Embarking on a journey through the world of containerization, it’s crucial to understand that securing your runtime environment is not just a best practice, but a necessity. This guide delves into the critical aspects of runtime security, offering insights into safeguarding your containerized applications from a multitude of threats. We’ll explore the core principles, tools, and techniques required to build a robust and resilient security posture for your container deployments.
This document provides a detailed roadmap, covering everything from understanding the fundamentals of container runtime security to implementing advanced techniques and ensuring compliance. You’ll learn how to select the right security tools, implement image scanning, monitor for threats, secure your network, harden your host OS, and enforce the principle of least privilege. Moreover, we will examine the critical role of auditing, logging, vulnerability management, and zero-trust architectures in bolstering your container security posture.
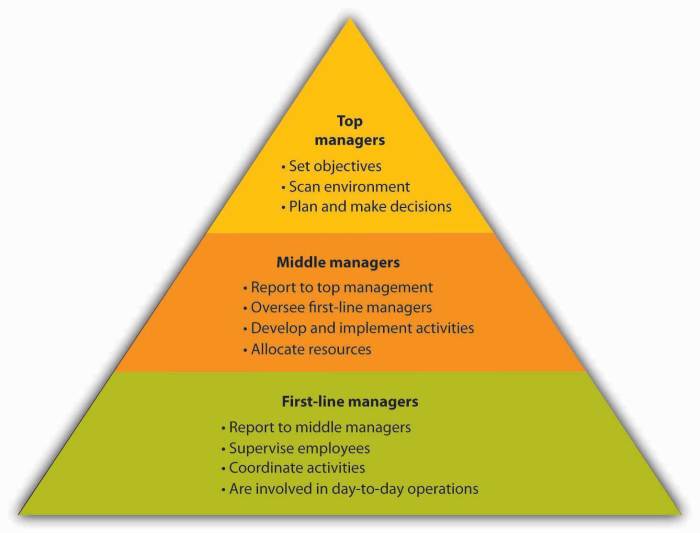
Understanding Container Runtime Security
Container runtime security is crucial for protecting applications deployed in containerized environments. It focuses on securing the execution phase of containers, ensuring that running containers behave as expected and are protected from malicious activities. This proactive approach helps to mitigate risks and maintain the integrity of containerized applications throughout their lifecycle.
Fundamental Principles of Container Runtime Security
Container runtime security is built upon several key principles that work together to create a secure environment. These principles guide the design and implementation of security measures to protect containers.
- Least Privilege: This principle dictates that containers should be granted only the minimum necessary permissions to function. This limits the potential damage from a compromised container. For example, a web server container should not have root privileges unless absolutely necessary, and should only be able to access the specific files and network ports it needs.
- Isolation: Containers should be isolated from each other and the underlying host operating system. This isolation prevents a compromised container from affecting other containers or the host. Containerization technologies like Docker and Kubernetes utilize kernel features such as namespaces and cgroups to achieve this isolation.
- Immutability: The container image should be immutable, meaning it should not be altered after it is built. This helps to ensure that the container always runs the same code and configuration, reducing the risk of vulnerabilities. This principle is often achieved through the use of image registries and build processes that prevent unauthorized modifications.
- Monitoring and Logging: Continuous monitoring and logging of container activity are essential for detecting and responding to security incidents. This includes monitoring network traffic, system calls, and resource usage. Log data should be collected and analyzed to identify suspicious behavior.
- Vulnerability Scanning: Regular scanning of container images for known vulnerabilities is a critical component of runtime security. This allows you to identify and address security flaws before they can be exploited. Vulnerability scanners compare the container image’s components against a database of known vulnerabilities.
Common Threats Targeting Container Runtimes
Container runtimes are attractive targets for attackers, and several common threats can compromise the security of containerized applications. Understanding these threats is crucial for implementing effective security measures.
- Container Escape: This involves an attacker breaking out of a container’s isolation and gaining access to the host operating system or other containers. This can be achieved through exploiting vulnerabilities in the container runtime or misconfigurations. A successful container escape can lead to complete system compromise.
- Malware Injection: Attackers may inject malicious code into a running container, such as through compromised dependencies or vulnerabilities in the application code. This malware can then be used to steal data, disrupt services, or launch further attacks.
- Denial of Service (DoS) Attacks: Attackers can attempt to overwhelm a container’s resources, such as CPU, memory, or network bandwidth, leading to a denial of service. This can be achieved by sending excessive requests or exploiting vulnerabilities that consume excessive resources.
- Privilege Escalation: Attackers may attempt to gain elevated privileges within a container, allowing them to access sensitive data or perform unauthorized actions. This can be achieved by exploiting vulnerabilities or misconfigurations.
- Supply Chain Attacks: Attackers may compromise the software supply chain, injecting malicious code into container images or dependencies. This can lead to widespread compromise of containerized applications. For example, an attacker could compromise a public Docker image and inject malware into it.
Importance of Runtime Security Compared to Other Security Layers
Container security is not a single layer but a multi-layered approach, with runtime security playing a vital role alongside other security measures. The importance of runtime security stems from its focus on the active protection of running containers.
- Complementary to Other Layers: Runtime security complements other security layers, such as image scanning, network security, and host security. Image scanning identifies vulnerabilities before deployment, network security controls traffic, and host security protects the underlying infrastructure.
- Real-time Protection: Runtime security provides real-time protection against threats that are actively targeting running containers. This includes detecting and blocking malicious activities as they occur. This proactive approach helps to minimize the impact of security incidents.
- Mitigating Zero-Day Vulnerabilities: Runtime security solutions can help mitigate the impact of zero-day vulnerabilities, which are vulnerabilities that are not yet known to the public. By monitoring container behavior and detecting suspicious activity, runtime security can help to identify and respond to attacks that exploit these vulnerabilities.
- Dynamic Environment Protection: Container environments are dynamic, with containers being created, destroyed, and scaled frequently. Runtime security solutions can adapt to these changes and provide continuous protection. This ensures that security is maintained even as the environment evolves.
- Defense-in-Depth: Implementing runtime security as part of a defense-in-depth strategy adds an extra layer of protection. Even if other security measures fail, runtime security can help to detect and prevent attacks, reducing the overall risk. This layered approach provides a more robust security posture.
Selecting the Right Runtime Security Tools
Choosing the appropriate runtime security tools is critical for effectively protecting containerized applications. The selection process involves understanding the available tool types, evaluating their capabilities, and aligning them with the specific security needs of your environment. This section provides a comprehensive guide to help you navigate this important decision.
Types of Container Runtime Security Tools
Container runtime security tools are diverse, each focusing on different aspects of protection. Understanding these categories is the first step in selecting the right solution.* Container Security Scanning: These tools analyze container images for vulnerabilities, malware, and misconfigurations before deployment. They typically integrate into the CI/CD pipeline to prevent compromised images from reaching production. Examples include tools that scan for known vulnerabilities in base images and installed packages, ensuring that containers are built from a secure foundation.* Runtime Monitoring and Threat Detection: These tools monitor container activity in real-time, identifying and responding to suspicious behavior.
They use techniques like behavioral analysis and anomaly detection to identify threats such as unauthorized access, privilege escalation, and malicious network traffic. These tools often provide alerts and automated responses to mitigate potential security incidents.* Container Network Security: This category focuses on securing the network communication between containers and other services. They provide features like network segmentation, micro-segmentation, and intrusion detection/prevention systems specifically designed for containerized environments.
This helps to isolate containers and control network traffic, reducing the attack surface.* Container Host Security: These tools focus on securing the underlying host operating system where containers run. They provide features like host intrusion detection, system call monitoring, and file integrity monitoring to protect the host from compromise. Ensuring the security of the host is crucial, as a compromised host can lead to the compromise of all running containers.* Compliance and Auditing Tools: These tools help organizations meet compliance requirements by providing visibility into container security posture.
