Understanding Docker networking concepts is crucial for effectively deploying and managing containerized applications. This guide provides a comprehensive overview of Docker networking, from fundamental principles to advanced configurations and troubleshooting techniques. It explores various network drivers, addressing mechanisms, and security considerations to equip you with the knowledge needed for successful container orchestration.
This detailed exploration will cover topics ranging from basic container communication to advanced concepts like load balancing and custom network topologies. We will also discuss troubleshooting techniques and security best practices to ensure secure and reliable Docker deployments.
Introduction to Docker Networking
Docker networking enables containers to communicate with each other and with the host system. It provides a standardized way for containers to share resources and interact, enhancing the overall efficiency and organization of applications deployed within a Docker environment. This structured approach is crucial for building complex applications that require interaction between multiple containers.Fundamental to Docker networking is the concept of virtual networks.
These networks isolate containers from each other and from the host system’s network, preventing conflicts and enhancing security. The creation of these virtual networks is managed by Docker, simplifying the management of network configurations for developers and administrators.
Fundamental Concepts of Docker Networking
Docker networks establish a virtualized networking environment for containers. This environment is separate from the host’s network, ensuring isolation and preventing conflicts. Network configurations are defined within Docker, abstracting the underlying network complexities from the developer. This abstraction simplifies deployment and management, facilitating seamless interaction between containers.
Docker Networks and Container Communication
Docker networks facilitate communication between containers by assigning them unique network addresses and enabling them to communicate using these addresses. This method allows containers to access each other and shared resources without direct access to the host’s network. This isolation is critical for security and preventing interference between different applications running in containers. Containers on the same network can directly communicate with each other, enabling complex application architectures.
Docker Network Types
Different Docker network types offer varying levels of connectivity and isolation. Understanding these differences is essential for choosing the appropriate network type for specific application needs. These network types cater to different architectural requirements and are a crucial part of Docker’s overall design.
| Network Type | Description | Connectivity | Isolation |
|---|---|---|---|
| Host | Connects containers directly to the host’s network. | High | Low |
| Bridge | Creates a virtual network between containers. | High | Medium |
| Overlay | Creates a virtual network across multiple hosts. | High | High |
A basic diagram illustrating container interaction within a Docker network is shown below:“`+—————–+ +—————–+| Container A |—->| Container B |+—————–+ +—————–+ | | Docker Network V+—————–+| Docker Host |+—————–+“`Container A and Container B are connected through a Docker network.
This network provides a virtual connection, allowing them to communicate with each other. The Docker host manages the network, enabling efficient communication and resource sharing.
Understanding Docker Network Drivers
Docker networking plays a crucial role in enabling containers to communicate with each other and the host system. Understanding the different network drivers available is essential for selecting the appropriate configuration for various application needs. This section delves into the details of Docker network drivers, highlighting their strengths, weaknesses, configurations, and performance characteristics.
Available Docker Network Drivers
Docker offers several network drivers, each with distinct characteristics and use cases. These drivers cater to different communication needs, ranging from simple container-to-container communication to complex scenarios involving external networks. Choosing the right driver is crucial for optimizing performance and security.
- `bridge`: This is the default Docker network driver. It creates a virtual bridge network that connects containers to the host’s network. This driver facilitates communication between containers on the same host machine. It’s straightforward to configure and well-suited for simple applications or development environments. A key strength is its ease of use.
However, it might not be ideal for production deployments involving complex network configurations. No specific configuration is required beyond the default settings.
- `host`: This driver connects containers directly to the host’s network stack. It provides the fastest performance for container-to-container communication because it avoids the overhead of a virtual bridge. This is particularly useful when containers need to access resources on the host’s network. Its simplicity and performance are its key strengths. However, it lacks isolation between containers and the host network, potentially creating security vulnerabilities if not carefully managed.
This driver does not require explicit configuration. It connects containers directly to the host’s network stack.
- `none`: This driver isolates containers from the host network completely. It’s suitable for scenarios where containers require no network access. The lack of network connectivity means no direct communication with other containers or external networks. Its simplicity and isolation are key advantages, but it is unsuitable for any application that requires network connectivity. No configuration is needed beyond specifying the driver.
- `overlay`: This driver is designed for multi-host deployments. It creates a virtual network across multiple hosts, enabling containers on different machines to communicate seamlessly. This is crucial for scaling applications across multiple servers. A key advantage is its ability to support complex multi-host environments. However, its configuration can be more intricate than other drivers.
