Understanding Disposability in 12-Factor Applications
This article dives into the crucial concept of disposability within the framework of 12-factor applications, highlighting its importance in modern clo...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article dives into the crucial concept of disposability within the framework of 12-factor applications, highlighting its importance in modern clo...

This article explores the dangers of premature optimization, a prevalent anti-pattern that can hinder software development progress. It outlines the c...

This comprehensive guide delves into the critical world of log analysis, outlining its fundamental principles, diverse applications, and vital role in...

Creating a compelling business case is essential for successful cloud migration projects. This strategic shift requires articulating the value proposi...
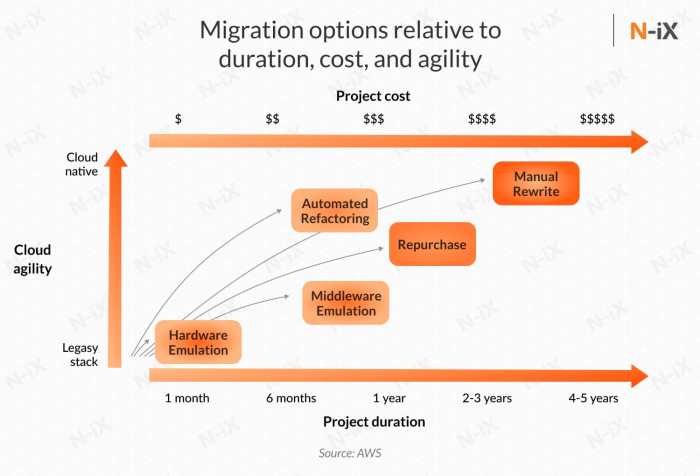
Cloud migration offers substantial benefits, but migrating all applications at once is rarely feasible. This necessitates a strategic approach to prio...