They generate reports, audit logs, and facilitate compliance with regulations such as PCI DSS, HIPAA, and GDPR. This ensures that container deployments meet the necessary regulatory standards.
Comparison of Open-Source and Commercial Runtime Security Solutions
Several open-source and commercial solutions are available for container runtime security. Each has its strengths and weaknesses, making it crucial to compare them based on your specific needs. The following table provides a comparative analysis of key features.“`html
| Feature | Open-Source Solutions | Commercial Solutions | Description |
|---|---|---|---|
| Cost | Generally free of charge, with potential costs for support and integration. | Subscription-based or per-use licensing fees. | Open-source tools offer a cost-effective entry point but may require internal expertise. Commercial solutions offer comprehensive features and support, but at a cost. |
| Ease of Deployment & Management | Can be complex to deploy and manage, often requiring significant configuration and expertise. | Typically easier to deploy and manage, with user-friendly interfaces and automated features. | Commercial tools often streamline deployment and management, reducing the burden on security teams. |
| Feature Set | Feature sets vary widely; may require integrating multiple tools to achieve comprehensive security. | Often offer a comprehensive suite of features, including vulnerability scanning, runtime monitoring, and compliance reporting. | Commercial solutions often provide a more complete set of security features out of the box. |
| Support & Documentation | Community support and documentation; may require more self-service and troubleshooting. | Dedicated support teams, comprehensive documentation, and often professional services. | Commercial tools offer robust support and documentation, which can be invaluable for complex deployments. |
| Scalability | Scalability can be challenging, requiring careful planning and configuration. | Designed for scalability, supporting large-scale container deployments with ease. | Commercial solutions are often optimized for scalability, ensuring performance even in large environments. |
| Integration | May require custom integration with other security tools and CI/CD pipelines. | Seamless integration with other security tools, CI/CD pipelines, and cloud platforms. | Commercial tools often provide pre-built integrations, simplifying the security workflow. |
| Examples | Examples include: Falco, Sysdig Open Source, Trivy, and Anchore Engine. | Examples include: Sysdig Secure, Aqua Security Platform, Palo Alto Networks Prisma Cloud, and Twistlock (acquired by Palo Alto Networks). | This lists prominent open-source and commercial tools available in the market. |
“`This table provides a high-level comparison. Each tool offers unique features and capabilities. Consider your specific needs and evaluate each solution based on the criteria Artikeld below.
Criteria for Choosing the Best Tool
Selecting the right container runtime security tool requires a careful assessment of several factors.* Security Needs and Risk Profile: Identify the specific threats your organization faces and the level of risk you are willing to accept. Different tools address different types of threats, so your choice should align with your risk profile. For example, organizations handling sensitive data might prioritize tools with robust runtime monitoring and intrusion detection capabilities.* Container Orchestration Platform: The tool must integrate seamlessly with your container orchestration platform (e.g., Kubernetes, Docker Swarm).
Consider factors such as compatibility, ease of integration, and the availability of pre-built integrations. For example, if you use Kubernetes, a tool with native Kubernetes support will simplify deployment and management.* Scalability and Performance: The tool should be able to scale to meet the demands of your containerized environment without impacting performance. Consider the tool’s resource consumption and its ability to handle a large number of containers and events.
Real-world examples show that some tools can significantly impact container performance if not properly configured.* Ease of Use and Management: Choose a tool that is easy to deploy, configure, and manage. Consider factors such as the user interface, documentation, and the availability of automated features. A user-friendly tool will reduce the burden on your security team and enable faster incident response.* Integration Capabilities: The tool should integrate with your existing security tools and CI/CD pipelines.
This allows you to centralize security management and automate security workflows. Look for tools that offer integrations with your SIEM, vulnerability scanners, and other security solutions.* Compliance Requirements: If you need to comply with specific regulations (e.g., PCI DSS, HIPAA), ensure the tool supports the required compliance standards. Consider the tool’s reporting capabilities and its ability to generate audit logs.* Support and Documentation: Evaluate the availability of support and documentation.
Commercial tools typically offer dedicated support teams, while open-source tools rely on community support. Consider the quality of the documentation and the responsiveness of the support team.* Cost: Compare the cost of different tools, considering both the upfront and ongoing costs. Evaluate the value proposition of each tool and determine whether the benefits outweigh the costs. Remember to factor in the cost of training and the time required for implementation and management.
Implementing Container Image Scanning
Container image scanning is a crucial element of a robust container runtime security strategy. By proactively identifying vulnerabilities within container images, organizations can significantly reduce their attack surface and improve their overall security posture. This section will explore the practical aspects of implementing image scanning, focusing on its integration into the CI/CD pipeline, configuration for vulnerability detection, and the process for addressing identified issues.
Integrating Image Scanning into the CI/CD Pipeline
Integrating image scanning into the CI/CD pipeline automates the vulnerability assessment process, ensuring that container images are scanned before they are deployed to production. This proactive approach allows for early detection and remediation of security flaws.
Here’s how to integrate image scanning:
- Choose a Scanning Tool: Select a container image scanning tool that aligns with your requirements and infrastructure. Popular choices include:
- Trivy: A simple and fast vulnerability scanner, ideal for local development and CI/CD pipelines.
- Anchore Engine: A comprehensive tool that provides detailed vulnerability analysis, policy enforcement, and image certification.
- Aqua Security: A commercial platform offering advanced image scanning, runtime protection, and vulnerability management.
- Snyk: A developer-first security platform that integrates with various CI/CD systems and provides vulnerability scanning for container images and dependencies.
- Automate Scanning within the Pipeline: Configure the chosen scanning tool to run automatically as part of your CI/CD pipeline. This can be achieved by adding specific tasks or steps to your pipeline configuration file (e.g., `Jenkinsfile`, `.gitlab-ci.yml`, `azure-pipelines.yml`).
- Define Scanning Triggers: Determine the triggers for image scanning. Common triggers include:
- On every code commit: This ensures that every new image build is scanned for vulnerabilities.
- On image build completion: Scanning is performed after the image is built and tagged.
- Scheduled scans: Periodic scans can be scheduled to detect vulnerabilities that may be introduced over time.
- Configure Output and Reporting: Set up the pipeline to generate reports detailing the scan results. The reports should include:
- Identified vulnerabilities: Lists of vulnerabilities, including severity levels (e.g., critical, high, medium, low).
- Affected packages: Information on the specific packages or libraries affected by the vulnerabilities.
- Remediation advice: Recommendations on how to address the identified vulnerabilities (e.g., upgrading packages, applying patches).
- Implement Failure Conditions: Configure the pipeline to fail if critical or high-severity vulnerabilities are detected. This prevents the deployment of vulnerable images.
Configuring Image Scanning to Detect Vulnerabilities
Configuring image scanning involves setting up the tool to scan for vulnerabilities, defining the scope of the scan, and specifying the criteria for reporting and remediation. Effective configuration is essential for obtaining accurate and actionable results.
Here’s how to configure image scanning:
- Define Scanning Scope: Determine the scope of the scan. This typically includes:
- Base images: Scan the base images used to build your container images.
- Application dependencies: Scan the packages and libraries used by your applications.
- Operating system packages: Scan the operating system packages installed within the container image.
- Set Vulnerability Severity Thresholds: Define the minimum severity level for vulnerabilities that should be reported. This allows you to focus on the most critical issues. For example, you might configure the scanner to report all critical and high-severity vulnerabilities.
- Configure Policy Enforcement: Implement policies to enforce security best practices. Policies can be used to:
- Block images with critical vulnerabilities: Prevent the deployment of images that contain vulnerabilities above a certain severity level.