Configuration involves defining the network’s properties, such as the underlying network and the scope of communication between containers.
- `macvlan`: This driver provides enhanced network isolation and performance by utilizing virtual network interfaces. It offers superior performance compared to the bridge driver, particularly in scenarios requiring high bandwidth or low latency. This is ideal for scenarios requiring high-performance networking, such as microservices deployments. The configuration for macvlan involves setting up the virtual network interface and configuring the necessary IP addresses and routing rules.
Comparison of Network Driver Performance
Performance characteristics differ significantly among the drivers. The `host` driver generally offers the best performance due to its direct connection to the host’s network. The `bridge` driver provides a good balance between performance and simplicity. The `overlay` driver is optimized for multi-host environments, but performance might be slightly lower than the `host` driver for single-host deployments. The `macvlan` driver also exhibits high performance but requires more intricate configurations.
Configuration Details
The configuration requirements vary based on the selected driver. For instance, the `bridge` driver typically requires no specific configuration, while the `overlay` driver demands careful configuration to ensure proper communication across multiple hosts. Each driver has specific parameters that can be customized.
Use Cases
The choice of driver depends on the specific use case. The `bridge` driver is suitable for simple applications and development environments. The `host` driver is best for high-performance scenarios where direct access to the host’s network is required. The `overlay` driver is essential for multi-host deployments. The `macvlan` driver is ideal for high-bandwidth, low-latency applications.
The `none` driver is suitable for use cases where network isolation is a priority.
Container Communication within Networks
Containers residing within a Docker network can communicate with each other seamlessly. This capability is crucial for building complex applications where different services need to interact and exchange data. The underlying mechanisms ensure efficient communication, enabling robust and scalable applications.Effective communication between containers is facilitated by the network infrastructure Docker provides. This infrastructure establishes a virtualized environment where containers can interact without directly accessing the host operating system’s network stack.
This isolation promotes security and prevents conflicts.
Mechanisms for Inter-Container Communication
Docker networks establish a virtual network layer between containers. This allows containers to communicate as if they were on the same physical network. This virtual network layer utilizes a variety of mechanisms, depending on the network driver employed. Common mechanisms include IP address assignment, port mapping, and routing.
IP Addresses and Ports in Container Networking
Each container within a Docker network is assigned a unique IP address. These addresses are part of the virtual network created by the Docker daemon. Containers can communicate with each other using these IP addresses. Port mappings allow containers to expose specific ports for external access or inter-container communication. These ports act as entry points for data exchange between containers.
The combination of IP addresses and ports allows precise routing of network traffic between containers. For example, a web server container might expose port 80, allowing other containers to access it using its assigned IP address.
Resolving Network Issues
Network issues between containers can stem from misconfigurations, incorrect IP assignments, or conflicts in port usage. A systematic approach to troubleshooting these issues is essential. Checking for firewall rules, verifying IP address assignments, and ensuring proper port mappings are crucial steps in diagnosing and resolving communication problems. Comprehensive logging and monitoring tools can help identify the source of network failures.
Detailed error messages often contain valuable clues about the nature of the problem.
Examples of Applications Requiring Specific Network Configurations
Various containerized applications necessitate specific network configurations. Microservices architectures often require precise inter-service communication. For example, a user authentication service needs to communicate with a database service. Similarly, a web application might need to interact with a payment gateway or a message queue. In these scenarios, carefully configured Docker networks ensure seamless communication between services, allowing for a more robust and scalable application.
Database containers often require specific network configurations, such as setting up a firewall to limit external access or enabling communication with application containers on a specific port.
Docker Network Addressing
Docker networks provide a way for containers to communicate with each other and with the host system. A crucial aspect of this communication is how Docker assigns IP addresses and manages the network topology. Understanding this process is essential for ensuring reliable container connectivity and troubleshooting potential issues.
IP Address Assignment
Docker assigns IP addresses to containers within a network based on the chosen network driver and the network configuration. Typically, Docker uses a DHCP-like mechanism, automatically assigning IP addresses from a pre-configured subnet. This automation simplifies container management and deployment. However, users can also configure static IP addresses for specific containers if required. This allows for predictable and consistent network access, especially for containers that need to be accessed by other systems.