APIs are fundamentally reshaping modern architecture by enabling seamless communication and data exchange between different software applications. Thi...
This comprehensive guide delves into the world of serverless computing, equipping you with the knowledge to ace your next interview. From the fundamen...
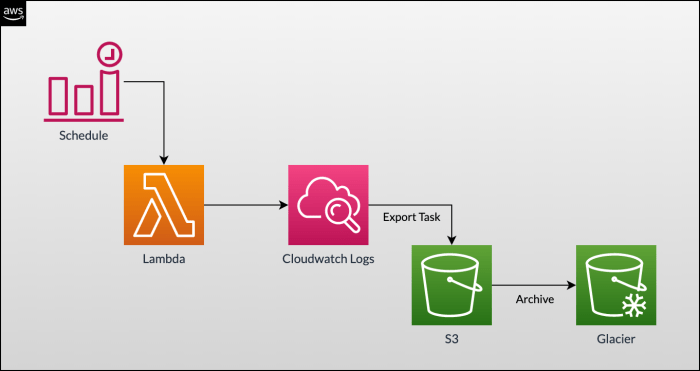
Effectively monitoring and troubleshooting your serverless applications hinges on understanding CloudWatch Logs for Lambda functions. This central rep...
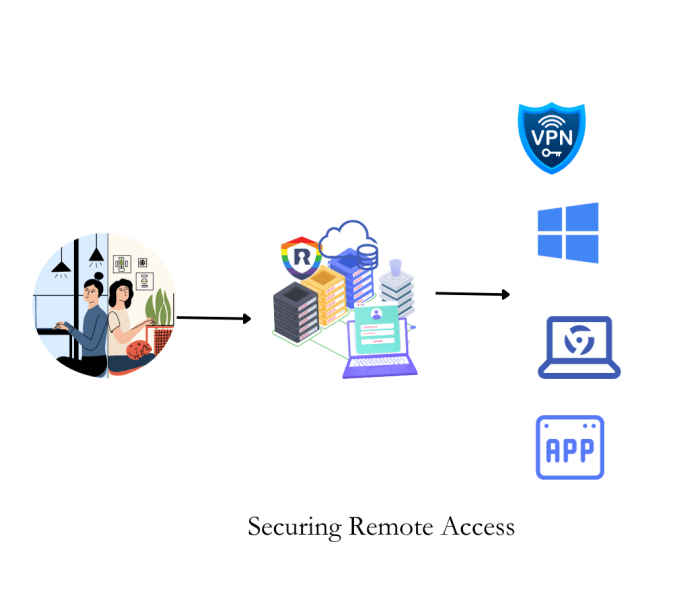
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...
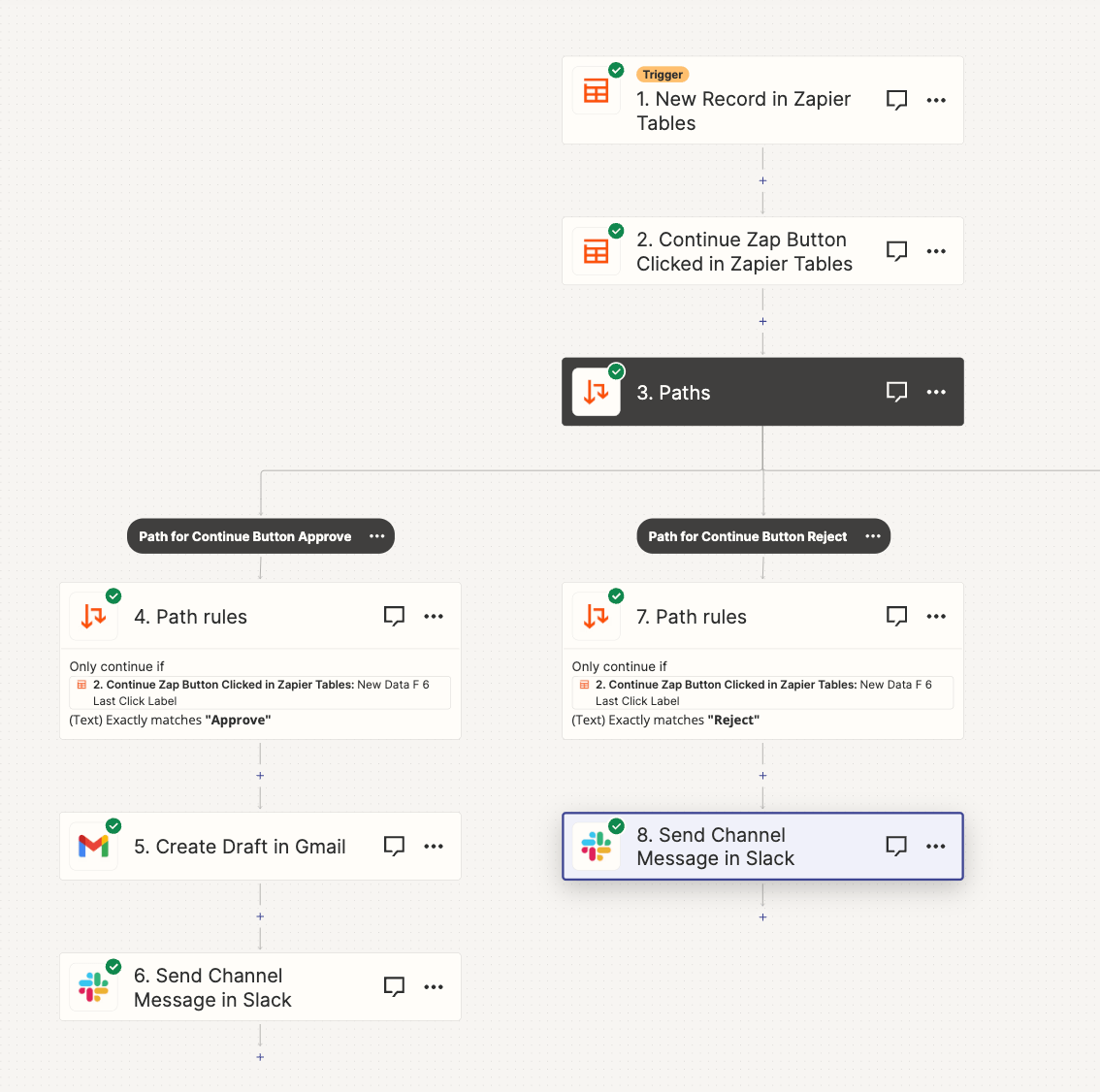
Serverless computing simplifies software development by removing the need for server management, allowing developers to concentrate on code. This arti...
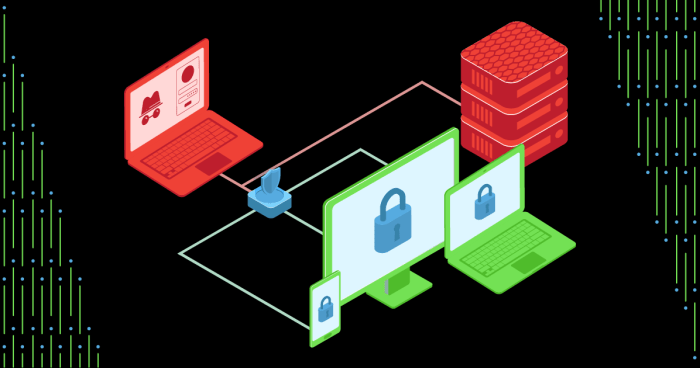
This comprehensive article explores the concept of honeypots in cybersecurity, detailing their purpose, diverse types (low, medium, and high-interacti...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...