- Enforce the use of approved base images: Ensure that only trusted base images are used.
- Require specific package versions: Mandate the use of specific versions of packages to mitigate known vulnerabilities.
- Integrate with Vulnerability Databases: Ensure the scanning tool is integrated with up-to-date vulnerability databases (e.g., the National Vulnerability Database (NVD), or vendor-specific databases). This ensures that the scanner has the latest information on known vulnerabilities.
- Customize Scanning Rules: Many scanning tools allow you to customize scanning rules to meet your specific needs. This can include:
- Ignoring false positives: Configure the scanner to ignore vulnerabilities that are not relevant to your environment.
- Defining custom vulnerability checks: Create custom checks to detect vulnerabilities that are not covered by the standard vulnerability databases.
Addressing Vulnerabilities Identified During Image Scans
Once vulnerabilities are identified, it’s essential to have a well-defined process for addressing them. This process should involve prioritization, remediation, and retesting.
Here’s a structured approach to addressing vulnerabilities:
- Prioritize Vulnerabilities: Prioritize vulnerabilities based on their severity and the potential impact on your application and infrastructure. Critical and high-severity vulnerabilities should be addressed first.
- Remediate Vulnerabilities: Take steps to fix the identified vulnerabilities. Common remediation actions include:
- Updating Packages: Upgrade vulnerable packages to the latest versions that include security patches.
- Applying Patches: Apply security patches provided by the package maintainers.
- Rebuilding Images: Rebuild the container images with the updated packages or patches.
- Mitigation Strategies: Implement mitigating controls if a direct fix is not immediately available (e.g., network segmentation to limit access to vulnerable components).
- Retest Images: After remediation, retest the container images to ensure that the vulnerabilities have been successfully addressed. This can be done by running the image scanning tool again.
- Track and Monitor Vulnerabilities: Implement a system for tracking and monitoring vulnerabilities. This can include:
- Maintaining a vulnerability log: Record all identified vulnerabilities, remediation actions, and retesting results.
- Generating reports: Regularly generate reports to track the progress of vulnerability remediation efforts.
- Setting up alerts: Configure alerts to notify you of new vulnerabilities or changes in the severity of existing vulnerabilities.
- Automate Remediation: Whenever possible, automate the remediation process. This can include:
- Automated package updates: Integrate package update mechanisms into your CI/CD pipeline.
- Automated image rebuilding: Automatically rebuild container images after package updates or patch deployments.
Runtime Monitoring and Threat Detection
Implementing robust runtime monitoring and threat detection is crucial for maintaining the security posture of your containerized applications. This involves continuous observation of container activities, analysis of collected data, and automated responses to identified threats. Effectively implementing these practices helps to identify and mitigate potential security breaches in real-time, ensuring the integrity and availability of your containerized environment.
Implementing Runtime Monitoring for Container Activities
Implementing runtime monitoring involves several key steps. It begins with selecting appropriate monitoring tools, configuring these tools to collect relevant data, and establishing a centralized system for data aggregation and analysis. This system should provide real-time visibility into container behavior, enabling proactive identification of anomalies and potential security threats. The chosen tools should also integrate with existing security infrastructure for seamless alert management and response.To successfully implement runtime monitoring, consider the following points:
- Choose appropriate monitoring tools: Select tools that are specifically designed for container environments. Popular choices include Falco, Sysdig, and commercial solutions like Aqua Security and Twistlock (now Palo Alto Networks). These tools offer container-aware features, such as the ability to monitor container-specific events and identify suspicious activities.
- Configure data collection: Define which data points to monitor, including system calls, network traffic, file access, and process execution. Configure the monitoring tools to capture these events and transmit them to a centralized logging and analysis platform.
- Establish a centralized logging and analysis platform: Aggregate logs and metrics from all containers into a centralized platform, such as the Elastic Stack (Elasticsearch, Logstash, Kibana), Splunk, or cloud-based services like Amazon CloudWatch or Google Cloud Logging. This platform should provide the capabilities for searching, analyzing, and visualizing the collected data.
- Set up alerts and notifications: Configure the system to generate alerts based on predefined rules and thresholds. These alerts should notify security teams of potential threats, allowing for prompt investigation and response.
- Integrate with existing security infrastructure: Integrate the monitoring system with other security tools, such as SIEM (Security Information and Event Management) systems and incident response platforms. This integration facilitates streamlined alert management, incident investigation, and remediation.
Key Metrics to Monitor for Suspicious Behavior
Monitoring specific metrics is essential for identifying suspicious behavior within containers. These metrics provide insights into various aspects of container activity, allowing for the detection of anomalies and potential security threats. By focusing on these key areas, security teams can proactively identify and respond to malicious activities.Here are some key metrics to monitor:
- System Calls: Monitor for unusual or malicious system calls. For example, calls to `execve` with suspicious arguments, `chmod` to modify permissions, or `ptrace` for debugging could indicate malicious activity.
- Network Traffic: Analyze network connections, including source and destination IPs, ports, and protocols. Look for unexpected outbound connections, connections to known malicious IP addresses, or excessive network traffic volume.
- File Access: Track file access patterns, including file creation, modification, and deletion. Monitor for suspicious file operations, such as attempts to access sensitive files or modify system configuration files.
- Process Execution: Monitor process creation and termination. Look for unexpected processes, processes running with elevated privileges, or processes spawned from suspicious locations.
- Resource Usage: Monitor CPU, memory, and disk I/O usage. Anomalous resource consumption patterns could indicate denial-of-service attacks or other malicious activities.
- User Activity: Monitor user logins, commands executed, and user account modifications. Look for unauthorized access attempts, suspicious commands, or changes to user privileges.
- Container Configuration Changes: Monitor for modifications to container configuration, such as changes to environment variables or container images. This can help detect attempts to compromise container security.
Designing a System for Automatically Detecting and Responding to Runtime Threats
Designing a system for automatic threat detection and response involves establishing a closed-loop process that includes monitoring, analysis, alerting, and remediation. This system should be capable of identifying threats in real-time and triggering automated responses to mitigate the impact of security incidents. This proactive approach significantly reduces the window of opportunity for attackers and improves the overall security posture of the containerized environment.The system should include these components:
- Monitoring and Data Collection: Utilize the monitoring tools to collect relevant data, including system calls, network traffic, file access, and process execution.
- Threat Detection Engine: Implement a threat detection engine that analyzes the collected data in real-time. This engine can utilize rule-based detection, anomaly detection, and machine learning techniques to identify suspicious activities.
- Rule-based detection: This method involves defining rules based on known attack patterns or security best practices. For example, a rule could trigger an alert if a container attempts to execute a specific malicious command or connect to a known malicious IP address.
- Anomaly detection: This method uses statistical techniques and machine learning to identify deviations from normal behavior. The system learns the baseline behavior of containers and flags any significant deviations as potential threats.
- Machine learning: Machine learning models can be trained to identify complex attack patterns and predict future threats. These models can analyze large datasets of security events to identify subtle indicators of compromise.
- Alerting and Notification: Configure the system to generate alerts and notifications when threats are detected. These alerts should be routed to the appropriate security teams and incident response platforms.
- Automated Response: Implement automated response actions to mitigate the impact of identified threats. Examples include:
- Container Isolation: Isolate compromised containers from the network to prevent the spread of the attack.
- Container Termination: Terminate malicious containers to prevent further damage.
- Image Rollback: Roll back to a known good container image to restore the container to a clean state.
- Alerting and Logging: Log all actions taken and provide detailed information for investigation.
