures continuous improvement of the security posture. | Compliance reports, vulnerability remediation, configuration changes. |
Landing Zone Deployment Methods
The deployment of a cloud landing zone is a critical step in establishing a secure, compliant, and scalable cloud environment. The choice of deployment method significantly impacts the speed, efficiency, and maintainability of the landing zone. Several methods exist, each with its own strengths and weaknesses, catering to different organizational needs and technical expertise levels.
Automated Deployment Script Examples
Automated deployment scripts are essential for streamlining the landing zone deployment process, promoting consistency, and reducing human error. These scripts leverage Infrastructure as Code (IaC) principles to define and provision cloud resources programmatically.The following are examples, illustrating different IaC approaches, of automated deployment scripts for creating core landing zone components. These are conceptual examples and would need adaptation based on the specific cloud provider (AWS, Azure, GCP, etc.) and the chosen IaC tool (Terraform, CloudFormation, ARM templates, etc.).* Terraform Example (Conceptual): This script might define the following: “`terraform # Terraform script for creating a VPC in AWS resource “aws_vpc” “main” cidr_block = “10.0.0.0/16” tags = Name = “landing-zone-vpc” resource “aws_subnet” “public_subnet_1a” vpc_id = aws_vpc.main.id cidr_block = “10.0.1.0/24” availability_zone = “us-east-1a” tags = Name = “public-subnet-1a” # Further resources would define internet gateways, route tables, security groups, etc.
“` This script, written in Terraform, a popular IaC tool, defines a Virtual Private Cloud (VPC) and a public subnet in AWS. It specifies the CIDR block, availability zone, and tags for each resource. The use of variables and modules allows for reusability and customization. The deployment would involve running the `terraform init`, `terraform plan`, and `terraform apply` commands.* Azure Resource Manager (ARM) Template Example (Conceptual): This example demonstrates an ARM template for creating a resource group and a storage account in Azure.
“`json “$schema”: “https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#”, “contentVersion”: “1.0.0.0”, “resources”: [ “type”: “Microsoft.Resources/resourceGroups”, “apiVersion”: “2020-10-01”, “name”: “landing-zone-rg”, “location”: “eastus” , “type”: “Microsoft.Storage/storageAccounts”, “apiVersion”: “2021-09-01”, “name”: “storagelandingzone”, “location”: “eastus”, “sku”: “name”: “Standard_LRS” , “kind”: “StorageV2”, “properties”: “accessTier”: “Hot” , “dependsOn”: [ “[resourceId(‘Microsoft.Resources/resourceGroups’, ‘landing-zone-rg’)]” ] ] “` This ARM template, written in JSON, defines a resource group and a storage account.
The template specifies the resource type, API version, name, location, SKU, and dependencies. Deployment involves using the Azure CLI or PowerShell to deploy the template.* Google Cloud Deployment Manager Example (Conceptual): This example Artikels a deployment manager configuration for creating a basic network in Google Cloud Platform (GCP). “`yaml resources:
name
landing-zone-network type: compute.v1.network properties: name: landing-zone-network autoCreateSubnetworks: false
name
landing-zone-subnet-1 type: compute.v1.subnetwork properties: name: landing-zone-subnet-1 ipCidrRange: 10.10.0.0/24 network: landing-zone-network region: us-central1 “` This YAML file defines a network and a subnet.
Deployment involves using the `gcloud deployment-manager deployments create` command.These examples illustrate the basic structure of automated deployment scripts. In reality, landing zone scripts are far more complex, encompassing security configurations, identity and access management (IAM) setups, networking configurations, logging and monitoring, and other essential components.
Steps in Deploying a Landing Zone
The deployment process typically involves several key steps, regardless of the chosen method or tool. These steps can be adapted to the specific cloud provider and the desired level of automation.* Planning and Design: Define the requirements for the landing zone, including security, networking, identity, and compliance needs. This involves selecting appropriate services, designing the network topology, and defining security policies.* Environment Setup: Set up the necessary tooling and infrastructure for deployment.
