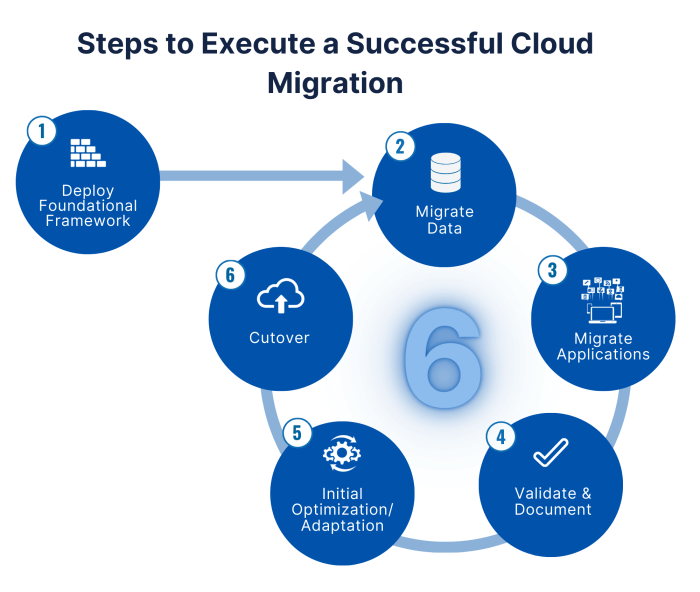
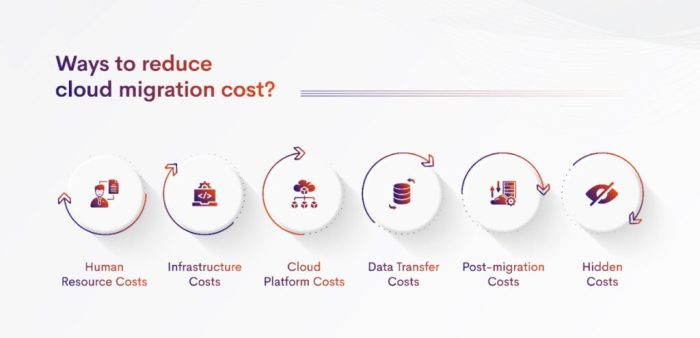
Cloud migration represents a significant shift in IT infrastructure, offering scalability, agility, and cost efficiencies. However, the transition necessitates a robust cloud governance framework to ensure that the benefits are realized while mitigating risks. This framework serves as the bedrock for managing cloud resources effectively, ensuring compliance, optimizing costs, and maintaining security posture post-migration. Failure to establish a well-defined governance structure can lead to uncontrolled spending, security breaches, and regulatory non-compliance, undermining the very advantages cloud migration seeks to achieve.
This comprehensive guide explores the critical steps involved in establishing a cloud governance framework after migration. It covers essential aspects such as risk assessment, policy creation, cost management, access control, data governance, automation, and continuous improvement. Each section delves into practical strategies and best practices, providing a roadmap for organizations to navigate the complexities of cloud governance successfully. The focus is on building a framework that is not only compliant but also adaptable to evolving business needs and technological advancements.
Defining Cloud Governance Post-Migration
Establishing robust cloud governance post-migration is critical to realizing the full benefits of cloud adoption while mitigating risks. This framework ensures that cloud resources are utilized effectively, securely, and in alignment with business objectives. A well-defined governance strategy promotes cost optimization, compliance, and operational efficiency, thereby maximizing the return on investment in cloud infrastructure.
Initial Assessment
The initial assessment is a foundational step in defining cloud governance post-migration. It involves evaluating the current state, identifying key objectives, and understanding the impact of the migration on existing governance practices. This comprehensive evaluation provides a baseline for establishing a governance framework that effectively supports the migrated cloud environment.
- Identifying the Key Business Objectives Driving the Cloud Migration: Cloud migration initiatives are typically driven by specific business goals. Understanding these objectives is paramount for aligning cloud governance with strategic priorities. These goals might include:
- Cost Optimization: Reducing IT infrastructure costs by leveraging the cloud’s pay-as-you-go model and optimizing resource utilization. For instance, a company migrating its on-premises data center to AWS might aim to reduce operational expenses by 20% within the first year, achieved through optimized instance selection and automated scaling.
- Increased Agility and Speed to Market: Accelerating the development and deployment of new applications and services by leveraging the cloud’s scalability and flexibility. An e-commerce company, for example, might migrate to the cloud to enable faster product launches and respond more quickly to market demands, such as increasing server capacity during peak shopping seasons.
- Improved Scalability and Resilience: Enhancing the ability to handle fluctuating workloads and ensuring business continuity through the cloud’s robust infrastructure. Consider a financial institution that migrates its core banking systems to Azure to ensure high availability and disaster recovery capabilities, thus reducing downtime and data loss risks.
- Enhanced Security and Compliance: Strengthening data protection and meeting regulatory requirements by utilizing the cloud provider’s security features and compliance certifications. A healthcare provider, for example, might migrate patient data to Google Cloud to leverage its HIPAA compliance and advanced security services.
- Elaborating on the Current State of Cloud Resources and Their Governance Before Migration: Prior to migration, it’s crucial to assess the existing cloud environment, including its governance policies and practices. This involves:
- Inventory of Cloud Resources: Identifying all existing cloud resources, such as virtual machines, storage accounts, databases, and networking components. This can be achieved through the use of cloud resource management tools, such as AWS Config, Azure Resource Manager, or Google Cloud Resource Manager.
- Review of Existing Governance Policies: Evaluating current governance policies related to security, cost management, compliance, and access control. For example, a company might already have policies in place for password management, data encryption, and access control lists.
- Assessment of Compliance Posture: Determining the organization’s compliance with relevant regulations and standards, such as GDPR, HIPAA, or PCI DSS. This involves reviewing existing audit reports and compliance documentation.
- Identification of Gaps and Weaknesses: Pinpointing areas where governance is lacking or needs improvement. This might include a lack of automated monitoring, insufficient access controls, or inadequate cost management practices.
- Discussing the Impact of the Migration on Existing Governance Policies and Procedures: Cloud migration often necessitates modifications to existing governance policies and procedures. The migration can introduce new technologies, services, and responsibilities, requiring adjustments to ensure continued effectiveness. This may include:
- Updates to Security Policies: Adapting security policies to address cloud-specific threats and vulnerabilities. This involves defining new security controls, such as multi-factor authentication, intrusion detection systems, and data encryption in transit and at rest.
- Changes to Cost Management Procedures: Implementing new cost optimization strategies, such as right-sizing instances, utilizing reserved instances, and leveraging cloud-specific cost management tools.
- Modifications to Access Control Mechanisms: Updating access control policies to manage user permissions and roles in the cloud environment. This involves defining new roles and responsibilities and implementing identity and access management (IAM) solutions.
- Updates to Compliance Procedures: Adjusting compliance procedures to meet the requirements of cloud-specific regulations and standards. This may include updating audit trails, implementing data loss prevention (DLP) policies, and maintaining compliance documentation.
The following table Artikels the key stakeholders and their responsibilities in cloud governance:
| Stakeholder | Responsibilities | Key Activities | Metrics |
|---|---|---|---|
| Cloud Governance Team | Defining and enforcing cloud governance policies and procedures. | Developing and maintaining governance documentation, monitoring compliance, and conducting audits. | Number of policy violations, audit findings, and compliance score. |
| Cloud Architects | Designing and implementing cloud solutions that adhere to governance policies. | Reviewing architectural designs, ensuring compliance with security and cost optimization best practices, and providing technical guidance. | Number of security vulnerabilities, cost optimization savings, and architectural adherence. |
| Security Team | Ensuring the security of cloud resources and data. | Implementing security controls, monitoring security events, and responding to security incidents. | Number of security incidents, vulnerability scan results, and mean time to resolve incidents. |
| Finance Team | Managing cloud costs and ensuring cost optimization. | Monitoring cloud spending, identifying cost-saving opportunities, and forecasting cloud expenses. | Cloud spending vs. budget, cost optimization savings, and cost per unit of output. |
Assessing Risks and Compliance in the Cloud Environment
Post-migration, a robust understanding of the cloud environment’s security posture and adherence to compliance regulations is paramount. This involves proactively identifying potential vulnerabilities, establishing continuous monitoring mechanisms, and implementing stringent data protection measures to mitigate risks and ensure regulatory compliance. The following sections detail these critical aspects.
Common Security Risks in Cloud Environments Post-Migration
Migrating workloads to the cloud introduces new security challenges that must be addressed. These risks stem from the shared responsibility model, where both the cloud provider and the customer share security responsibilities. Understanding these risks is essential for developing effective mitigation strategies.
- Data Breaches: Unauthorized access to sensitive data is a significant concern. This can result from misconfigured storage, weak access controls, or vulnerabilities in applications. For example, a 2023 report by IBM indicated that the average cost of a data breach globally reached $4.45 million, highlighting the financial impact of such incidents.