- Incident Response and Remediation: Establish an incident response process to investigate and remediate security incidents. This process should include steps for:
- Incident investigation: Analyze the incident to determine the root cause and scope of the attack.
- Containment: Implement containment measures to prevent the attack from spreading.
- Eradication: Remove the threat from the containerized environment.
- Recovery: Restore the containerized environment to a secure state.
- Post-incident analysis: Conduct a post-incident analysis to identify areas for improvement and prevent future incidents.
Network Security in Container Runtimes
Securing network communications is a critical aspect of container runtime security. Containerized applications, by their nature, often involve numerous services interacting with each other and the external world. Without proper network security measures, these interactions can become significant vulnerabilities, allowing malicious actors to exploit weaknesses and compromise the entire container environment. This section focuses on essential network security practices within container runtimes.
Importance of Network Segmentation for Container Security
Network segmentation is a fundamental principle in securing containerized environments. It involves dividing the network into isolated segments, restricting communication between them based on the principle of least privilege. This approach minimizes the attack surface, containing the impact of a security breach. If one container is compromised, the attacker’s access is limited to the segment it resides in, preventing them from easily spreading to other containers or the underlying infrastructure.To effectively implement network segmentation, consider the following:
- Isolate Workloads: Separate different application tiers (e.g., web servers, databases) into distinct network segments. This prevents lateral movement if one tier is breached. For example, a compromised web server should not have direct access to the database segment.
- Micro-segmentation: Within a segment, further restrict communication between individual containers using fine-grained network policies. This ensures only necessary traffic is allowed.
- Firewalling: Implement network firewalls to control traffic flow between segments and external networks. This is a crucial step in preventing unauthorized access.
- Regular Auditing: Regularly audit network policies and firewall rules to ensure they are up-to-date and effective. Review access logs for suspicious activity.
Configuring Network Policies with Calico or Cilium
Tools like Calico and Cilium are designed to simplify the implementation of network policies in Kubernetes, providing robust and flexible solutions for container network security. These tools allow administrators to define rules that govern how containers communicate with each other and the outside world.Here’s a guide to configuring network policies using Calico and Cilium:
Calico:
Calico uses Kubernetes NetworkPolicy resources and its own custom resources (e.g., GlobalNetworkPolicy) to define network rules.
- Installation: Install Calico on your Kubernetes cluster. The installation process typically involves applying a YAML configuration file.
- NetworkPolicy Definition: Create Kubernetes NetworkPolicy resources. These policies specify which pods are allowed to communicate with each other, based on labels.
- Example: To allow a frontend pod with the label “app=frontend” to access a backend pod with the label “app=backend” on port 8080, you might create a NetworkPolicy like this:
apiVersion: networking.k8s.io/v1kind: NetworkPolicymetadata: name: allow-frontend-to-backend namespace: defaultspec: podSelector: matchLabels: app: backend policyTypes: -Ingress ingress: -from: -podSelector: matchLabels: app: frontend ports: -protocol: TCP port: 8080
This policy, placed in the same namespace as the backend pods, allows incoming traffic from frontend pods on port 8080.
Cilium:
Cilium also leverages Kubernetes NetworkPolicy but provides additional features, such as Layer 7 (application-level) filtering and service mesh capabilities. Cilium uses eBPF for high-performance networking and security.
- Installation: Install Cilium on your Kubernetes cluster. This also typically involves applying a YAML configuration file.
- NetworkPolicy Definition: Create Kubernetes NetworkPolicy resources or CiliumNetworkPolicy resources. CiliumNetworkPolicy offers more advanced options, such as L7 policies.
- Example: To allow HTTP traffic from a frontend pod to a backend pod on a specific path using CiliumNetworkPolicy:
apiVersion: cilium.io/v2kind: CiliumNetworkPolicymetadata: name: allow-frontend-to-backend-http namespace: defaultspec: endpointSelectors: -matchLabels: app: backend ingress: -fromEndpoints: -matchLabels: app: frontend toPorts: -ports: -port: "80" protocol: TCP rules: http: -method: GET path: /api/data
This CiliumNetworkPolicy allows HTTP GET requests to the /api/data path on port 80 of the backend pods from the frontend pods.
Key Considerations:
- Namespaces: NetworkPolicies are namespace-scoped by default. This means they only apply to pods within the same namespace.
- Labels: Use labels consistently to identify pods for network policy targeting.
- Policy Types: Define policy types (Ingress, Egress, or both) to control traffic direction.
- Testing: Thoroughly test network policies in a non-production environment before applying them to production.
Best Practices for Securing Container-to-Container Communication
Securing communication between containers is crucial for maintaining the integrity and confidentiality of containerized applications. Implement these best practices to protect container-to-container traffic:
- Use Network Policies: Implement network policies (as described above) to restrict communication between containers to only what is necessary. This prevents unauthorized access and limits the impact of a security breach.
- Encrypt Traffic: Encrypt all sensitive traffic between containers. This protects data in transit from eavesdropping. Consider using TLS/SSL for HTTP communication or other encryption protocols for different types of traffic.
- Service Mesh: Deploy a service mesh (e.g., Istio, Linkerd) to manage and secure container-to-container communication. Service meshes provide features like mutual TLS (mTLS) for encrypted communication, traffic management, and observability.
- Least Privilege: Ensure that containers only have the necessary permissions to communicate with other containers. Avoid granting excessive privileges.
- Authentication and Authorization: Implement authentication and authorization mechanisms to verify the identity of containers before allowing them to communicate. This prevents unauthorized containers from accessing sensitive resources.
- Regular Auditing and Monitoring: Continuously monitor container-to-container communication for suspicious activity. Regularly audit network policies and access logs to identify potential security vulnerabilities.
- Consider Zero Trust Principles: Implement a Zero Trust approach, assuming that no container or user is trusted by default. Verify every access request, regardless of its origin. This can be achieved using tools like service meshes and robust authentication mechanisms.
Host OS Hardening for Container Runtimes
The host operating system (OS) serves as the foundation upon which container runtimes operate. Its security posture directly impacts the security of all containers running on it. A compromised host OS can provide attackers with a pathway to compromise all the containers and data residing within. Therefore, securing the host OS is a critical component of a comprehensive container security strategy.
Critical Host OS Hardening Techniques
Implementing robust host OS hardening techniques is essential to minimize the attack surface and prevent container-related security breaches. This involves several key areas.
- Regular Security Patching: Maintaining an up-to-date host OS is paramount. Timely application of security patches addresses known vulnerabilities that attackers can exploit. This includes patches for the kernel, system libraries, and installed software. Automated patching mechanisms can significantly reduce the time between vulnerability disclosure and remediation. For example, organizations like the National Institute of Standards and Technology (NIST) regularly publish vulnerability databases (like the National Vulnerability Database – NVD) that provide detailed information about known vulnerabilities, enabling security teams to prioritize patching efforts.
- User Account Management: Strict control over user accounts and privileges is crucial. Avoid using default accounts and passwords. Implement the principle of least privilege, granting users only the necessary access rights. Regular review of user accounts and their permissions ensures that access is appropriate and up-to-date. Multi-factor authentication (MFA) should be enforced for all privileged accounts to add an extra layer of security.
- File System Security: Secure file system configurations prevent unauthorized access and modification of system files and container images. This includes proper permissions management, such as setting appropriate ownership and permissions on critical files and directories. Employing file integrity monitoring tools helps detect any unauthorized changes to system files.
- Network Security: Configure the host OS firewall to restrict network traffic to only the necessary ports and protocols. Implement intrusion detection and prevention systems (IDS/IPS) to monitor network activity for suspicious behavior. Consider using network segmentation to isolate the host OS from container networks and other potentially untrusted networks.