This includes installing the IaC tool, configuring the cloud provider’s CLI, and setting up a version control system (e.g., Git) for managing the deployment scripts.* Script Development: Write the IaC scripts to define and provision the landing zone resources. This involves using the chosen IaC tool to create scripts that define the infrastructure components, such as VPCs, subnets, security groups, IAM roles, and logging configurations.* Testing and Validation: Test the deployment scripts in a non-production environment to ensure they function as expected.
This involves validating the configurations, verifying that resources are created correctly, and testing security policies.* Deployment: Deploy the landing zone to the production environment. This typically involves running the IaC scripts to provision the resources. The deployment process should be automated and repeatable.* Post-Deployment Configuration: Configure the deployed resources according to the organization’s specific requirements.
This may include configuring logging and monitoring, setting up security alerts, and integrating with existing systems.* Monitoring and Management: Continuously monitor the landing zone and manage its resources. This includes monitoring performance, security, and compliance, and making updates and changes as needed.
Step-by-Step Deployment Procedure
A detailed step-by-step procedure, exemplified using Terraform on AWS, could be as follows:* Prerequisites: 1. Install Terraform. 2. Configure AWS credentials. 3.
Choose a suitable code editor or IDE. 4. Establish a Git repository for version control.* Project Setup: 1. Create a new directory for the landing zone project. 2.
Initialize a Terraform project using `terraform init`. 3. Create a main configuration file (e.g., `main.tf`).* Define Infrastructure: Within `main.tf`, define the required AWS resources using Terraform code. This might include:
A VPC with a specified CIDR block.
Public and private subnets across multiple Availability Zones.
An Internet Gateway for public subnet access.
Route tables for subnet routing.
Security groups to control network traffic.
IAM roles and policies for access control.
Logging and monitoring configurations.
* Apply Configuration: 1. Run `terraform plan` to preview the changes Terraform will make. This command provides a detailed view of the resources that will be created, modified, or deleted. 2. Review the plan and confirm the changes.
3. Run `terraform apply` to deploy the landing zone infrastructure. This command executes the plan and creates the resources in AWS. Terraform will prompt for confirmation before applying the changes.* Verification and Testing: 1. Verify the deployment by checking the AWS Management Console.
2. Test connectivity to the created resources. 3. Validate security group rules. 4.
Test IAM access permissions. 5. Verify that logging and monitoring are functioning correctly.* Iterative Development and Updates: 1. Make changes to the Terraform configuration files as needed. 2.
Run `terraform plan` to preview the changes. 3. Run `terraform apply` to apply the updates.* Cleanup (Optional): 1. If the landing zone is no longer needed, run `terraform destroy` to remove the resources. This command removes all resources defined in the Terraform configuration.This procedure is a simplified example.
Real-world deployments would likely include more sophisticated configurations, such as using Terraform modules to encapsulate reusable components, implementing a CI/CD pipeline for automated deployments, and integrating with other tools for configuration management and security.
Landing Zone and Multi-Account Strategy
A well-architected landing zone is fundamentally designed to support and enable a multi-account strategy within a cloud environment. This approach is crucial for achieving robust isolation, enhanced security, and efficient resource management, aligning with best practices for cloud adoption and governance. The landing zone provides the foundational infrastructure and organizational structure necessary to effectively deploy and manage resources across multiple independent cloud accounts.
Facilitation of a Multi-Account Strategy
The landing zone acts as the central orchestrator for a multi-account strategy. It provides the necessary frameworks and tools to establish and manage these accounts.
- Account Provisioning and Management: The landing zone streamlines the creation and management of individual cloud accounts. This includes automated account creation, pre-configured security settings, and standardized resource configurations, reducing manual effort and potential configuration drift.
- Centralized Identity and Access Management (IAM): By integrating with a centralized IAM system, such as AWS IAM Identity Center (formerly AWS Single Sign-On) or Azure Active Directory, the landing zone allows for consistent identity management across all accounts. This simplifies user access control and minimizes the risk of unauthorized access.
- Shared Services and Infrastructure: The landing zone typically houses shared services, such as networking components (VPCs, subnets, transit gateways), logging and monitoring tools, and security services (e.g., security information and event management – SIEM). This centralized approach promotes consistency, reduces operational overhead, and allows for economies of scale.