- Misconfiguration: Incorrectly configured cloud resources, such as storage buckets or virtual machines, can expose data and systems to unauthorized access. A common example is an inadvertently publically accessible Amazon S3 bucket, leading to data exposure.
- Insider Threats: Malicious or negligent actions by employees or contractors with access to cloud resources can lead to data breaches or service disruptions. This emphasizes the importance of robust identity and access management (IAM) policies.
- Account Hijacking: Attackers may attempt to gain control of user accounts through phishing, credential stuffing, or brute-force attacks. Once successful, they can access sensitive data, modify configurations, and launch other attacks. Multi-factor authentication (MFA) is a critical defense against account hijacking.
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks: These attacks aim to disrupt service availability by overwhelming cloud resources with traffic. Cloud providers offer various services to mitigate these attacks, but customers must configure and utilize them effectively.
- Vulnerability Exploitation: Exploiting known vulnerabilities in operating systems, applications, or cloud services can allow attackers to gain unauthorized access or control. Regular patching and vulnerability scanning are essential to address these risks.
- Compliance Violations: Failure to comply with relevant regulations, such as GDPR or HIPAA, can result in significant fines and reputational damage. This underscores the need for a comprehensive compliance strategy.
Compliance Requirements Relevant to Migrated Workloads
Cloud migration necessitates a thorough understanding of applicable compliance regulations. These regulations vary depending on the industry, the location of the data, and the nature of the data itself. Ensuring compliance is not just a legal requirement but also builds trust with customers and stakeholders.
- General Data Protection Regulation (GDPR): GDPR applies to organizations that process the personal data of individuals within the European Economic Area (EEA). Key requirements include obtaining consent for data processing, providing data subject rights (access, rectification, erasure), and implementing appropriate security measures. Failure to comply can result in fines of up to 4% of global annual turnover.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA regulates the protection of protected health information (PHI) in the United States. Covered entities (healthcare providers, health plans, and healthcare clearinghouses) and their business associates must comply with HIPAA’s Privacy Rule, Security Rule, and Breach Notification Rule. Violations can result in significant financial penalties and reputational damage.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS applies to organizations that process, store, or transmit cardholder data. It Artikels security requirements for protecting cardholder data from theft and fraud. Compliance involves implementing technical and operational security controls, such as firewalls, encryption, and access controls.
- California Consumer Privacy Act (CCPA) and California Privacy Rights Act (CPRA): These California laws grant consumers rights regarding their personal information, including the right to access, delete, and opt-out of the sale of their data. Organizations that do business in California and meet certain thresholds must comply with these regulations.
- Other Industry-Specific Regulations: Depending on the industry, organizations may need to comply with other regulations, such as the Sarbanes-Oxley Act (SOX) for financial institutions or the Federal Information Security Management Act (FISMA) for government agencies.
Process for Continuous Monitoring of Security and Compliance Posture
Establishing a robust process for continuous monitoring is crucial to maintain a strong security and compliance posture in the cloud. This involves proactive monitoring, automated alerting, and regular audits to identify and address potential issues promptly.
- Define Key Performance Indicators (KPIs): Establish specific KPIs to measure security and compliance effectiveness. Examples include the number of security incidents, the time to remediate vulnerabilities, and the percentage of compliant configurations.
- Implement Security Information and Event Management (SIEM): Deploy a SIEM solution to collect, analyze, and correlate security logs from various sources, such as cloud services, applications, and network devices. This helps identify security threats and anomalies.
- Automated Vulnerability Scanning: Utilize automated vulnerability scanning tools to regularly scan cloud resources for vulnerabilities. These tools identify known weaknesses in operating systems, applications, and configurations.
- Compliance Auditing: Regularly audit cloud configurations and activities to ensure compliance with relevant regulations and internal policies. This can involve both manual and automated assessments.
- Threat Detection and Response: Implement threat detection mechanisms, such as intrusion detection systems (IDS) and endpoint detection and response (EDR) solutions, to identify and respond to security threats in real-time.
- Incident Response Plan: Develop and regularly test an incident response plan to handle security incidents effectively. This plan should Artikel the steps to be taken in the event of a security breach or other incident.
- Regular Reporting and Analysis: Generate regular reports on security and compliance posture, including KPIs, findings from audits and vulnerability scans, and the status of remediation efforts. Analyze these reports to identify trends and areas for improvement.
Best Practices for Data Loss Prevention
Data loss prevention (DLP) is a critical aspect of cloud security. Implementing these best practices helps to minimize the risk of data breaches and unauthorized data access.
- Data Classification: Classify data based on its sensitivity and business value. This helps to prioritize security efforts and implement appropriate controls for different types of data.
- Data Encryption: Encrypt data at rest and in transit to protect it from unauthorized access. Encryption is a fundamental security control.
- Access Control: Implement strong access controls, including role-based access control (RBAC) and multi-factor authentication (MFA), to restrict access to sensitive data.
- Data Loss Prevention (DLP) Tools: Utilize DLP tools to monitor and control data movement, detect sensitive data, and prevent data leakage.
- Regular Backups: Implement a robust backup and recovery strategy to ensure that data can be recovered in the event of a data loss incident. Backups should be stored securely and tested regularly.
- Data Retention Policies: Establish and enforce data retention policies to minimize the amount of sensitive data stored. This reduces the potential impact of a data breach.
- User Training: Educate employees about data security best practices and the importance of protecting sensitive data. Regular security awareness training is crucial.
- Monitoring and Auditing: Continuously monitor data access and activity, and regularly audit data security controls to identify and address potential vulnerabilities.
Establishing Cloud Governance Policies and Procedures
Effective cloud governance post-migration hinges on well-defined policies and procedures. These ensure consistent application of security, cost management, and operational best practices across the cloud environment. This section details the creation, implementation, and enforcement of these critical elements.
Creating a Template for Cloud Governance Policies
Developing a comprehensive cloud governance policy template is the foundation for a secure, compliant, and cost-effective cloud environment. This template should cover key areas, providing a structured approach to cloud management.
- Access Control: This policy dictates who can access what resources and under what circumstances. It ensures the principle of least privilege is applied, minimizing the attack surface. It should include:
- Role-Based Access Control (RBAC): Defining roles and assigning permissions based on job function.
- Multi-Factor Authentication (MFA): Mandatory for all user accounts to enhance security.
- Regular Access Reviews: Periodic audits to ensure access rights remain appropriate.
- Data Management: This policy governs data storage, handling, and retention. It addresses data security, compliance with regulations, and data lifecycle management. Considerations include:
- Data Encryption: Encryption of data at rest and in transit.
- Data Classification: Categorizing data based on sensitivity to determine appropriate handling.
- Data Retention Policies: Defining how long data is stored and when it should be deleted.
- Cost Optimization: This policy focuses on managing and minimizing cloud spending. It aims to achieve cost efficiency without sacrificing performance or security. It encompasses:
- Resource Utilization Monitoring: Tracking resource usage to identify inefficiencies.
- Right-Sizing Resources: Optimizing resource allocation to match actual needs.
- Reserved Instances/Savings Plans: Leveraging these options to reduce long-term costs.
- Security: Security policies are paramount and encompass a wide range of practices to protect cloud assets. This includes:
- Vulnerability Scanning: Regular scanning to identify and address security vulnerabilities.
- Incident Response: Establishing a plan for responding to security incidents.
- Compliance: Ensuring adherence to relevant regulatory requirements (e.g., HIPAA, GDPR).
Enforcing Cloud Governance Policies Using Automation Tools
Automation is essential for enforcing cloud governance policies consistently and at scale. Various tools can automate policy enforcement, reducing manual effort and human error.
- Infrastructure as Code (IaC): Tools like Terraform or AWS CloudFormation allow defining infrastructure as code, embedding governance policies into infrastructure deployments. This ensures every deployment adheres to predefined standards.
- Policy as Code (PaC): Services like AWS Config or Azure Policy enable defining policies as code. These policies can automatically assess resource configurations and enforce compliance. For example, a PaC policy could check if all S3 buckets are encrypted.
- Automated Remediation: When a policy violation is detected, automated remediation tools can take corrective actions. This might involve automatically shutting down non-compliant resources or reconfiguring them to meet policy requirements.
- Example using AWS Config:
- Policy Definition: Define a rule in AWS Config to check if all S3 buckets have server-side encryption enabled.
- Configuration Changes: When a new S3 bucket is created without encryption, AWS Config detects this configuration change.
- Remediation: An AWS Lambda function, triggered by AWS Config, automatically enables server-side encryption on the non-compliant bucket.
Procedures for Handling Policy Violations and Exceptions
A well-defined process for handling policy violations and exceptions is critical for maintaining governance integrity. This process ensures violations are addressed promptly and exceptions are managed responsibly.
- Detection and Alerting: Implement mechanisms to detect policy violations. This includes monitoring logs, running automated compliance checks, and establishing alerts for violations.
- Investigation and Analysis: When a violation is detected, investigate the cause and assess the impact. This involves analyzing logs, reviewing configurations, and determining the root cause.