- Audit Logging: Enable comprehensive audit logging to track system events and user activities. This includes logging of login attempts, file access, and system configuration changes. Regularly review audit logs to identify suspicious activities and potential security incidents. Tools like `auditd` on Linux systems provide robust auditing capabilities.
- Security Configuration Management: Use security configuration management tools (e.g., CIS benchmarks, security templates) to standardize and automate the configuration of the host OS. These tools ensure consistent security settings across all hosts and simplify the process of applying security best practices.
Benefits of Using a Minimal Host OS for Containers
Employing a minimal host OS, often referred to as a “container-optimized OS” or “distroless OS,” offers significant security advantages. These OSes are designed to reduce the attack surface by including only the essential components needed to run containers.
- Reduced Attack Surface: Minimal OSes have a smaller footprint, which means fewer installed packages and services. This significantly reduces the potential attack surface, as there are fewer vulnerabilities to exploit. For example, a traditional OS might include a web server, database server, and other services, each of which represents a potential entry point for attackers. A minimal OS would exclude these, focusing solely on the container runtime and essential dependencies.
- Faster Boot Times: With fewer components, minimal OSes boot up faster. This can lead to quicker container startup times and improved overall system performance.
- Simplified Management: The streamlined nature of minimal OSes makes them easier to manage and maintain. Updates and security patching are often simpler and less prone to errors.
- Enhanced Security Posture: The reduced complexity of minimal OSes contributes to a more secure environment. It’s easier to identify and mitigate potential vulnerabilities when there are fewer components to consider.
- Improved Resource Efficiency: Minimal OSes consume fewer system resources (CPU, memory, disk space), which can lead to improved resource utilization and cost savings.
Steps to Secure the Host OS Against Container-Related Attacks
Securing the host OS against container-related attacks involves a multi-layered approach, addressing various potential attack vectors.
- Isolate Containers: Implement container isolation mechanisms (e.g., namespaces, cgroups) to prevent containers from interfering with each other or the host OS. Namespaces provide isolation for processes, networks, and other resources, while cgroups limit resource usage.
- Limit Host Access from Containers: Restrict the access containers have to the host OS. Avoid mounting sensitive directories (e.g., `/proc`, `/sys`) into containers unless absolutely necessary. This prevents containers from potentially accessing and manipulating host OS resources.
- Regularly Update the Container Runtime: Keep the container runtime (e.g., Docker, containerd) up-to-date with the latest security patches. These updates often include fixes for vulnerabilities that could be exploited to compromise the host OS.
- Use a Container Security Scanner: Employ container image scanning tools to identify vulnerabilities in container images before they are deployed. This helps prevent the deployment of images with known security flaws.
- Implement Host Intrusion Detection: Install host-based intrusion detection systems (HIDS) to monitor the host OS for suspicious activity that could indicate a container-related attack. HIDS can detect unauthorized access, privilege escalation attempts, and other malicious behaviors.
- Harden the Container Runtime Configuration: Configure the container runtime with security best practices. This includes enabling features like AppArmor or SELinux to further restrict container capabilities and prevent malicious actions.
- Monitor Container Activity: Implement container monitoring tools to track container behavior and identify any unusual or suspicious activity. This can help detect and respond to security incidents in a timely manner.
- Protect the Container Daemon: Secure the container daemon (e.g., `dockerd`) to prevent unauthorized access. This includes restricting access to the daemon socket and using authentication mechanisms.
- Secure Container Network: Utilize a secure container network to prevent unauthorized network traffic. This can be achieved by using network policies, firewalls, and encryption.
Implementing Least Privilege in Containers
Implementing least privilege is a cornerstone of secure containerization. By adhering to this principle, you significantly reduce the attack surface of your containers and limit the potential damage from a security breach. This involves granting containers only the minimum necessary permissions and access to resources required for their specific tasks.
Understanding Least Privilege and Its Importance
The principle of least privilege dictates that a subject (e.g., a user, a process, or a container) should only have the minimum necessary privileges to perform its intended function. Applying this principle to container runtime security is crucial for several reasons.
- Reduced Attack Surface: Limiting the privileges of a container minimizes the potential impact of a successful compromise. If an attacker gains control of a container, they will only have access to the resources and permissions that the container was explicitly granted.
- Improved Containment: Least privilege enhances the effectiveness of container isolation. Even if a container is compromised, the attacker’s ability to move laterally within the system or access sensitive data is severely restricted.
- Enhanced Compliance: Many security standards and regulations (e.g., PCI DSS, HIPAA) mandate the implementation of least privilege. Adhering to this principle helps organizations meet these compliance requirements.
- Simplified Auditing: By clearly defining the permissions and resource access for each container, auditing becomes simpler and more effective. It’s easier to identify and investigate suspicious activity when privileges are well-defined.
Configuring User Namespaces and Capabilities
User namespaces and capabilities are fundamental mechanisms for implementing least privilege within containers. They provide fine-grained control over the permissions and resources available to a container.
- User Namespaces: User namespaces isolate user and group IDs within a container from the host system. This means a user with UID 0 (root) inside a container does not necessarily have root privileges on the host.
- Capabilities: Capabilities are a more granular approach to privilege control than the traditional root/non-root dichotomy. Instead of granting or denying all root privileges, capabilities allow you to grant only specific privileges.
Configuring user namespaces typically involves enabling them when running the container. For example, using Docker:
docker run --userns-remap default <image_name>This command uses the default user namespace remapping, which assigns a non-root user on the host to the root user inside the container.
Capabilities can be controlled using the `–cap-add` and `–cap-drop` flags. For example, to add the `NET_ADMIN` capability (allowing network configuration) and drop all other capabilities:
docker run --cap-add=NET_ADMIN --cap-drop=ALL <image_name>Alternatively, to add only the necessary capabilities, one could do the following:
docker run --cap-drop=ALL --cap-add=CHOWN --cap-add=DAC_OVERRIDE --cap-add=FOWNER --cap-add=SETGID --cap-add=SETUID <image_name>This configuration drops all capabilities and then adds only those required for the container’s functionality. This is a significantly more secure approach.
Restricting Container Access to Host Resources
Restricting container access to host resources is essential for preventing malicious activity from affecting the underlying host system. Several techniques can be employed to achieve this.
- Volumes: Use volumes to control which host directories and files a container can access. Avoid mounting the entire host file system.
- Network Isolation: Utilize container networking features (e.g., Docker networks) to isolate containers from the host network.
- Resource Limits: Set resource limits (e.g., CPU, memory) to prevent a compromised container from consuming excessive host resources and potentially causing a denial-of-service condition.
- Security Profiles: Implement security profiles (e.g., AppArmor, SELinux) to enforce additional restrictions on container behavior and resource access.
For example, to mount a specific host directory as a volume:
docker run -v /host/path:/container/path <image_name>This mounts the `/host/path` directory on the host to the `/container/path` directory inside the container.
To limit the CPU usage of a container:
docker run --cpus=0.5 <image_name>This limits the container to use up to 50% of a single CPU core.
Container Auditing and Logging
Container auditing and logging are essential components of a robust container runtime security strategy. They provide a detailed record of activities within containerized environments, enabling security teams to monitor, analyze, and respond to potential threats effectively. By capturing and analyzing these logs, organizations can gain valuable insights into container behavior, detect anomalies, and improve their overall security posture.
Setting Up Container Auditing and Logging
Establishing a comprehensive container auditing and logging system involves several key steps to ensure that all relevant events are captured and readily accessible for analysis. The following points detail the process of setting up container auditing and logging:
- Choose a Logging Solution: Select a logging solution compatible with your container orchestration platform (e.g., Kubernetes, Docker Swarm). Popular choices include the Elastic Stack (Elasticsearch, Logstash, Kibana), Splunk, and cloud-native logging services offered by providers like AWS, Azure, and Google Cloud.