- Governance and Compliance: The landing zone enforces governance policies and compliance requirements across all accounts. This is achieved through the use of policies, guardrails, and automated compliance checks. This ensures that all resources adhere to the organization’s security and compliance standards.
Resource Management Across Multiple Accounts
Managing resources across multiple accounts requires a strategic approach. The landing zone facilitates this through various mechanisms.
- Infrastructure as Code (IaC): IaC tools, such as Terraform or AWS CloudFormation, are integral to the landing zone. They enable the consistent deployment and management of infrastructure across multiple accounts. This allows for the definition of infrastructure in code, which can be version-controlled, automated, and applied across different accounts.
- Service Control Policies (SCPs): SCPs, available in AWS, provide a mechanism for defining the permissions boundaries for all accounts within an organization. This allows for the enforcement of a consistent security posture across all accounts by restricting the actions that users and roles can perform.
- Cross-Account Access and Communication: The landing zone facilitates secure cross-account communication through mechanisms such as VPC peering, transit gateways, and shared services. This allows resources in different accounts to interact while maintaining network isolation.
- Centralized Logging and Monitoring: Centralized logging and monitoring services, configured within the landing zone, aggregate logs and metrics from all accounts. This provides a unified view of the environment, enabling proactive monitoring, security incident detection, and performance optimization.
Benefits of a Multi-Account Setup: Isolation and Security
A multi-account setup, facilitated by the landing zone, offers significant advantages in terms of isolation and security.
- Enhanced Security Isolation: Each account acts as a security boundary, limiting the blast radius of security incidents. If one account is compromised, the impact is contained within that account, minimizing the risk to other workloads and data.
- Improved Compliance: Separating workloads into different accounts can simplify compliance efforts. For example, sensitive workloads can be isolated in accounts with stricter security controls, making it easier to meet regulatory requirements.
- Resource Quota Management: Each account has its own set of resource quotas. This allows for better control over resource consumption and prevents a single workload from consuming all available resources, potentially impacting other applications.
- Reduced Risk of Accidental Exposure: By default, resources in one account are isolated from resources in other accounts. This reduces the risk of accidental exposure of sensitive data or misconfiguration that could lead to security breaches.
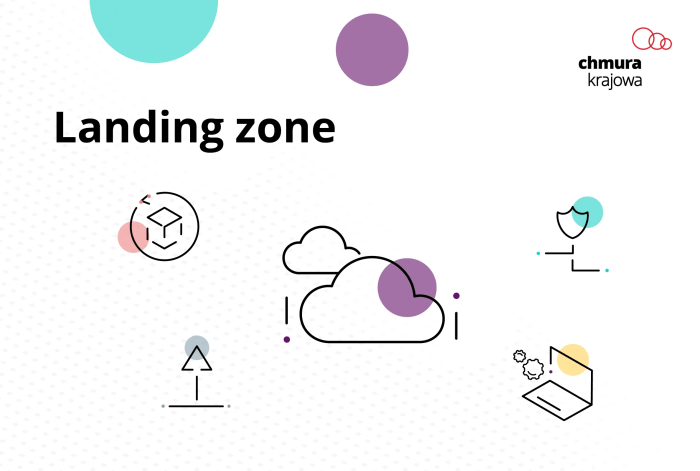
Multi-Account Structure Illustration
Imagine a visual representation of a landing zone’s multi-account structure. The image depicts a hierarchical structure, where the root of the organization is the top level. Underneath this root, several organizational units (OUs) are depicted. Each OU represents a logical grouping of accounts, such as “Security,” “Network,” “Development,” and “Production.” Each OU contains one or more individual cloud accounts. The “Security” OU houses accounts for security logging, auditing, and threat detection.
The “Network” OU contains accounts for networking components like transit gateways and shared services. The “Development” and “Production” OUs contain accounts for application development, testing, and deployment. Arrows indicate the flow of data and access, demonstrating the centralized logging, monitoring, and security controls that span all accounts. A visual key indicates the purpose of each account and the services used, such as IAM, VPC, and security services, which are consistently applied across all accounts.