Subnet Masks in Docker Networks
Subnet masks define the portion of an IP address that identifies the network and the portion that identifies the host within that network. A subnet mask is crucial for proper network communication. It ensures that data packets are routed correctly to the intended recipient within the network. A typical example in Docker networks would use a /24 subnet mask, meaning the first 24 bits of the IP address identify the network, and the remaining bits identify the host.
Different network drivers might use varying subnet mask sizes.
Configuring Custom IP Ranges
Users can configure custom IP ranges for Docker networks using Docker network creation commands. This allows for greater control over the network addressing scheme. For example, using a command like `docker network create –subnet=192.168.100.0/24 my-network` will create a network with the specified subnet. This is particularly useful when deploying containers in environments with existing network infrastructure or when a specific IP range is required for compatibility reasons.
Impact of Network Configuration on Container Accessibility
The network configuration directly impacts how containers can communicate with each other and with external systems. Incorrect network configuration can lead to connectivity issues. For instance, if a container’s IP address is not correctly configured or the subnet mask is incorrect, the container might be inaccessible from other containers or external hosts. This highlights the importance of accurate network configurations for seamless communication.
Troubleshooting Container Network Connectivity Issues
Troubleshooting container network connectivity problems often involves verifying the IP addresses of containers, checking the network configuration, and examining logs for any errors. Tools like `docker inspect` and `docker network inspect` can provide valuable information about the network configuration of containers and networks. If connectivity issues persist, systematically checking these elements can often pinpoint the source of the problem.
Advanced Docker Networking Concepts
Docker networking extends beyond basic container communication, enabling sophisticated configurations for robust and scalable applications. This section explores advanced features like load balancing, network aliases, external network integration, custom topologies, and security considerations, enhancing the deployment and management of Dockerized services.
Docker Load Balancing
Docker Swarm mode provides built-in support for load balancing across multiple containers. This allows distributing incoming requests across multiple instances of an application, improving performance and availability. Load balancing distributes traffic based on various factors like CPU utilization, response time, or even a round-robin approach. This ensures that no single container is overloaded, maintaining the system’s responsiveness and reliability.
Docker Network Aliases
Network aliases provide a way to assign human-readable names to containers within a Docker network. These aliases act as alternative names for containers, facilitating easier identification and management. Instead of using IP addresses, administrators can refer to containers by their aliases, improving readability and reducing the cognitive load during troubleshooting and maintenance. For example, a web server container might be given the alias “webserver01”, simplifying management and configuration.
Docker Network Integration with External Networks
Docker networks can seamlessly integrate with existing external networks. This capability is crucial for connecting Docker containers to external services like databases or load balancers residing outside the Docker environment. Containers can access these external resources as if they were part of the Docker network, facilitating seamless communication and data exchange between internal and external systems. This integration enhances the overall flexibility and scalability of the Docker deployment.
Custom Docker Network Topologies
Docker allows the creation of custom network topologies, enabling specific communication patterns between containers. These topologies can be tailored to suit the requirements of the application. For example, a clustered application might require a mesh network topology, where every container can directly communicate with every other container. A hub-and-spoke network topology could be suitable for scenarios where communication flows through a central container.
This flexibility caters to diverse application architectures and communication requirements.
Docker Networking Security Features
Docker provides various security features to protect containers and their network interactions. These include network policies, which define which containers can communicate with each other, limiting potential security breaches. These policies can control traffic flow, restricting communication between containers based on predefined rules. This ensures that only authorized containers can interact, mitigating the risk of unauthorized access and data breaches.
Furthermore, Docker’s use of IP address ranges and port restrictions enhances network security by controlling access to sensitive resources.
Practical Applications of Docker Networking
Docker networking empowers the creation of complex, interconnected applications by providing a streamlined way to manage communication between containers. This facilitates the deployment and management of microservices architectures, allowing for greater flexibility, scalability, and maintainability compared to traditional monolithic applications. The ability to isolate and control network traffic within a Docker environment is crucial for security and performance optimization.Understanding how to configure and utilize Docker networks is essential for successfully deploying and managing applications composed of multiple containers.
This section explores practical scenarios, focusing on configuring Docker networks for microservices, integrating them with existing infrastructure, and ensuring robust network security within a Docker environment.
Multi-Container Application Scenario
A common use case involves a web application (e.g., Node.js) that interacts with a database (e.g., PostgreSQL). These applications are frequently structured as microservices, where each service runs within its own container.A web application, serving as the front end, would retrieve data from a database, and the database would be responsible for data storage. To achieve this, the containers must be connected to a network.