- Configure Container Runtime Logging: Configure the container runtime (e.g., Docker, containerd) to log container activity. This typically involves setting up logging drivers, such as the `json-file` driver (for local storage) or the `syslog` driver (for forwarding logs to a centralized server). Ensure that the logging driver captures standard output (stdout) and standard error (stderr) streams from container processes.
- Implement Log Aggregation: Implement a log aggregation system to collect logs from all containers across the environment. This involves configuring log shippers (e.g., Filebeat, Fluentd, Fluent Bit) to collect logs from container hosts and forward them to a centralized logging server or cloud service. The log shippers should be configured to parse the logs, add metadata (e.g., container ID, image name, pod name), and forward them in a structured format.
- Configure Log Storage: Configure the centralized logging server or cloud service to store the aggregated logs. Consider factors such as storage capacity, retention policies, and indexing strategies. Indexing logs allows for efficient searching and analysis.
- Define Log Retention Policies: Establish clear log retention policies based on compliance requirements, security needs, and storage capacity. Regularly review and adjust retention policies to balance the need for historical data with storage costs.
- Enable Auditing Features (Kubernetes): If using Kubernetes, enable the Kubernetes audit log to capture API server activity. Configure the audit policy to log relevant events, such as user actions, resource modifications, and security-related events. Store audit logs securely and separate from application logs.
- Test and Validate: Thoroughly test the logging setup to ensure that logs are being collected, aggregated, and stored correctly. Verify that log entries contain the necessary information and that the system can handle the expected volume of logs. Simulate security incidents to validate the effectiveness of the logging and alerting mechanisms.
Analyzing Logs to Identify Security Incidents
Analyzing container logs is crucial for identifying security incidents and understanding the behavior of containerized applications. This analysis involves searching, filtering, and correlating log entries to detect suspicious activities and potential threats. Here are the steps for analyzing logs to identify security incidents:
- Define Baseline Behavior: Establish a baseline of normal container behavior by analyzing historical logs. This involves identifying typical patterns of activity, such as resource usage, network connections, and process execution. This baseline will serve as a reference point for detecting deviations and anomalies.
- Search for Anomalies: Use log analysis tools (e.g., Kibana, Splunk, or custom scripts) to search for anomalies in the logs. This involves looking for unusual events, such as unexpected network connections, unauthorized file access, or suspicious process executions.
- Filter and Correlate Logs: Filter logs based on specific criteria, such as container ID, image name, user ID, or time range. Correlate log entries from different sources (e.g., container logs, audit logs, network logs) to gain a comprehensive view of events and identify relationships between activities.
- Identify Indicators of Compromise (IOCs): Look for specific indicators of compromise (IOCs), such as known malicious IP addresses, suspicious file names, or unusual user agents. Regularly update the IOC list to stay ahead of emerging threats.
- Investigate Suspicious Events: Investigate any suspicious events identified during log analysis. Gather additional information, such as the context of the event, the affected container, and the potential impact. This may involve examining container configurations, network traffic, and other relevant data.
- Use Threat Intelligence Feeds: Integrate threat intelligence feeds (e.g., from security vendors or open-source intelligence sources) to identify known threats and malicious activities. Correlate log data with threat intelligence to detect potential attacks.
- Automate Log Analysis: Automate log analysis using scripts, rules, or machine learning algorithms to detect and respond to security incidents more efficiently. Implement automated alerting to notify security teams of suspicious events in real-time.
Creating a System for Alerting on Suspicious Events within Containers
Establishing a robust alerting system is essential for timely detection and response to security incidents within containers. The following points Artikel the process of creating a system for alerting on suspicious events:
- Define Alerting Rules: Define a set of alerting rules based on the identified IOCs, anomalies, and security best practices. These rules should trigger alerts when specific conditions are met in the logs.
- Choose an Alerting System: Select an alerting system that integrates with the chosen logging solution. Popular options include email notifications, Slack integrations, PagerDuty, and custom notification systems.
- Configure Alerting Thresholds: Configure alerting thresholds to avoid generating too many false positives. Fine-tune the thresholds based on the environment and the nature of the events.
- Integrate with Incident Response: Integrate the alerting system with the incident response workflow. Ensure that alerts are routed to the appropriate security teams or personnel for investigation and remediation.
- Implement Real-Time Monitoring: Implement real-time monitoring to detect and respond to security incidents as they occur. Use stream processing tools (e.g., Kafka, Apache Flink) to process logs in real-time and trigger alerts immediately.
- Monitor Container Activity: Set up alerts to monitor container activity. This can include alerts for unauthorized container starts or stops, unexpected process executions, changes to container configurations, and network connections to suspicious IP addresses or domains.
- Monitor System-Level Events: Configure alerts to monitor system-level events, such as unusual resource usage, suspicious file access, or unauthorized changes to the host operating system.
- Test and Refine Alerts: Test the alerting system thoroughly to ensure that alerts are triggered correctly and that the notification mechanisms are working as expected. Regularly review and refine the alerting rules and thresholds to improve accuracy and reduce false positives.
- Implement a Reporting System: Implement a reporting system to track alerts, analyze trends, and measure the effectiveness of the alerting system. Use the reports to identify areas for improvement and adjust the security posture accordingly.
Vulnerability Management in Container Runtimes
Managing vulnerabilities is a critical aspect of maintaining a secure containerized environment. It involves identifying, assessing, and mitigating security flaws within container images and the underlying runtime environment. This proactive approach helps to minimize the attack surface and protect against potential exploitation. Effective vulnerability management is not a one-time task but an ongoing process that requires continuous monitoring, patching, and remediation efforts.
Patching Container Images and Runtimes
Patching container images and runtimes is a fundamental aspect of vulnerability management. It involves applying updates to address known security vulnerabilities. The process can be broken down into several key steps.
- Identifying Vulnerabilities: This is the first step in patching. Tools like container image scanners are used to analyze images for known vulnerabilities. These scanners compare the components within the image against vulnerability databases (e.g., the National Vulnerability Database – NVD). The scan results provide a list of identified vulnerabilities, their severity levels, and affected components.
- Choosing a Patching Strategy: There are several approaches to patching container images:
- Rebuilding Images: This involves rebuilding the container image with updated base images or dependencies that include the necessary patches. This is a common and often preferred method, as it provides a clean and updated image.
- Applying Patches Directly (Less Common): In some cases, it might be possible to apply patches directly to the container image. However, this approach can be complex and may not be recommended because it can lead to image drift (differences between the image and its definition).
- Applying Patches:
- Base Image Updates: For vulnerabilities in the base image (e.g., the operating system), updating the base image to a newer version that includes the security patches is necessary. This typically involves updating the `FROM` instruction in the Dockerfile.
- Dependency Updates: For vulnerabilities in application dependencies (e.g., libraries), updating the dependency versions in the Dockerfile or using package managers (e.g., `apt-get update` for Debian-based systems, `yum update` for Red Hat-based systems) is required.
- Testing: After applying patches, it is crucial to thoroughly test the updated container image. This involves running automated tests, performing manual testing, and verifying that the application functions correctly and is not negatively impacted by the changes.
- Deployment: Once the patched image has been tested and validated, it can be deployed to the container runtime environment. This typically involves updating the container deployment configuration (e.g., Kubernetes deployments) to use the new image tag.
- Runtime Updates: Container runtimes themselves (e.g., Docker, containerd) also require regular patching to address security vulnerabilities. These updates are usually provided by the runtime vendor and should be applied promptly.
Managing and Prioritizing Vulnerabilities
Effective vulnerability management requires a structured approach to manage and prioritize identified vulnerabilities. This ensures that the most critical issues are addressed first.