The structure highlights the separation of concerns, with shared services centralized and individual workloads isolated within their respective accounts.
Landing Zone Evolution and Maintenance
The cloud landing zone, once deployed, is not a static entity. It requires continuous maintenance and evolution to adapt to changing business needs, evolving security threats, and updates to cloud provider services. This section Artikels the ongoing requirements, provides examples of evolution, details best practices for monitoring and troubleshooting, and encapsulates maintenance and evolution strategies.
Ongoing Maintenance Requirements of a Cloud Landing Zone
Maintaining a cloud landing zone is a continuous process, requiring regular attention to ensure its operational effectiveness, security posture, and alignment with organizational policies. This includes tasks such as patching, configuration management, and regular audits.
- Patching and Updates: Cloud providers regularly release updates and security patches for their services. The landing zone must be updated to incorporate these changes. This involves applying patches to operating systems, updating software, and ensuring that underlying infrastructure components are up-to-date.
- Configuration Management: Maintaining consistent configurations across all cloud resources is crucial. This involves regularly reviewing and updating configurations to reflect changes in security policies, compliance requirements, and best practices. Tools like Infrastructure as Code (IaC) are essential for automating configuration management.
- Security Audits and Assessments: Regular security audits and assessments are vital for identifying vulnerabilities and ensuring compliance. These audits should cover all aspects of the landing zone, including network configurations, access controls, and data encryption. The results of these audits should be used to inform updates and improvements.
- Cost Optimization: Cloud environments can be expensive, so regular cost optimization efforts are essential. This includes monitoring resource utilization, identifying unused resources, and right-sizing instances. Cost optimization strategies can significantly reduce cloud spending.
- Compliance Checks: Compliance with industry regulations and organizational policies is a continuous requirement. Regular checks and audits are necessary to ensure the landing zone meets the required compliance standards. This includes monitoring logs, reviewing configurations, and implementing necessary controls.
- Documentation: Maintaining accurate and up-to-date documentation is crucial for all aspects of the landing zone. This includes documentation of the architecture, configurations, security policies, and operational procedures. Updated documentation facilitates troubleshooting, onboarding, and knowledge transfer.
Examples of How to Update and Evolve a Landing Zone Over Time
A landing zone evolves over time to accommodate changes in business needs, technology advancements, and evolving security threats. This section presents examples of how a landing zone can be updated and evolved.
- Adding New Regions: As an organization expands its global presence, it may need to deploy its landing zone in new cloud regions. This involves replicating the landing zone architecture, configuring networking, and establishing connectivity to the new region. For example, a company initially operating in North America might expand to Europe and Asia, necessitating the deployment of landing zones in those regions.
- Implementing New Security Controls: New security threats and vulnerabilities require the implementation of new security controls. This might include deploying new security services, such as Web Application Firewalls (WAFs), intrusion detection systems (IDS), and security information and event management (SIEM) systems. For example, a company might implement a WAF to protect against distributed denial-of-service (DDoS) attacks.
- Adopting New Cloud Services: Cloud providers continuously release new services that can improve performance, reduce costs, or enhance security. The landing zone should be updated to leverage these new services. For example, a company might adopt a new database service to improve performance and scalability.
- Automating New Processes: As an organization matures, it may automate more processes. This could involve automating deployment, configuration, and monitoring. Automation reduces manual effort and improves consistency. For example, a company might automate the deployment of new applications using IaC tools.
- Updating Identity and Access Management (IAM) Policies: IAM policies must be regularly reviewed and updated to reflect changes in user roles, responsibilities, and security requirements. This involves granting and revoking permissions, implementing multi-factor authentication (MFA), and ensuring the principle of least privilege is enforced. For example, a company might update IAM policies to restrict access to sensitive data.
- Improving Cost Optimization Strategies: Cost optimization strategies need to be continuously refined. This includes optimizing resource utilization, right-sizing instances, and leveraging cost-saving features offered by the cloud provider. For example, a company might implement automated instance scaling to reduce costs during periods of low activity.
Best Practices for Monitoring and Troubleshooting a Landing Zone
Effective monitoring and troubleshooting are essential for maintaining a healthy and secure cloud landing zone. This section Artikels best practices.