- Remediation: Take corrective actions to resolve the violation. This could involve manual intervention, automated remediation, or a combination of both.
- Documentation and Reporting: Document all violations, the actions taken, and the outcomes. Generate reports to track compliance status and identify trends.
- Exception Management: Establish a process for handling exceptions to policies. This should include a formal request process, review and approval workflow, and ongoing monitoring of exceptions.
Demonstrating Cloud Governance Policy Implementation
The following example illustrates how a cost optimization policy could be implemented using AWS CloudFormation and AWS CloudWatch.
Policy: “All EC2 instances must be tagged with a cost center tag.”
Implementation:
- CloudFormation Template: Create a CloudFormation template to deploy EC2 instances. The template includes a `Tags` section requiring a `CostCenter` tag.
- AWS CloudWatch Rule: Create a CloudWatch rule that triggers on EC2 instance creation. The rule uses the `ec2:CreateInstances` event from CloudTrail.
- AWS Lambda Function: The CloudWatch rule triggers an AWS Lambda function.
This Lambda function checks if the created EC2 instance has the `CostCenter` tag.
If the tag is missing, the Lambda function sends a notification to the designated team and/or automatically tags the instance with a default cost center.Outcome: All EC2 instances are created with the `CostCenter` tag, ensuring accurate cost allocation and adherence to the cost optimization policy. The automated process minimizes manual effort and ensures consistent policy enforcement.
Implementing Cost Management and Optimization Strategies
Following a cloud migration, effective cost management and optimization are crucial for realizing the full benefits of cloud computing, such as scalability and agility, while avoiding cost overruns. Proactive monitoring, resource utilization optimization, and the strategic use of cost management tools are essential for controlling cloud spending and maximizing the return on investment (ROI). This section delves into the practical strategies for achieving these goals.
Monitoring and Controlling Cloud Spending
Effective monitoring is the foundation of cloud cost management. It provides real-time visibility into cloud spending patterns, allowing for proactive identification of cost anomalies and opportunities for optimization.
- Setting Up Budget Alerts and Thresholds: Implementing budget alerts allows organizations to proactively manage cloud spending. By defining budget thresholds, users receive notifications when spending approaches or exceeds pre-defined limits. For example, a company might set a budget alert for its development environment at $5,000 per month. When spending reaches $4,500, an alert is triggered, enabling the team to investigate and take corrective action before the budget is exceeded.
This proactive approach prevents unexpected costs.
- Utilizing Cloud Provider’s Cost Management Dashboards: Cloud providers, such as AWS, Azure, and Google Cloud, offer built-in cost management dashboards that provide detailed insights into spending. These dashboards allow users to visualize spending trends, identify cost drivers, and analyze costs by service, region, and resource type. AWS Cost Explorer, Azure Cost Management + Billing, and Google Cloud’s Cloud Billing dashboards provide functionalities to filter, group, and analyze cost data, enabling granular control and analysis.
- Establishing Regular Cost Reporting and Analysis: Regularly reviewing and analyzing cost reports is critical for identifying areas where costs can be reduced. These reports should detail spending by department, project, and resource. For instance, a monthly cost report might reveal that a specific development project is consuming an unexpectedly high amount of compute resources due to inefficient code or over-provisioned instances. This information enables the organization to take corrective actions, such as optimizing code or resizing instances.
- Implementing Tagging and Resource Grouping: Tagging resources with relevant metadata, such as project name, department, or cost center, is essential for accurate cost allocation and reporting. By tagging resources, organizations can easily track and attribute costs to specific projects or teams. Resource grouping allows for logical organization and management of resources, simplifying cost analysis. For example, tagging all EC2 instances used by the marketing department with the “marketing” tag enables accurate cost allocation and reporting for that department.
Strategies for Optimizing Cloud Resource Utilization
Optimizing cloud resource utilization involves ensuring that resources are used efficiently, avoiding waste, and maximizing the value derived from cloud investments.
- Rightsizing Instances: Rightsizing involves matching the size of compute instances to their actual workload requirements. Over-provisioning leads to unnecessary costs, while under-provisioning can impact performance. Regular monitoring of CPU utilization, memory usage, and network I/O is essential for identifying instances that are either over- or under-utilized. For example, if an EC2 instance consistently uses only 20% of its CPU capacity, it can be resized to a smaller, less expensive instance type.
- Automating Instance Scheduling: Automating the start and stop times of instances based on usage patterns can significantly reduce costs. For example, non-production environments can be scheduled to shut down during off-peak hours, such as nights and weekends. Tools like AWS Instance Scheduler and Azure Automation can automate this process, ensuring that resources are only running when needed.
- Leveraging Reserved Instances and Savings Plans: Cloud providers offer reserved instances and savings plans that provide significant discounts compared to on-demand pricing. Reserved instances offer a discount in exchange for a commitment to use a specific instance type for a defined period. Savings plans offer flexibility in instance type and usage, providing discounts based on a commitment to spend a certain amount over a period.
For instance, committing to a 3-year reserved instance for a critical database server can result in cost savings of up to 70% compared to on-demand pricing.
- Implementing Auto-Scaling: Auto-scaling automatically adjusts the number of instances based on demand, ensuring that resources are available when needed and scaling down during periods of low activity. This prevents over-provisioning and reduces costs by optimizing resource utilization. For example, an e-commerce website can use auto-scaling to automatically add instances during peak shopping seasons and scale down during off-peak hours.
- Optimizing Storage Usage: Optimizing storage usage involves selecting the appropriate storage tier for different data types and managing data lifecycle effectively. Data that is accessed frequently should be stored in high-performance storage tiers, while less frequently accessed data can be moved to lower-cost tiers, such as archive storage. For example, cold data, such as archived logs, can be moved to Amazon S3 Glacier for cost-effective storage.
Comparison of Cost Management Tools
Different cost management tools offer varying features and capabilities. The choice of tools depends on the specific needs and requirements of the organization.
| Tool | Cloud Provider | Key Features | Benefits | Limitations |
|---|---|---|---|---|
| AWS Cost Explorer | AWS | Cost visualization, cost allocation, budget alerts, cost optimization recommendations | Detailed cost analysis, proactive cost management, cost optimization recommendations | Limited to AWS resources, can be complex for beginners |
| Azure Cost Management + Billing | Azure | Cost analysis, budget alerts, cost recommendations, resource utilization insights | Comprehensive cost management, budget control, resource optimization | Limited to Azure resources, may require some expertise to use effectively |
| Google Cloud Billing | Google Cloud | Cost reporting, cost analysis, budget alerts, cost optimization recommendations | User-friendly interface, detailed cost insights, cost-saving recommendations | Limited to Google Cloud resources, may lack some advanced features compared to third-party tools |
| CloudHealth by VMware | Multi-cloud | Multi-cloud cost management, cost optimization, governance, security | Centralized cost management across multiple cloud providers, comprehensive reporting, advanced analytics | Can be more expensive than cloud-native tools, may require additional configuration |
| CloudCheckr | Multi-cloud | Cost monitoring, security, compliance, automation | Automated cost optimization, security and compliance checks, proactive alerts | May require additional configuration and setup, can be more complex than cloud-native tools |
Illustration: Cloud Cost Optimization Techniques
The following is a detailed description of an illustration depicting various cloud cost optimization techniques.The illustration presents a visually engaging infographic divided into several sections, each representing a key area of cloud cost optimization. The overall design utilizes a clean and modern aesthetic with a consistent color scheme and clear labeling.* Section 1: Rightsizing Instances. This section depicts a series of compute instances represented by stylized server icons.
Some icons are oversized and labeled as “Over-Provisioned,” with a downward arrow indicating potential cost savings. Other icons are appropriately sized and labeled as “Right-Sized.” The illustration emphasizes the importance of monitoring CPU utilization and memory usage to identify and resize instances to match actual workload demands.
Section 2
Automated Scheduling. This section shows a calendar icon with a clock and instances represented by server icons, illustrating the concept of automating instance start and stop times. The illustration indicates that instances are active only during peak hours (e.g., business hours) and automatically shut down during off-peak hours (e.g., nights and weekends). This highlights the cost savings achieved by shutting down instances when they are not needed.
Section 3
Reserved Instances/Savings Plans. This section shows a visual representation of a discount coupon or a savings certificate. This is next to instance icons, which represents how committing to a specific instance type or spending a certain amount can result in cost savings. The illustration highlights the difference between on-demand pricing and discounted pricing for reserved instances or savings plans.
Section 4
Auto-Scaling. This section depicts a dynamic cluster of server icons, with arrows indicating the scaling up and scaling down of instances based on demand. During periods of high activity, the number of server icons increases, representing the addition of instances. During periods of low activity, the number of server icons decreases, representing the removal of instances. This illustrates how auto-scaling optimizes resource utilization by dynamically adjusting the number of instances based on demand.