A user requesting information from the web application will trigger communication through the network between the web application container and the database container. The configuration of the network is essential for efficient data exchange and overall application functionality.
Network Configuration for the Scenario
To establish communication between the web application and database containers, a Docker network is required. This network provides a virtualized network space that allows containers to communicate with each other.
- Network Creation: A Docker network, such as a bridge network, or a custom network can be created to encapsulate the application’s containers.
- Container Connection: Both the web application and database containers are connected to this network. This enables direct communication between them.
- IP Addressing: The Docker daemon assigns unique IP addresses to each container within the network. The web application container will be able to use the IP address of the database container to communicate with it.
Microservices with Docker Networks
Docker networks are ideal for microservices architectures. Each microservice is packaged as a container, and the network facilitates communication between these services. This modular approach allows for independent scaling and development of individual services.
- Independent Deployment: Each microservice container can be deployed and managed independently. This flexibility enables rapid iteration and scalability.
- Enhanced Scalability: The network facilitates communication between the containers, enabling seamless scaling of individual services based on demand.
- Improved Maintainability: Individual microservices can be updated or replaced without impacting other components in the system, leading to increased maintainability.
Integrating with Existing Infrastructure
Docker networks can seamlessly integrate with existing infrastructure. A Docker network can be connected to an existing network to allow containers to communicate with external services or hosts.
- External Service Access: Docker networks can connect containers to external services like load balancers, message queues, or other infrastructure components.
- Bridged Connections: A Docker bridge network provides a connection to the host’s network, enabling communication with external systems.
- Custom Networks: Custom networks offer more control over the networking configuration, enabling integration with complex network topologies.
Network Security in Docker
Robust network security is paramount in a Docker environment. Network isolation and access control are crucial to protect against vulnerabilities.
- Security Considerations: Network security is a crucial aspect of Docker containerization. Appropriate access control mechanisms must be implemented to prevent unauthorized access to containers.
- Network Segmentation: Docker networks enable the segmentation of containers, limiting potential attack vectors.
- Access Control: Implement robust access controls to restrict container communication and enforce policies.
Troubleshooting Docker Networking Problems
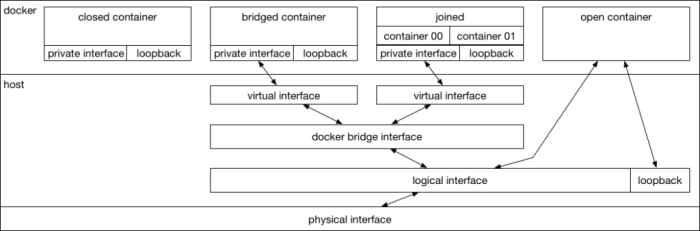
Troubleshooting Docker networking issues can be a complex but manageable task. Understanding the common causes and systematic diagnostic methods is crucial for effective resolution. This section details common problems, their causes, and steps for isolation and repair, ensuring smooth container communication and overall system stability.Effective troubleshooting requires a methodical approach. Identifying the specific problem is the first step.
This involves carefully reviewing logs, observing container behavior, and checking network configurations. A detailed understanding of the Docker networking stack and its interactions with other network components is essential for effective diagnosis and resolution.
Common Docker Networking Issues
Various issues can disrupt Docker network functionality. These include problems with network configuration, driver mismatches, and conflicts with other networking components. Careful attention to detail and a systematic approach to diagnosis and resolution are key to successful troubleshooting.
- Misconfigured Docker Networks: Incorrectly configured Docker networks can lead to connectivity problems between containers. Incorrect network names, IP ranges, or gateway settings can all cause issues. Verification of network settings and proper configuration of bridges and routing tables is essential.
- Driver-Specific Issues: Different Docker network drivers have varying behaviors and limitations. Issues can arise if the chosen driver is incompatible with the specific network configuration or if there are driver-related bugs. Careful consideration of the chosen driver and its suitability for the task is crucial.
- Port Mapping Errors: Problems with port mappings can prevent external access to container services. Incorrect port mappings or firewall rules can lead to this problem. Verifying the mapping and checking the firewall configuration is essential for resolution.
- DNS Resolution Problems: Containers might not be able to resolve hostnames if the DNS configuration is faulty. Incorrect DNS server settings or misconfigurations in the network setup can prevent resolution. Checking DNS resolution processes and configuring appropriate DNS servers within the Docker network is crucial.