- Centralized Logging and Monitoring: Implement a centralized logging and monitoring solution to collect and analyze logs from all components of the landing zone. This allows for real-time monitoring, proactive identification of issues, and faster troubleshooting. Examples of tools include CloudWatch (AWS), Azure Monitor (Azure), and Cloud Logging/Monitoring (GCP).
- Proactive Alerting: Configure alerts to notify administrators of critical events, such as security breaches, performance degradation, and system failures. Alerts should be based on predefined thresholds and should be actionable.
- Performance Monitoring: Monitor the performance of all cloud resources, including compute instances, databases, and networks. This includes tracking metrics such as CPU utilization, memory usage, and network latency. Performance monitoring helps to identify bottlenecks and optimize resource utilization.
- Security Monitoring: Implement security monitoring to detect and respond to security threats. This includes monitoring security logs, detecting suspicious activity, and responding to security incidents. Security monitoring tools, such as SIEM systems, are crucial.
- Regular Audits: Conduct regular audits of the landing zone to ensure compliance with security policies and best practices. Audits should cover all aspects of the landing zone, including access controls, network configurations, and data encryption.
- Incident Response Plan: Develop and maintain an incident response plan to guide the response to security incidents and system failures. The plan should Artikel the steps to be taken, the roles and responsibilities of team members, and the communication procedures.
- Testing and Validation: Regularly test and validate the landing zone to ensure that it is functioning correctly and that security controls are effective. This includes testing failover procedures, disaster recovery plans, and security configurations.
- Use of Infrastructure as Code (IaC) for Consistency: IaC tools allow for consistent deployments, making troubleshooting easier. The use of IaC can facilitate the identification of configuration drift and ensure that infrastructure remains in the desired state.
Maintenance and Evolution Using Bullet Points
This section summarizes the key aspects of landing zone maintenance and evolution.
- Regular Updates: Keep software and infrastructure up-to-date with the latest security patches and updates.
- Configuration Management: Maintain consistent configurations across all resources using IaC.
- Security Audits: Conduct regular security audits and assessments.
- Cost Optimization: Monitor and optimize cloud spending.
- Compliance Checks: Ensure ongoing compliance with regulations and policies.
- Documentation: Maintain accurate and up-to-date documentation.
- Evolving to New Regions: Expand the landing zone to new geographical regions as needed.
- Implementing New Security Controls: Adapt to new security threats and vulnerabilities.
- Adopting New Cloud Services: Leverage new services offered by cloud providers.
- Automation: Automate processes for efficiency and consistency.
- IAM Updates: Regularly review and update IAM policies.
- Centralized Monitoring: Implement centralized logging and monitoring.
- Proactive Alerting: Configure alerts for critical events.
- Performance and Security Monitoring: Monitor performance and security metrics.
- Incident Response Plan: Have an established incident response plan.
- Testing and Validation: Regularly test and validate configurations.
Conclusive Thoughts
In conclusion, a landing zone is more than just a starting point; it’s the cornerstone of a successful cloud strategy. By carefully designing and implementing a landing zone, organizations can unlock the full potential of cloud computing, ensuring a secure, efficient, and compliant environment. It provides a scalable, repeatable, and automated foundation that empowers businesses to innovate and thrive in the cloud era.
FAQ Explained
What is the primary purpose of a cloud landing zone?
The primary purpose is to establish a secure, scalable, and compliant foundation for cloud deployments, streamlining resource provisioning and governance.
How does a landing zone improve security?
It enhances security by implementing security best practices, such as centralized identity and access management, network segmentation, and security monitoring from the outset.
Is a landing zone necessary for all cloud deployments?
While not strictly mandatory, a landing zone is highly recommended for any organization planning to deploy applications and services in the cloud, especially for production environments.
Can a landing zone be customized?
Yes, landing zones are highly customizable to meet specific organizational requirements, allowing for tailored configurations and integrations.
How does a landing zone impact cost?
A well-designed landing zone can reduce costs by optimizing resource utilization, automating deployments, and enabling efficient governance and compliance.