Section 5
Storage Optimization. This section shows a tiered storage structure with different data types, such as “Frequently Accessed Data,” “Infrequently Accessed Data,” and “Archived Data,” each stored in different storage tiers with varying costs. The illustration demonstrates how moving data to lower-cost storage tiers based on access frequency can significantly reduce storage costs.
Defining Roles and Responsibilities for Cloud Governance
Establishing clear roles and responsibilities is a critical step in building a robust cloud governance framework post-migration. This structured approach ensures accountability, streamlines decision-making processes, and facilitates effective management of cloud resources. Properly defined roles minimize operational inefficiencies and security vulnerabilities, contributing to a more secure and cost-effective cloud environment.
Identifying Key Roles for Cloud Governance
Effective cloud governance requires the assignment of specific roles, each with distinct responsibilities. These roles work collaboratively to ensure that the cloud environment aligns with organizational goals, adheres to compliance requirements, and maximizes the benefits of cloud adoption. Defining these roles is essential for creating a clear division of labor and enabling efficient cloud management.
- Cloud Governance Lead: This role provides overall strategic direction and oversight for cloud governance. They are responsible for defining the cloud governance framework, establishing policies, and ensuring alignment with business objectives.
- Cloud Architect: The Cloud Architect designs and implements the cloud infrastructure, ensuring it meets technical requirements, security standards, and performance goals. They translate business needs into technical solutions and oversee the deployment and management of cloud resources.
- Cloud Security Officer/Specialist: This role focuses on securing the cloud environment. They are responsible for implementing security policies, managing access controls, monitoring security threats, and ensuring compliance with security regulations.
- Cloud Operations Manager: The Cloud Operations Manager oversees the day-to-day operations of the cloud environment. This includes monitoring performance, managing incidents, and ensuring the availability and reliability of cloud services.
- Cloud Cost Manager: This role is responsible for managing and optimizing cloud spending. They monitor cloud costs, identify areas for optimization, and implement cost-saving strategies.
- Compliance Officer: The Compliance Officer ensures that the cloud environment complies with relevant regulations, industry standards, and internal policies. They are responsible for conducting audits, managing compliance risks, and implementing necessary controls.
Elaborating on the Responsibilities of Each Role
Each role within the cloud governance framework has specific responsibilities that contribute to the overall success of cloud adoption. These responsibilities encompass a wide range of activities, from strategic planning to day-to-day operations. Defining these responsibilities clearly ensures that each role understands their obligations and can contribute effectively to the cloud governance process.
- Cloud Governance Lead: Responsibilities include:
- Developing and maintaining the cloud governance framework.
- Defining and communicating cloud governance policies and standards.
- Overseeing the implementation and enforcement of cloud governance policies.
- Monitoring the effectiveness of the cloud governance framework and making necessary adjustments.
- Ensuring alignment of cloud initiatives with business objectives.
- Cloud Architect: Responsibilities include:
- Designing and implementing cloud infrastructure solutions.
- Ensuring that cloud solutions meet technical requirements and performance goals.
- Implementing security best practices in cloud deployments.
- Managing cloud resources and ensuring their efficient utilization.
- Providing technical guidance and support to other teams.
- Cloud Security Officer/Specialist: Responsibilities include:
- Developing and implementing cloud security policies and procedures.
- Managing access controls and user permissions.
- Monitoring security threats and vulnerabilities.
- Conducting security audits and assessments.
- Ensuring compliance with security regulations and standards.
- Cloud Operations Manager: Responsibilities include:
- Monitoring the performance and availability of cloud services.
- Managing incidents and resolving operational issues.
- Ensuring the reliability and scalability of cloud infrastructure.
- Implementing automation and orchestration tools.
- Managing cloud resource provisioning and deprovisioning.
- Cloud Cost Manager: Responsibilities include:
- Monitoring cloud spending and identifying cost optimization opportunities.
- Implementing cost-saving strategies, such as reserved instances and right-sizing.
- Generating cost reports and providing insights to stakeholders.
- Developing and enforcing cloud cost management policies.
- Managing cloud budgets and forecasts.
- Compliance Officer: Responsibilities include:
- Ensuring that the cloud environment complies with relevant regulations and standards (e.g., GDPR, HIPAA, PCI DSS).
- Conducting compliance audits and assessments.
- Identifying and mitigating compliance risks.
- Developing and implementing compliance policies and procedures.
- Liaising with regulatory bodies and auditors.
Establishing Clear Lines of Communication and Escalation Paths
Effective communication and well-defined escalation paths are essential for the smooth operation of the cloud governance framework. Clear communication channels ensure that information flows efficiently between different roles and teams. Well-defined escalation paths ensure that critical issues are addressed promptly and effectively.
- Communication Channels: Establish clear communication channels for different types of information. For example, use a dedicated communication platform (e.g., Slack, Microsoft Teams) for real-time updates, email for formal communications, and regular meetings for strategic discussions.
- Escalation Paths: Define clear escalation paths for issues that require immediate attention. This should include a hierarchy of contacts, with escalation procedures for different types of incidents (e.g., security breaches, service outages, cost overruns).
- Documentation: Document all communication and escalation procedures to ensure consistency and clarity. This documentation should be readily accessible to all relevant personnel.
- Regular Reviews: Regularly review communication and escalation procedures to ensure they remain effective and relevant. Adjust these procedures as needed to reflect changes in the cloud environment or organizational structure.
Mapping Roles to Responsibilities
The following table provides a concise overview of the key roles and their associated responsibilities within a cloud governance framework. This mapping facilitates a clear understanding of each role’s contributions and promotes effective collaboration across teams.
| Role | Responsibilities | Key Activities |
|---|---|---|
| Cloud Governance Lead | Overall strategic direction and oversight of cloud governance. | Developing and maintaining the cloud governance framework, defining and communicating policies, monitoring effectiveness, and ensuring alignment with business objectives. |
| Cloud Architect | Designing and implementing cloud infrastructure solutions. | Designing and implementing cloud infrastructure, ensuring technical requirements are met, implementing security best practices, managing resources, and providing technical guidance. |
| Cloud Security Officer/Specialist | Securing the cloud environment. | Developing and implementing security policies, managing access controls, monitoring threats, conducting audits, and ensuring compliance with security regulations. |
| Cloud Operations Manager | Overseeing the day-to-day operations of the cloud environment. | Monitoring performance, managing incidents, ensuring availability, implementing automation, and managing resource provisioning. |
| Cloud Cost Manager | Managing and optimizing cloud spending. | Monitoring costs, identifying optimization opportunities, implementing cost-saving strategies, generating reports, and managing budgets. |
| Compliance Officer | Ensuring compliance with regulations and standards. | Ensuring compliance, conducting audits, mitigating risks, developing policies, and liaising with regulatory bodies. |
Implementing Access Control and Identity Management
Establishing robust access control and identity management (IAM) is paramount for securing cloud resources post-migration. Effective IAM practices ensure that only authorized users and services can access specific resources, minimizing the attack surface and protecting sensitive data. This section details the implementation of IAM strategies, focusing on access control mechanisms, user identity management, multi-factor authentication (MFA), and best practices.
Implementing Robust Access Control Mechanisms in the Cloud
Access control mechanisms are the cornerstones of cloud security. They govern who or what (users, groups, or services) can access cloud resources and what actions they are permitted to perform. Implementing these mechanisms requires careful planning and execution.The foundation of access control lies in the principle of least privilege. This means granting users only the minimum level of access necessary to perform their job functions.
Avoid granting broad permissions that could lead to unintended consequences if compromised. Role-Based Access Control (RBAC) is a common and effective approach, assigning permissions based on roles within an organization. Attribute-Based Access Control (ABAC) offers even more granular control, allowing access decisions to be based on various attributes, such as user, resource, environment, and time.For example, consider a cloud environment hosting sensitive customer data.
An administrator might implement RBAC with roles such as “Data Analyst,” “Data Engineer,” and “Security Officer.” A “Data Analyst” might be granted read-only access to specific datasets, while a “Data Engineer” might have read-write access to those datasets for data transformation and loading. A “Security Officer” would have broad access for auditing and security monitoring. ABAC could further refine these permissions, allowing access to data only during business hours or based on the user’s location.Another critical aspect is regularly reviewing and auditing access controls.
Periodically assess user permissions to ensure they remain appropriate and remove unnecessary access. Audit logs should be reviewed regularly to detect any unauthorized access attempts or suspicious activities. Cloud providers offer various tools for access control, such as AWS IAM, Azure Active Directory, and Google Cloud IAM. Leveraging these tools effectively is crucial for establishing and maintaining robust access control.
Managing User Identities and Permissions
Effective management of user identities and permissions is essential for maintaining a secure and compliant cloud environment. This involves the creation, management, and lifecycle of user accounts, as well as the assignment and modification of permissions.The process begins with identity provisioning. This involves creating user accounts and assigning initial permissions. Many organizations use identity providers (IdPs) such as Active Directory or Okta to manage user identities centrally and synchronize them with cloud platforms.