- IP Address Conflicts: If multiple containers or network components are assigned the same IP address, conflicts can arise. This can lead to communication failures. Checking for duplicate IP addresses and ensuring unique assignments within the network is critical.
Diagnosing and Resolving Networking Problems
A systematic approach to diagnosing and resolving networking problems is essential. This involves using diagnostic tools and logging to pinpoint the issue’s source and implementing appropriate fixes. Thorough understanding of Docker network logs, container logs, and network monitoring tools are essential.
- Inspect Docker Networks: Using `docker network inspect
` allows detailed inspection of network configurations. This helps identify any misconfigurations or inconsistencies. - Examine Container Logs: Container logs provide insights into errors or exceptions encountered during network communication. These logs often indicate the root cause of the networking issues.
- Check Network Connectivity: Verify connectivity between containers using tools like `ping` and `tcpdump`. These tools can identify network connectivity issues and diagnose the exact point of failure.
- Isolate the Problem: Gradually isolate the affected components or containers to identify the specific source of the problem. This involves disabling or removing certain components to determine their impact on network communication.
- Review Docker Compose Files (if applicable): For applications using Docker Compose, examine the configuration files for any misconfigurations or inconsistencies that might affect networking.
Common Errors and Their Interpretation
Understanding common errors is crucial for effective troubleshooting. Analyzing error messages helps to identify the underlying problem.
- “Connection refused”: This error often indicates that the container is not listening on the specified port or that there’s a problem with the network configuration. Double-checking the port mapping and the container’s listening state is crucial.
- “No route to host”: This error suggests that there’s no valid route configured for reaching the destination host or container. Verify the network settings and ensure that routes are correctly established between the involved components.
- “Connection timed out”: This error indicates that the connection request took longer than expected to be established. Checking the network latency and ensuring proper connectivity between containers is necessary.
Potential Conflicts with Other Networking Components
Conflicts with other networking components can disrupt Docker network operations. Identifying and resolving these conflicts is crucial for stable operation.
- Firewall Rules: Incorrect firewall rules can block network traffic between containers or prevent external access to container services. Review and adjust firewall rules to allow necessary network traffic.
- Network Interfaces: Conflicts with other network interfaces or virtual network interfaces can cause communication failures. Ensure that the network interface assigned to the Docker network is functioning correctly and not interfering with other network services.
Steps to Isolate and Fix Specific Networking Problems
A structured approach to isolating and fixing problems ensures that the issue is addressed effectively. This involves systematic identification and resolution of the problem’s source.
- Identify the Affected Components: Pinpointing the containers or network components experiencing problems is the first step.
- Verify Network Configuration: Thoroughly review the Docker network configuration and compare it to the expected setup.
- Implement Corrections: Apply necessary corrections to the network configuration, such as adjusting IP addresses, port mappings, or firewall rules.
- Test and Validate: Verify that the corrections have resolved the problem by testing connectivity between containers and external services.
Security Considerations in Docker Networking
Docker networking, while offering significant advantages in container orchestration, introduces security considerations that must be addressed to prevent vulnerabilities and maintain a robust environment. Improperly configured networks can expose containers to attacks and compromise the entire system. Therefore, meticulous attention to security best practices is crucial for a secure Docker deployment.Understanding the potential security implications and employing proactive measures to mitigate risks is paramount.
Effective security strategies involve isolating containers, controlling network access, and regularly auditing configurations. This approach helps to prevent unauthorized access, data breaches, and other security incidents.
Security Implications of Docker Networking
Docker containers, when deployed in a network, share resources and communicate with each other. This inherent interconnectedness, while beneficial for application development, introduces potential security vulnerabilities if not managed carefully. Misconfigurations can lead to unauthorized access to sensitive data within containers, impacting the entire host system.
Securing Container Communication
Establishing secure communication channels between containers is essential. Employing network security tools such as firewalls, encryption protocols, and access controls is critical. These measures help prevent unauthorized access to container resources and sensitive data. Implementing strong authentication mechanisms and access controls restricts communication to only authorized containers.
Protecting Against Network Attacks
Docker networking can be a target for various network attacks, including denial-of-service (DoS) attacks, man-in-the-middle (MitM) attacks, and unauthorized access attempts. Implementing robust security measures, including intrusion detection systems (IDS) and intrusion prevention systems (IPS), helps detect and prevent malicious activity. Regularly updating Docker and associated components with the latest security patches minimizes vulnerabilities.