- Vulnerability Assessment: This involves analyzing the scan results and assessing the potential impact of each vulnerability. Consider factors such as:
- Severity: Vulnerabilities are typically assigned a severity score (e.g., Critical, High, Medium, Low) based on the Common Vulnerability Scoring System (CVSS). Prioritize vulnerabilities with higher CVSS scores.
- Exploitability: Assess how easy it is to exploit the vulnerability. Consider if a public exploit is available or if the vulnerability requires specific conditions to be exploited.
- Impact: Evaluate the potential consequences of a successful exploit, such as data breaches, system compromise, or denial of service.
- Asset Value: Consider the importance of the affected container or application to the business. Prioritize vulnerabilities in critical systems.
- Vulnerability Prioritization: Based on the assessment, vulnerabilities should be prioritized for remediation. A common approach is to use a risk-based prioritization model, where vulnerabilities are ranked based on their severity, exploitability, and impact.
Prioritization Formula: Risk = Severity x Exploitability x Impact
Prioritize vulnerabilities with high-risk scores.
- Remediation Planning: Create a plan for addressing each prioritized vulnerability. This plan should include the following information:
- Remediation Steps: Specify the actions required to fix the vulnerability (e.g., updating the image, applying a patch).
- Timeline: Set a realistic timeline for remediation, taking into account the urgency and complexity of the fix.
- Responsible Parties: Assign ownership of the remediation tasks to specific individuals or teams.
- Tracking and Reporting: Implement a system for tracking the progress of vulnerability remediation efforts. Generate reports to monitor the overall security posture and identify trends.
Automating the Vulnerability Remediation Process
Automating the vulnerability remediation process can significantly improve efficiency and reduce the time it takes to address security vulnerabilities. Automation can be applied to several stages of the process.
- Automated Scanning: Integrate container image scanning into the CI/CD pipeline. This allows for automated scanning of images as they are built or updated. Tools such as Clair, Trivy, and Snyk can be integrated into CI/CD pipelines (e.g., Jenkins, GitLab CI, GitHub Actions) to automatically scan container images for vulnerabilities.
- Automated Image Builds: When vulnerabilities are detected, the CI/CD pipeline can be configured to automatically rebuild the container images with the necessary patches. This can involve updating the base image, updating dependencies, or applying patches.
- Automated Testing: Implement automated testing to validate the patched images before deployment. This can include unit tests, integration tests, and security tests.
- Automated Deployment: Once the patched image has been tested, the CI/CD pipeline can automatically deploy it to the container runtime environment. This can involve updating the container deployment configuration and triggering a rollout. For example, in Kubernetes, the deployment can be updated to use the new image tag.
- Vulnerability Remediation Automation Tools: Some tools offer features for automated remediation. For example, some tools can automatically suggest or apply patches based on vulnerability scan results.
- Example of Automated Workflow:
- Developer commits code changes.
- CI/CD pipeline builds a new container image.
- Container image scanner (e.g., Trivy) scans the image for vulnerabilities.
- If vulnerabilities are found, the CI/CD pipeline automatically:
- Updates the base image or dependencies.
- Rebuilds the container image.
- Runs automated tests.
- Deploys the patched image to the container runtime environment.
- Alerts are sent to relevant teams about the remediation.
Advanced Runtime Security Techniques
In the realm of container security, staying ahead of evolving threats necessitates employing advanced techniques. These methods provide deeper visibility, enhanced control, and more robust protection against sophisticated attacks targeting containerized environments. This section delves into cutting-edge strategies, offering practical insights and actionable recommendations.
Use of eBPF for Container Security
eBPF (extended Berkeley Packet Filter) has emerged as a powerful technology for container security, providing unprecedented visibility and control over container behavior. It allows developers to write and run sandboxed programs within the kernel, enabling real-time monitoring and enforcement of security policies without requiring modifications to the container’s code or the underlying kernel.eBPF offers several advantages for container security:
- Real-time Monitoring: eBPF programs can tap into kernel events, providing real-time insights into container activities such as system calls, network traffic, and file access.
- Fine-grained Control: Security policies can be enforced at the kernel level, allowing for precise control over container behavior.
- Performance Efficiency: eBPF programs run within the kernel, minimizing overhead and performance impact.
- Dynamic Enforcement: Security rules can be dynamically updated and enforced without requiring container restarts.
- Extensibility: eBPF is highly extensible, allowing for the development of custom security solutions.
For instance, a security team can use eBPF to monitor system calls made by a containerized application. If the application attempts to execute a command that violates a security policy (e.g., writing to a protected file location), the eBPF program can immediately block the action, generate an alert, and log the event. This proactive approach helps prevent malicious activities before they can cause harm.
Several security tools, like Falco and Cilium, leverage eBPF to provide runtime security capabilities for containers.
Benefits of Using Runtime Security Tools with Zero-Trust Architectures
Integrating runtime security tools with zero-trust architectures significantly enhances the security posture of containerized environments. Zero-trust assumes no implicit trust, requiring every request to be authenticated and authorized. Runtime security tools play a crucial role in verifying and validating container behavior within this framework.The combination of runtime security tools and zero-trust architectures provides the following benefits:
- Continuous Verification: Runtime security tools continuously monitor container activities, ensuring that they align with predefined policies and the principles of zero-trust.
- Reduced Attack Surface: By enforcing least privilege and detecting anomalous behavior, runtime security tools reduce the attack surface and prevent unauthorized actions.
- Enhanced Visibility: Runtime monitoring provides detailed insights into container activities, enabling security teams to detect and respond to threats quickly.
- Improved Compliance: The combination helps organizations meet compliance requirements by providing evidence of security controls and policy enforcement.
- Automated Response: Runtime security tools can automatically respond to security incidents, such as isolating compromised containers or blocking malicious network traffic.
Consider a scenario where a container is compromised. With a zero-trust architecture and integrated runtime security tools, the following actions might occur:
- The runtime security tool detects unusual network traffic originating from the compromised container.
- The tool automatically isolates the container, preventing it from communicating with other parts of the network.
- An alert is generated, notifying the security team of the incident.
- The security team investigates the incident, analyzing logs and container behavior to determine the root cause.
This automated response, enabled by the integration of runtime security tools with zero-trust principles, helps to contain the damage and minimize the impact of the security breach.
Using Container Sandboxing Technologies
Container sandboxing technologies create isolated environments for containers, limiting their access to host resources and reducing the potential impact of security breaches. These technologies provide an extra layer of protection, preventing compromised containers from affecting the host operating system or other containers.Sandboxing technologies utilize various techniques to isolate containers:
- Resource Limits: Limiting the resources a container can use, such as CPU, memory, and network bandwidth.
- Capability Control: Restricting the capabilities a container has, such as the ability to create new users or mount file systems.
- Seccomp Profiles: Using seccomp (secure computing mode) to filter system calls made by a container, blocking potentially harmful calls.
- Namespaces: Isolating the container’s view of the system, including the network, process IDs, and file systems.
A practical illustration of container sandboxing can be visualized using a diagram that shows a container within a sandboxed environment.
Illustration of a Container Sandbox
The image depicts a layered architecture, representing the components involved in container sandboxing. The layers from the bottom up are:
- Host Operating System: The base layer represents the host operating system, the foundation on which the container runtime environment is built.
- Container Runtime (e.g., Docker, containerd): This layer sits atop the host OS and manages the lifecycle of containers, providing the necessary infrastructure for container execution.
- Container Sandbox: This is the key element. It’s depicted as a protective shell or boundary surrounding the container, and can be implemented with technologies like gVisor, Kata Containers or similar.