This approach, often referred to as federated identity, allows users to use their existing credentials to access cloud resources, simplifying user management and improving the user experience.Permission management involves defining the access rights for each user or group. This should be based on the principle of least privilege, granting only the necessary permissions. Permissions can be assigned directly to users or, more commonly, through roles.
Roles are collections of permissions that define a specific job function or responsibility. This approach simplifies permission management and reduces the risk of errors.User lifecycle management is also critical. This includes processes for onboarding new users, modifying permissions as needed, and offboarding users when they leave the organization or change roles. Automated processes for user lifecycle management can help ensure that user accounts are created, updated, and removed in a timely and consistent manner.Regular audits of user permissions are also essential.
This involves reviewing user access rights to ensure they remain appropriate and removing unnecessary permissions. Audit logs should be reviewed regularly to detect any unauthorized access attempts or suspicious activities.For instance, a company migrating its on-premises infrastructure to AWS might use AWS IAM Identity Center (successor to AWS SSO) to manage user identities. They would integrate their existing Active Directory with IAM Identity Center, allowing users to use their existing credentials to access AWS resources.
They would then define roles such as “Developer,” “Tester,” and “Administrator” and assign the appropriate permissions to each role. The company would implement an automated process to provision and deprovision user accounts and regularly audit user permissions to ensure compliance with security policies.
Designing a Solution for Multi-Factor Authentication
Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple forms of verification before accessing cloud resources. This mitigates the risk of unauthorized access even if a user’s password is compromised.A robust MFA solution typically involves at least two factors: something the user knows (e.g., password), something the user has (e.g., a mobile device), or something the user is (e.g., biometric data).
Implementing MFA requires careful planning and selection of appropriate authentication methods.Common MFA methods include:* Time-Based One-Time Passwords (TOTP): Users generate a six-digit code from an authenticator app (e.g., Google Authenticator, Microsoft Authenticator) that changes every 30 seconds.
Push Notifications
Users receive a push notification on their mobile device, which they approve or deny to authenticate.
Hardware Security Keys
Physical keys (e.g., YubiKey) that generate cryptographic keys or authenticate via USB or NFC.
Biometrics
Fingerprint, facial recognition, or other biometric data used to verify the user’s identity.Choosing the right MFA method depends on the specific needs of the organization. TOTP is a widely supported and cost-effective option. Push notifications provide a user-friendly experience. Hardware security keys offer a high level of security but may be more expensive and require more user training.Implementation involves several steps:
1. Enable MFA for all users
This should be enforced across all cloud accounts and services.
2. Choose an MFA method
Select the method(s) that best meet the organization’s security and usability requirements.
3. Configure MFA for users
Provide clear instructions and support for users to set up MFA.
4. Monitor MFA usage
Track MFA adoption and usage to ensure compliance.
5. Enforce MFA policies
Implement policies that require MFA for all sensitive resources.For example, a financial institution might implement MFA using TOTP and hardware security keys. Employees would be required to use an authenticator app or a security key to access their cloud accounts. The institution would also monitor MFA usage and enforce policies that require MFA for all sensitive resources, such as customer data.
Best Practices for Identity and Access Management
Implementing effective identity and access management requires adherence to best practices. Following these practices helps to ensure the security, compliance, and operational efficiency of the cloud environment.* Implement the Principle of Least Privilege: Grant users only the minimum level of access necessary to perform their job functions.
Use Role-Based Access Control (RBAC)
Assign permissions based on roles within the organization to simplify management and reduce errors.
Employ Multi-Factor Authentication (MFA)
Enforce MFA for all user accounts and sensitive resources to mitigate the risk of unauthorized access.
Automate User Lifecycle Management
Implement automated processes for onboarding, modifying, and offboarding user accounts.
Use Strong Passwords and Password Policies
Enforce strong password policies and regularly review and update passwords.
Regularly Review and Audit Access Controls
Periodically assess user permissions to ensure they remain appropriate and remove unnecessary access.
Monitor and Analyze Audit Logs
Regularly review audit logs to detect any unauthorized access attempts or suspicious activities.
Use Centralized Identity Management
Leverage identity providers (IdPs) to manage user identities centrally and synchronize them with cloud platforms.
Implement Conditional Access Policies
Use conditional access policies to control access based on factors such as user location, device, and network.
Educate Users on Security Best Practices
Train users on security best practices, including password management, phishing awareness, and data security.
Data Governance and Data Protection Strategies
Data governance and protection are critical components of a robust cloud governance framework, particularly after a migration. Ensuring data integrity, confidentiality, and availability is paramount to maintaining trust, complying with regulations, and supporting business objectives. Effective strategies in these areas are not merely technical implementations but are integral to the overall risk management strategy of the cloud environment.
Principles of Data Governance in a Cloud Environment
Data governance in the cloud is guided by principles that emphasize control, accountability, and compliance. These principles ensure that data assets are managed effectively and in accordance with organizational policies and external regulations.
- Data Ownership and Stewardship: Establishing clear roles and responsibilities for data ownership and stewardship is fundamental. Data owners are accountable for the quality, security, and compliance of specific datasets, while data stewards are responsible for implementing and enforcing data governance policies. This ensures accountability for data throughout its lifecycle.
- Data Quality and Consistency: Implementing processes to maintain data quality and consistency is essential. This includes data validation, cleansing, and standardization to ensure data accuracy and reliability. Data quality metrics should be defined and monitored to identify and address data quality issues proactively.
- Data Security and Privacy: Prioritizing data security and privacy is crucial. This involves implementing robust security controls, such as encryption, access controls, and data loss prevention (DLP) measures, to protect sensitive data from unauthorized access, use, or disclosure. Compliance with relevant data privacy regulations, such as GDPR and CCPA, is also a key aspect.
- Data Access and Control: Defining and enforcing data access controls based on the principle of least privilege is vital. This ensures that users and applications only have access to the data they need to perform their functions. Access controls should be regularly reviewed and updated to reflect changes in roles, responsibilities, and business requirements.
- Data Lifecycle Management: Implementing a data lifecycle management strategy is important for managing data from creation to archival or deletion. This includes defining data retention policies, managing data storage costs, and ensuring compliance with legal and regulatory requirements.
- Metadata Management: Maintaining comprehensive metadata about data assets is crucial for understanding and managing data. Metadata includes information about data definitions, lineage, and usage. Effective metadata management enables data discovery, data quality monitoring, and data governance reporting.
- Compliance and Regulatory Adherence: Ensuring compliance with relevant data privacy and security regulations is a core principle. This includes implementing controls to meet the requirements of regulations such as GDPR, HIPAA, and CCPA. Regular audits and assessments should be conducted to verify compliance.
Strategies for Protecting Sensitive Data Post-Migration
Protecting sensitive data requires a layered approach that incorporates technical controls, policies, and procedures. The following strategies are essential for safeguarding data in the cloud environment.
- Data Encryption: Implementing encryption at rest and in transit is a fundamental security measure. Data at rest should be encrypted using strong encryption algorithms, such as AES-256. Data in transit should be encrypted using secure protocols, such as TLS/SSL. Consider using encryption key management services offered by cloud providers for enhanced security and control.
- Access Control and Identity Management: Implementing robust access control mechanisms is essential to restrict access to sensitive data. This includes using strong authentication methods, such as multi-factor authentication (MFA), and implementing the principle of least privilege. Regularly review and update access controls to reflect changes in roles and responsibilities.
- Data Loss Prevention (DLP): Deploying DLP solutions to monitor and prevent the unauthorized disclosure of sensitive data is important. DLP solutions can identify and block sensitive data from leaving the cloud environment. This includes monitoring data uploads, downloads, and email communications.
- Data Masking and Tokenization: Implementing data masking and tokenization techniques to protect sensitive data in non-production environments is necessary. Data masking replaces sensitive data with fictitious but realistic values, while tokenization replaces sensitive data with non-sensitive tokens. This reduces the risk of data breaches in development and testing environments.
- Security Information and Event Management (SIEM): Utilizing SIEM solutions to collect, analyze, and correlate security events is important. SIEM solutions provide real-time monitoring of security events, enabling the detection and response to security incidents. Configure SIEM to monitor cloud resources and services.
- Vulnerability Management: Regularly scanning cloud resources for vulnerabilities and applying security patches is critical. Vulnerability management programs should include regular vulnerability assessments, penetration testing, and remediation of identified vulnerabilities. Automate patch management processes to ensure timely application of security updates.
- Data Backup and Recovery: Implementing robust data backup and recovery procedures is essential to ensure data availability and business continuity. Regularly back up data to a secure location and test the recovery process to ensure data can be restored in the event of a disaster.