Best Practices for Securing Docker Networks
Implementing strong security practices in Docker networks involves a multi-layered approach. Use network namespaces to isolate containers and restrict their access to only necessary resources. Utilize network policies to define allowed communication between containers, limiting exposure and preventing unwanted interactions. Employing encryption for sensitive data transmitted between containers enhances data confidentiality.
Vulnerabilities and Potential Risks in Docker Networking
Potential vulnerabilities in Docker networking include misconfigurations of network settings, lack of proper access controls, and insufficient security monitoring. These issues can expose containers to various attacks. Using default configurations without careful review and customization can create significant security risks. Failure to monitor network traffic and container activities for suspicious behavior can leave systems vulnerable.
Docker Networking Use Cases and Examples
Docker networking provides a flexible and powerful mechanism for connecting containers, enabling them to communicate and share resources effectively. This flexibility translates to diverse use cases, making Docker a valuable tool for various applications. Understanding these use cases helps in designing efficient and scalable architectures.Real-world applications often require complex interactions between different services running within containers. Docker networks offer a robust solution to orchestrate these interactions, ensuring reliable communication and data exchange.
This is particularly relevant in microservices architectures where independent components need to communicate seamlessly.
Web Applications with Multiple Services
Docker networks are crucial for deploying web applications with multiple services, such as a web server, database, and caching layer. These services typically need to communicate with each other to function correctly. A well-designed Docker network ensures that these components can communicate reliably, providing a consistent environment. For example, a web application might use a separate network for the web server containers and a separate network for the database containers.
This approach allows for better isolation and security.
Microservices Architectures
Microservices architectures are increasingly popular due to their modularity and scalability. Docker networks are ideally suited for this approach. Each microservice can run in its own container, connected through a Docker network. This allows for independent deployment, scaling, and maintenance of individual services. The network provides the communication channels for inter-service interactions.
Database and Application Integration
Docker networks facilitate seamless integration between databases and applications. A dedicated network can connect database containers to application containers, enabling secure and efficient data exchange. This isolates database traffic from the application, enhancing security and preventing unintended exposure. An example could be a web application that needs to query a database. The application container can access the database container through the Docker network, without needing to know the exact IP address of the database.
CI/CD Pipelines
Docker networks can also be used in CI/CD pipelines to facilitate communication between different stages of the build process. A separate network can connect build containers to testing containers and deployment containers, allowing for seamless data transfer and efficient workflow. This approach improves the overall efficiency of the CI/CD process, reducing latency and streamlining the deployment process.
Containerized Data Processing
For data processing tasks, Docker networks can connect containers running data processing jobs with containers holding the necessary data sets. This enables a distributed and efficient data processing workflow. This is especially useful for complex data analysis or machine learning tasks.
Table of Use Cases
| Use Case | Example | Benefits | Drawbacks |
|---|---|---|---|
| Web Application | A web application with a front-end, API, and database | Improved organization, scalability, and security | Complexity in managing multiple networks |
| Microservices | An e-commerce platform with separate services for inventory, payment, and user accounts | Enhanced flexibility, independent scaling, and easier maintenance | Potential for increased complexity in inter-service communication |
| Database/Application | A web application accessing a relational database | Secure and efficient data exchange, isolated communication channels | Requires careful planning for network configuration |
Last Recap
In summary, mastering Docker networking empowers developers to build complex, scalable, and secure applications using containers. This comprehensive guide has provided a detailed roadmap to navigate the intricacies of Docker networking, enabling efficient container communication, management, and troubleshooting. By understanding these concepts, you’ll be well-equipped to leverage the full potential of Docker for your projects.
Answers to Common Questions
What are the common Docker networking issues?
Common Docker networking issues include conflicts with other networking components, incorrect IP address configurations, port conflicts, and problems with network drivers. Careful configuration and troubleshooting are essential to address these issues.
How can I secure container communication within a Docker network?
Securing container communication involves employing strong authentication mechanisms, using network firewalls, and implementing access control lists. This ensures that only authorized containers can communicate with each other.
What are the different types of Docker network drivers?
Common Docker network drivers include “bridge,” “host,” “overlay,” and “none.” Each driver has its own characteristics and use cases, impacting performance and configuration requirements.
How do Docker networks integrate with external networks?
Docker networks can integrate with external networks through various methods, such as using a Docker bridge or overlay network. This integration allows containers to access resources and services on the external network.