- Container: Located inside the sandbox, this represents the application or service that is running. The sandbox isolates the container from the host OS and other containers.
Within the sandbox:
- Resource Limits: Arrows indicate limitations on CPU, memory, and network bandwidth, showing the restricted resources available to the container.
- Capability Control: Icons or symbols indicate that certain capabilities (like mounting file systems or creating users) are restricted within the sandbox.
- Seccomp Profile: A filter symbol depicts a seccomp profile, which is applied to filter system calls, blocking potentially harmful ones.
- Namespaces: Dashed lines indicate namespaces, such as network, PID, and mount namespaces, which isolate the container’s view of the system.
This visual representation demonstrates how container sandboxing creates a secure and isolated environment, limiting the container’s access to host resources and reducing the risk of security breaches.
Compliance and Container Runtime Security

Ensuring the security of containerized environments is not just about implementing technical controls; it’s also about adhering to industry regulations and standards. Compliance provides a framework for consistent security practices, enabling organizations to demonstrate their commitment to protecting sensitive data and systems. This section delves into the critical role of compliance in container runtime security, offering guidance on aligning security measures with established frameworks and generating necessary reports.
Importance of Compliance Standards in Container Security
Compliance standards play a vital role in container security by providing a structured approach to managing and mitigating risks. These standards offer a set of requirements and best practices that organizations can follow to ensure their containerized applications and infrastructure meet specific security objectives.The benefits of incorporating compliance standards are numerous:
- Risk Reduction: Compliance helps identify and address potential vulnerabilities, reducing the likelihood of security breaches and data loss. By adhering to established standards, organizations can proactively mitigate risks associated with container runtime environments.
- Improved Security Posture: Compliance mandates the implementation of specific security controls, such as access controls, monitoring, and vulnerability management, leading to a stronger overall security posture.
- Regulatory Adherence: Many industries are subject to regulatory requirements, such as PCI DSS (for payment card data) or HIPAA (for healthcare information). Compliance helps organizations meet these requirements, avoiding penalties and legal issues.
- Enhanced Trust and Reputation: Demonstrating compliance with industry standards builds trust with customers, partners, and stakeholders, enhancing the organization’s reputation.
- Simplified Audits: Following a compliance framework simplifies the audit process, as auditors can easily assess whether the required controls are in place and functioning effectively.
Guide to Mapping Container Security Practices to Compliance Frameworks
Mapping container security practices to compliance frameworks involves identifying the specific requirements of each framework and aligning them with the implemented security controls within the container environment. This process ensures that the container security strategy effectively addresses the compliance obligations.The following steps Artikel a general approach to mapping container security practices to compliance frameworks:
- Identify Applicable Compliance Frameworks: Determine which compliance frameworks are relevant to the organization’s industry, data types, and regulatory requirements. Common examples include PCI DSS, HIPAA, GDPR, NIST, and ISO 27001.
- Understand Framework Requirements: Thoroughly review the requirements of each selected framework. This includes understanding the specific security controls, policies, and procedures mandated by the framework.
- Assess Container Security Practices: Evaluate the current container security practices, including image scanning, runtime monitoring, network segmentation, access controls, and vulnerability management. Document the implemented controls and their effectiveness.
- Map Practices to Requirements: Map the existing container security practices to the specific requirements of each compliance framework. Identify any gaps where security controls are missing or inadequate.
- Develop Remediation Plans: Create remediation plans to address any identified gaps. This may involve implementing new security controls, modifying existing configurations, or updating policies and procedures.
- Implement and Test Remediation: Implement the planned remediation actions and test their effectiveness. Verify that the implemented controls meet the requirements of the compliance frameworks.
- Document and Maintain Compliance: Document the entire mapping process, including the implemented controls, remediation plans, and testing results. Regularly review and update the container security practices to maintain compliance over time.
For example, consider PCI DSS. A containerized application handling credit card data would need to address requirements such as:
- Requirement 6.3: “Develop and maintain secure systems and applications.” This can be addressed through container image scanning and vulnerability management.
- Requirement 8.3: “Implement multi-factor authentication for all access to cardholder data.” This can be achieved through robust access control policies and multi-factor authentication mechanisms within the container environment.
- Requirement 10.2.3: “Implement audit trails to track all user activity.” This aligns with comprehensive container auditing and logging practices.
Demonstrating How to Generate Compliance Reports for Container Environments
Generating compliance reports is essential for demonstrating adherence to security standards and regulations. These reports provide evidence of the implemented security controls and their effectiveness in protecting containerized environments. The specific steps for generating compliance reports will vary depending on the tools and platforms used. However, the general process involves collecting data, analyzing it, and creating reports that detail the organization’s compliance posture.
- Select Reporting Tools: Choose the appropriate tools for generating compliance reports. Many container security platforms offer built-in reporting capabilities, while other tools can be integrated to collect and analyze data.
- Define Reporting Scope: Determine the scope of the compliance reports, including the specific compliance frameworks and the containerized environments to be covered.
- Collect Data: Collect the necessary data from various sources, such as container image scanners, runtime monitoring tools, and audit logs. This data should include information on vulnerabilities, security events, and configuration settings.
- Analyze Data: Analyze the collected data to assess the organization’s compliance posture. Identify any gaps or areas that require attention.
- Generate Reports: Use the reporting tools to generate compliance reports. The reports should include a summary of the findings, details of the implemented security controls, and any identified issues or non-compliance.
- Review and Validate: Review the generated reports to ensure their accuracy and completeness. Validate the findings and address any discrepancies.
- Distribute and Archive: Distribute the compliance reports to relevant stakeholders, such as security teams, auditors, and management. Archive the reports for future reference and audit purposes.
For example, using a container security platform, the process might involve:
- Configuring the platform: Setting up the platform to collect data from container images, runtime environments, and network traffic.
- Defining compliance policies: Specifying the compliance frameworks and requirements to be assessed.
- Running scans and assessments: Initiating scans and assessments to identify vulnerabilities, misconfigurations, and compliance violations.
- Generating reports: Using the platform’s reporting features to create reports that summarize the findings and demonstrate compliance status.
Final Conclusion
In conclusion, implementing robust runtime security for containers is a multifaceted endeavor that requires a proactive and layered approach. By integrating the strategies and tools Artikeld in this guide, you can significantly reduce your attack surface and protect your containerized applications from evolving threats. Remember that continuous monitoring, adaptation, and a commitment to security best practices are essential for maintaining a secure and compliant container environment.
Embracing these principles will empower you to confidently leverage the benefits of containerization while mitigating the associated risks.
Key Questions Answered
What is the difference between container runtime security and container image security?
Container image security focuses on vulnerabilities within the image itself during the build and deployment phases. Runtime security, on the other hand, protects the container while it’s actively running, monitoring for malicious activities and unauthorized access attempts.
How often should I update my container images?
Regularly update your container images, ideally as part of your CI/CD pipeline. This includes patching base images and dependencies to address identified vulnerabilities. The frequency depends on the criticality of the application and the rate at which vulnerabilities are discovered.
What are some common misconfigurations that can lead to runtime security breaches?
Common misconfigurations include running containers with excessive privileges (e.g., root user), not implementing network segmentation, failing to restrict resource usage, and neglecting to monitor container activity. These oversights can create significant vulnerabilities.
How can I automate my runtime security responses?
Automation is key. Integrate your runtime security tools with orchestration platforms like Kubernetes. Implement automated alerting and response mechanisms to address detected threats. For example, automatically isolate a compromised container or trigger a security incident response process.
What are the performance implications of implementing runtime security?
Runtime security tools can introduce some performance overhead. However, well-designed tools are optimized to minimize their impact. Carefully select tools, monitor their performance, and tune them to your specific environment to balance security with performance needs.