Data Backup and Disaster Recovery Procedures
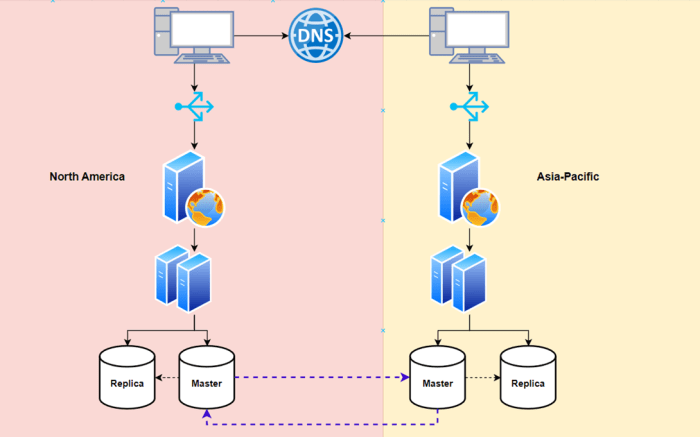
Data backup and disaster recovery (DR) procedures are critical for ensuring business continuity and protecting against data loss. These procedures should be carefully planned, implemented, and regularly tested.
- Backup Strategy: Develop a comprehensive backup strategy that defines the frequency, scope, and retention policies for data backups. Consider using a combination of full, incremental, and differential backups to optimize backup performance and recovery time. Store backups in a geographically diverse location to protect against regional disasters.
- Recovery Point Objective (RPO) and Recovery Time Objective (RTO): Define RPO and RTO to determine the acceptable data loss and downtime in the event of a disaster. RPO defines the maximum amount of data loss that is acceptable, while RTO defines the maximum amount of time that is acceptable for restoring data and services. These objectives should align with business requirements and risk tolerance.
- Disaster Recovery Plan (DRP): Create a detailed DRP that Artikels the steps to be taken in the event of a disaster. The DRP should include procedures for failover, data recovery, and service restoration. Regularly test the DRP to ensure its effectiveness.
- Automated Failover and Failback: Implement automated failover and failback mechanisms to minimize downtime and streamline the recovery process. This can include using cloud-based services that automatically replicate data and applications to a secondary region.
- Regular Testing and Validation: Conduct regular testing of backup and DR procedures to validate their effectiveness. This includes simulating disaster scenarios and testing the recovery process. Document the results of the tests and address any identified issues.
- Data Replication: Implement data replication to ensure data availability and redundancy. Data can be replicated to a secondary region or availability zone to provide a failover site in the event of a disaster.
- Cloud Provider Services: Leverage cloud provider services for backup and DR. Cloud providers offer a range of services, such as object storage, snapshots, and automated replication, to simplify backup and DR processes.
Detailed Description for an Illustration of a Data Governance Workflow
The following describes a data governance workflow, depicted in a diagram illustrating the flow of data from its origin through various stages of processing and protection, to its eventual consumption and archival. This workflow is designed to illustrate how data governance principles are applied in a cloud environment.The diagram is organized as a series of interconnected boxes and arrows.
- Data Source (Origin): This is the starting point of the workflow, representing the origin of the data. Examples of data sources include databases, applications, and external feeds. The box is labeled “Data Source” and contains icons depicting these sources.
- Data Ingestion and Collection: Data from the source is ingested and collected. This involves the process of gathering data from the source and preparing it for processing. The box is labeled “Data Ingestion & Collection” and has an icon of a funnel.
- Data Transformation and Cleansing: This stage involves transforming and cleansing the data to ensure its quality and consistency. This includes data validation, cleansing, and standardization. The box is labeled “Data Transformation & Cleansing” and contains icons representing data transformation tools and processes.
- Data Storage (Secure Cloud Storage): Transformed and cleansed data is stored in a secure cloud storage environment. This environment is protected by access controls, encryption, and other security measures. The box is labeled “Data Storage (Secure Cloud Storage)” and includes an icon of a secure cloud icon.
- Data Access and Governance Policies: This box highlights the application of data governance policies and access controls. These policies govern who can access the data and how it can be used. The box is labeled “Data Access & Governance Policies” and includes icons representing data governance frameworks and access control lists.
- Data Processing and Analytics: Data is processed and analyzed to generate insights. This includes running queries, performing analytics, and generating reports. The box is labeled “Data Processing & Analytics” and includes icons representing analytics tools and dashboards.
- Data Consumption and Reporting: Processed data is consumed by users and applications. This includes generating reports, creating dashboards, and supporting business decisions. The box is labeled “Data Consumption & Reporting” and includes icons representing user interfaces and reporting tools.
- Data Archival and Retention: Data is archived and retained according to data retention policies. This ensures that data is available for compliance and historical analysis. The box is labeled “Data Archival & Retention” and contains an icon representing archival storage.
- Monitoring and Auditing: Throughout the workflow, monitoring and auditing processes are in place to track data access, usage, and compliance. The box is labeled “Monitoring & Auditing” and includes icons representing monitoring tools and audit logs.
- Feedback Loop: Arrows and connectors illustrate the flow of data and feedback loops between the different stages. For example, feedback from monitoring and auditing can inform improvements in data transformation and cleansing processes.
This workflow is an illustrative model, and the specific steps and processes may vary depending on the organization’s needs and the cloud environment. The key is to establish a comprehensive data governance framework that addresses all stages of the data lifecycle.
Automation and Orchestration for Cloud Governance
Automating and orchestrating cloud governance tasks is crucial for maintaining control, ensuring compliance, and optimizing resource utilization in a post-migration cloud environment. This approach streamlines operations, reduces human error, and enables consistent policy enforcement across the entire cloud infrastructure. By leveraging automation, organizations can respond quickly to incidents, proactively manage costs, and maintain a secure and compliant cloud environment.
Automating Cloud Governance Tasks
Automating cloud governance involves leveraging tools and processes to streamline repetitive tasks, enforce policies, and ensure consistent operations. This reduces manual effort and allows for greater efficiency and scalability.Key areas for automation include:
- Policy Enforcement: Automate the application of governance policies to newly provisioned resources. For example, ensure all new virtual machines are configured with specific security settings and tagging conventions.
- Configuration Management: Automate the configuration and maintenance of cloud resources, such as network settings, storage configurations, and access controls.
- Compliance Monitoring: Automate the monitoring of cloud resources for compliance with internal policies and regulatory requirements. Generate alerts and reports when non-compliant configurations are detected.
- Cost Optimization: Automate the identification and remediation of cost inefficiencies, such as identifying idle resources or right-sizing virtual machines.
- Incident Response: Automate the initial steps of incident response, such as triggering alerts, collecting relevant data, and initiating remediation actions.
Using Infrastructure-as-Code (IaC) for Policy Enforcement
Infrastructure-as-Code (IaC) is a practice where infrastructure is managed and provisioned using code, rather than through manual processes. This allows for consistent and repeatable infrastructure deployments and facilitates the enforcement of governance policies.IaC tools enable:
- Policy Definition: Define governance policies as code, specifying desired configurations, security settings, and compliance requirements. This code is version-controlled and can be easily reviewed and audited.
- Automated Provisioning: Use IaC tools to automatically provision infrastructure resources, ensuring that they are configured according to defined policies. For example, a policy might specify that all new virtual machines must be encrypted at rest.
- Configuration Drift Detection: Regularly scan infrastructure configurations to detect any deviations from the defined IaC code. This helps to identify and remediate configuration drift, ensuring that resources remain compliant.
- Continuous Compliance: Integrate IaC with continuous integration and continuous delivery (CI/CD) pipelines to automatically enforce policies during infrastructure deployments.
For instance, using Terraform, a configuration file could define a policy that all S3 buckets must have encryption enabled. The IaC tool would then automatically provision new buckets with encryption enabled, and continuously monitor existing buckets to ensure compliance.
Designing an Automated Workflow for Incident Response
An automated incident response workflow can significantly reduce the time to resolution and minimize the impact of security incidents. The workflow should be designed to automatically detect incidents, collect relevant information, and initiate remediation actions.A typical automated incident response workflow includes the following steps:
- Detection: Implement monitoring and alerting systems to detect potential security incidents. This includes monitoring logs, network traffic, and resource configurations for suspicious activity.
- Alerting: When an incident is detected, trigger an alert to notify relevant stakeholders. The alert should include information about the incident, such as the affected resource, the type of incident, and the severity.
- Triage: Automatically collect relevant data about the incident, such as logs, network traffic captures, and resource configurations. This information is used to understand the scope and impact of the incident.
- Containment: Initiate containment actions to limit the impact of the incident. This may include isolating affected resources, blocking malicious traffic, or disabling compromised accounts.
- Remediation: Implement remediation actions to resolve the incident. This may include patching vulnerabilities, restoring compromised data, or removing malicious software.
- Recovery: Restore affected systems and data to a normal operating state.
- Post-Incident Analysis: Conduct a post-incident analysis to identify the root cause of the incident and implement measures to prevent similar incidents in the future.
For example, a workflow might automatically detect a suspicious login attempt to a critical server. The workflow would then:
- Trigger an alert.
- Collect relevant logs and network traffic data.
- Isolate the affected server from the network.
- Notify the security team for further investigation.
Automation Tools and Their Capabilities
Several automation tools are available to assist in cloud governance. Each tool offers different capabilities and caters to different needs.Here are some prominent automation tools and their capabilities:
- Terraform: An infrastructure-as-code tool for building, changing, and versioning infrastructure. It supports multiple cloud providers and allows for the automated provisioning and management of resources.
- AWS CloudFormation / Azure Resource Manager / Google Cloud Deployment Manager: Native infrastructure-as-code tools for AWS, Azure, and Google Cloud, respectively. They enable the automated provisioning and management of resources within their respective cloud environments.
- Ansible: An automation engine for configuration management, application deployment, and orchestration. It uses simple playbooks to automate tasks across a variety of systems.
- Chef / Puppet: Configuration management tools that automate the configuration and maintenance of servers and applications. They ensure that systems are consistently configured and compliant with defined policies.
- Jenkins / GitLab CI / Azure DevOps: Continuous integration and continuous delivery (CI/CD) tools that automate the build, test, and deployment of applications. They can be integrated with IaC tools to automate the provisioning of infrastructure.
- Security Information and Event Management (SIEM) Systems (e.g., Splunk, Sumo Logic): These systems collect and analyze security logs and events to detect and respond to security incidents. They can be integrated with automation tools to trigger automated incident response actions.
- ServiceNow / Jira Service Management: Service management platforms that can be used to automate IT service management processes, including incident management, change management, and request fulfillment.
Monitoring and Reporting on Cloud Governance Effectiveness
Monitoring and reporting are crucial components of a robust cloud governance framework, providing insights into the framework’s effectiveness and enabling data-driven decision-making. Continuous monitoring ensures that policies and procedures are adhered to, risks are mitigated, and resources are optimized. Effective reporting facilitates communication and transparency, allowing stakeholders to understand the cloud environment’s status and identify areas for improvement.
Monitoring the Effectiveness of the Cloud Governance Framework
The effectiveness of a cloud governance framework is monitored through a multi-faceted approach, integrating automated tools, regular audits, and stakeholder feedback. This process involves continuous assessment and adjustment to ensure alignment with organizational goals and evolving cloud environments.
- Automated Monitoring Tools: Implement automated tools to track key metrics, such as resource utilization, security posture, and compliance with policies. These tools collect data in real-time, providing timely insights into potential issues. For example, tools can automatically flag instances that violate security policies or exceed budget allocations.
- Regular Audits: Conduct periodic audits, both internal and external, to assess compliance with established policies and industry regulations. These audits provide an independent evaluation of the framework’s effectiveness and identify areas for improvement. For example, a security audit may reveal vulnerabilities that need to be addressed.
- Stakeholder Feedback: Establish channels for gathering feedback from stakeholders, including cloud users, IT staff, and management. This feedback provides valuable insights into the framework’s usability, effectiveness, and areas for improvement. Surveys, focus groups, and regular meetings are effective methods for collecting feedback.
- Incident Management and Analysis: Establish a robust incident management process to identify, investigate, and resolve any cloud-related incidents, such as security breaches or service disruptions. Analyze the root causes of incidents to identify areas where the governance framework needs improvement. For example, if a security breach occurs, analyze the contributing factors and update security policies and procedures.
- Continuous Improvement Cycles: Embrace a continuous improvement approach, where monitoring data and stakeholder feedback are used to refine the cloud governance framework. This iterative process ensures that the framework remains relevant and effective over time. This might involve regularly updating policies, adjusting resource allocation, or enhancing security measures based on the latest threat landscape.
Key Performance Indicators (KPIs) to Track
Key Performance Indicators (KPIs) are critical metrics that measure the effectiveness of a cloud governance framework. Tracking these KPIs provides a quantifiable way to assess performance, identify trends, and make informed decisions. These metrics should align with the organization’s strategic objectives and be regularly reviewed and adjusted.
- Cost Optimization: Monitor cloud spending against budget, identify areas of waste, and track the effectiveness of cost-saving initiatives.
- Security Posture: Assess the security of cloud resources, including vulnerabilities, compliance with security policies, and the effectiveness of security controls.
- Compliance: Ensure adherence to regulatory requirements and internal policies, including data protection, privacy, and industry-specific standards.
- Resource Utilization: Monitor the utilization of cloud resources, such as compute instances, storage, and network bandwidth, to optimize resource allocation and reduce costs.
- Service Level Agreement (SLA) Adherence: Track the availability and performance of cloud services to ensure that SLAs are met and that users receive the expected level of service.
- Incident Response Time: Measure the time it takes to detect, respond to, and resolve cloud-related incidents, such as security breaches or service disruptions.
- User Adoption and Satisfaction: Assess user satisfaction with cloud services and track the adoption rate of cloud technologies.
Designing a Reporting Dashboard to Visualize Cloud Governance Metrics
A well-designed reporting dashboard is essential for visualizing cloud governance metrics and providing stakeholders with a clear understanding of the cloud environment’s status. The dashboard should be user-friendly, customizable, and provide real-time or near real-time data.
- Data Sources: The dashboard should integrate data from various sources, including cloud provider APIs, security tools, cost management platforms, and monitoring systems.
- Visualization Tools: Use appropriate visualization tools, such as charts, graphs, and tables, to present data in an easily understandable format.
- Key Metrics: Display key performance indicators (KPIs) that are relevant to the organization’s goals and objectives.
- Customization: Allow users to customize the dashboard to view the data that is most important to them.
- Alerting and Notifications: Implement alerts and notifications to notify stakeholders of any critical issues or trends.
- Regular Updates: Ensure that the dashboard is regularly updated with the latest data and that the underlying data sources are accurate.
- Accessibility: Make the dashboard accessible to all relevant stakeholders, including IT staff, management, and cloud users.
KPIs and Measurement Methods
The following table Artikels key performance indicators (KPIs) and their measurement methods:
| KPI | Description | Measurement Method | Target |
|---|---|---|---|
| Cloud Spend vs. Budget | The difference between actual cloud spending and the allocated budget. | Utilize cloud provider cost management tools (e.g., AWS Cost Explorer, Azure Cost Management, Google Cloud Cost Management) and budget alerts. | Stay within 5% of the allocated budget. |
| Security Vulnerability Remediation Time | The time it takes to remediate identified security vulnerabilities. | Use vulnerability scanning tools (e.g., Nessus, OpenVAS) and track remediation progress in a ticketing system. | Remediate critical vulnerabilities within 24 hours and high vulnerabilities within 72 hours. |
| Compliance Policy Adherence | The percentage of cloud resources that comply with established security and regulatory policies. | Use compliance monitoring tools (e.g., AWS Config, Azure Policy, Google Cloud Policy) and audit reports. | Maintain 95% compliance with all relevant policies. |
| Resource Utilization Rate | The percentage of allocated resources (e.g., CPU, memory, storage) that are actively used. | Use cloud provider monitoring tools (e.g., AWS CloudWatch, Azure Monitor, Google Cloud Monitoring) and resource utilization reports. | Maintain CPU utilization above 60% and storage utilization above 70%. |
Training and Awareness for Cloud Governance
Successful cloud governance post-migration hinges not only on technical implementation but also on fostering a culture of understanding and adherence to established policies. Training and awareness programs are crucial for equipping personnel with the necessary knowledge and skills to navigate the cloud environment securely, efficiently, and in compliance with organizational and regulatory requirements. These programs aim to ensure that all stakeholders, from technical staff to business users, understand their roles and responsibilities within the cloud governance framework.
Importance of Training and Awareness Programs
Training and awareness programs are essential for several reasons. They bridge the knowledge gap, reduce the risk of human error, and promote consistent application of cloud governance policies. Properly trained individuals are better equipped to identify and mitigate potential risks, leading to improved security posture and reduced operational costs. They also facilitate better collaboration and communication across teams, streamlining cloud operations and decision-making processes.
By investing in these programs, organizations can enhance their cloud maturity and achieve their strategic business objectives more effectively.
Examples of Training Materials and Resources
A comprehensive training program should leverage a variety of materials and resources to cater to different learning styles and roles. These include:
- Online Courses and Modules: Interactive online courses covering various cloud governance topics, such as security best practices, cost optimization techniques, and compliance requirements. These modules often include quizzes and assessments to reinforce learning. For instance, platforms like Coursera, edX, and AWS Training offer a range of cloud governance-related courses.
- Instructor-Led Training: In-person or virtual training sessions delivered by cloud governance experts. These sessions provide opportunities for Q&A and practical exercises, allowing for a deeper understanding of complex concepts.
- Workshops and Hands-on Labs: Practical workshops where participants can apply their knowledge to real-world scenarios. These labs often involve configuring cloud services, implementing governance policies, and troubleshooting common issues. For example, organizations might conduct workshops on implementing Identity and Access Management (IAM) policies or setting up cost allocation tags.
- Documentation and Guides: Comprehensive documentation, including policy documents, standard operating procedures (SOPs), and user guides, to provide clear instructions and reference materials. These resources should be easily accessible and regularly updated to reflect changes in the cloud environment.
- Simulations and Gamification: Interactive simulations and gamified learning experiences to make training more engaging and memorable. These can involve scenarios where participants must make decisions about cloud resource allocation, security configurations, or incident response.
- Regular Webinars and Lunch-and-Learns: Short, focused training sessions on specific topics, such as new cloud services, policy updates, or security vulnerabilities. These sessions can be recorded and made available for on-demand viewing.
Promoting a Culture of Cloud Governance
Fostering a culture of cloud governance requires a multi-faceted approach. This includes leadership commitment, clear communication, and ongoing reinforcement of policies and procedures. Senior management should actively champion cloud governance initiatives, setting the tone for the organization. Regular communication, through newsletters, internal blogs, and town hall meetings, is crucial for keeping employees informed about policy changes and best practices. Celebrating successes and recognizing individuals who demonstrate exemplary adherence to cloud governance principles can further reinforce the desired behaviors.
Additionally, incorporating cloud governance considerations into performance evaluations can incentivize employees to prioritize these practices.
Topics to Include in a Cloud Governance Training Program
A comprehensive cloud governance training program should cover a wide range of topics relevant to different roles and responsibilities within the organization. These include:
- Cloud Governance Principles and Framework: An overview of cloud governance concepts, including the importance of governance, common frameworks (e.g., NIST, ISO 27001), and the organization’s specific governance model.
- Cloud Security Fundamentals: Best practices for securing cloud environments, including identity and access management (IAM), data encryption, network security, and vulnerability management.
- Cloud Cost Management and Optimization: Strategies for managing and optimizing cloud costs, including resource allocation, right-sizing, and cost monitoring tools.
- Compliance and Regulatory Requirements: An understanding of relevant compliance regulations (e.g., GDPR, HIPAA, PCI DSS) and how to ensure cloud environments meet these requirements.
- Identity and Access Management (IAM): Training on IAM concepts, including user provisioning, role-based access control (RBAC), multi-factor authentication (MFA), and privileged access management (PAM).
- Data Governance and Data Protection: Best practices for data governance, including data classification, data loss prevention (DLP), and data retention policies.
- Incident Response and Disaster Recovery: Procedures for responding to security incidents and recovering from disasters, including incident reporting, containment, and remediation.
- Cloud Automation and Orchestration: Introduction to automation tools and techniques for streamlining cloud operations and enforcing governance policies.
- Monitoring and Reporting: Training on monitoring tools and techniques for tracking cloud resource usage, security events, and compliance metrics.
- Role-Specific Training: Tailored training modules for different roles, such as cloud architects, developers, security analysts, and business users, to address their specific responsibilities within the cloud governance framework.
Continuous Improvement and Iteration of the Framework
Continuous improvement is paramount in maintaining an effective cloud governance framework. The cloud environment is dynamic, with evolving technologies, changing business needs, and emerging security threats. A static framework quickly becomes obsolete, leaving the organization vulnerable and inefficient. This section Artikels the mechanisms for ensuring the framework remains relevant, effective, and adaptable to the evolving cloud landscape.
Reviewing and Updating Policies and Procedures
Regular reviews and updates of cloud governance policies and procedures are essential to address changes in technology, regulatory requirements, and organizational strategy. This process should be systematic and driven by data and stakeholder feedback.
- Establish a Review Schedule: Define a regular cadence for reviewing policies and procedures, such as quarterly, semi-annually, or annually. The frequency should be determined by the criticality of the policies, the rate of change in the cloud environment, and any regulatory mandates.
- Document the Review Process: Create a documented process for reviewing policies and procedures. This process should Artikel the steps involved, the roles and responsibilities, and the tools and templates to be used.
- Gather Input from Stakeholders: Collect feedback from all relevant stakeholders, including IT, security, finance, legal, and business units. This feedback should include suggestions for improvement, identification of gaps, and assessment of the effectiveness of existing policies.
- Analyze and Assess: Analyze the feedback and assess the impact of any proposed changes. Evaluate the potential benefits, risks, and costs associated with each change.
- Update Policies and Procedures: Based on the analysis and assessment, update the policies and procedures as needed. Ensure that all changes are clearly documented and communicated to all stakeholders.
- Implement and Monitor: Implement the updated policies and procedures and monitor their effectiveness. Track key metrics to measure compliance, identify areas for further improvement, and ensure the framework is achieving its objectives.
- Version Control: Maintain version control of all policies and procedures. This allows for tracking changes, reverting to previous versions if necessary, and ensuring that everyone is using the most up-to-date information.
Incorporating Feedback from Stakeholders
Stakeholder feedback is a critical input for continuous improvement. Gathering and acting upon this feedback ensures that the cloud governance framework meets the needs of the organization and is readily adopted.
- Establish Feedback Mechanisms: Implement multiple channels for stakeholders to provide feedback. These can include surveys, regular meetings, dedicated feedback forms, and a central point of contact for cloud governance inquiries.
- Encourage Active Participation: Actively encourage stakeholders to provide feedback. This can be achieved through clear communication about the importance of feedback, recognition of those who contribute, and showcasing how feedback has led to improvements.
- Analyze Feedback Systematically: Establish a process for systematically analyzing feedback. This involves categorizing feedback, identifying common themes, and prioritizing issues based on their impact and urgency.
- Document Feedback and Actions: Document all feedback received, along with the actions taken in response. This provides transparency and accountability and demonstrates that feedback is valued and acted upon.
- Communicate Results and Changes: Communicate the results of the feedback analysis and any changes made to the framework as a result. This keeps stakeholders informed and reinforces the value of their contributions.
- Iterate on Feedback Mechanisms: Continuously evaluate and improve the feedback mechanisms themselves. This may involve adjusting survey questions, refining communication strategies, or implementing new tools to gather and analyze feedback more effectively.
Illustration of the Continuous Improvement Cycle
The continuous improvement cycle is a cyclical process that involves planning, doing, checking, and acting. This iterative approach ensures that the cloud governance framework is constantly refined and optimized.
The illustration depicts a circular flow, representing the continuous nature of the improvement cycle. At the center of the circle is a diagram representing the “Cloud Governance Framework.” Around this central element, the cycle unfolds in four key stages:
- Plan: This stage is represented by a section labeled “Plan,” containing icons symbolizing activities such as “Policy Development,” “Risk Assessment,” and “Objective Setting.” Arrows lead from this section to the “Do” section.
- Do: This stage is labeled “Do” and includes icons related to “Implementation,” “Training,” and “Monitoring.” This section signifies the execution of the plans made in the “Plan” stage. Arrows lead from this section to the “Check” section.
- Check: This stage is labeled “Check,” with icons depicting “Performance Measurement,” “Feedback Analysis,” and “Compliance Audits.” This section focuses on evaluating the outcomes of the “Do” stage. Arrows lead from this section to the “Act” section.
- Act: This stage is labeled “Act,” with icons showing “Policy Updates,” “Process Adjustments,” and “Training Refinement.” This section is where improvements are made based on the “Check” stage’s findings. Arrows lead back to the “Plan” section, completing the cycle.
Each stage has a clear connection to the others, with arrows indicating the flow of information and actions. The overall impression is one of constant iteration and refinement, demonstrating the ongoing commitment to improving the cloud governance framework. The diagram emphasizes that the framework is not a one-time effort but a continuous process of planning, doing, checking, and acting to ensure effectiveness and alignment with organizational goals.
Final Summary
In conclusion, establishing a cloud governance framework post-migration is a continuous journey of planning, implementation, and refinement. By proactively addressing risks, implementing robust policies, and embracing automation, organizations can unlock the full potential of the cloud while maintaining control and ensuring compliance. The ongoing commitment to monitoring, reporting, and continuous improvement is paramount to adapt to evolving cloud landscapes and business objectives.
Ultimately, a well-defined cloud governance framework empowers organizations to leverage the cloud strategically, driving innovation and achieving sustainable success in the digital era.
Key Questions Answered
What is the primary goal of a cloud governance framework post-migration?
The primary goal is to ensure the secure, compliant, and cost-effective use of cloud resources while aligning with business objectives and maintaining operational efficiency.
How often should cloud governance policies be reviewed and updated?
Cloud governance policies should be reviewed and updated at least annually, or more frequently if there are significant changes in business requirements, technology, or regulatory landscape.
What are the key differences between cloud governance and traditional IT governance?
Cloud governance focuses on the dynamic and elastic nature of cloud resources, emphasizing automation, self-service, and the ability to scale rapidly. Traditional IT governance typically focuses on on-premise infrastructure and often involves more manual processes.
How can automation contribute to effective cloud governance?
Automation streamlines policy enforcement, reduces human error, enables rapid incident response, and enhances overall efficiency by automating repetitive tasks such as provisioning, configuration, and compliance checks.
What are the essential components of a cloud governance reporting dashboard?
An effective reporting dashboard should include key performance indicators (KPIs) related to cost, security, compliance, and performance, providing a comprehensive view of the cloud environment’s health and effectiveness.