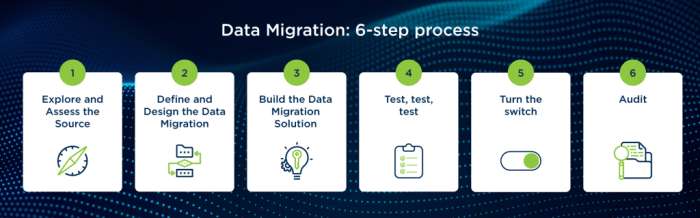
CRM System Migration: Key Considerations for a Smooth Transition
Migrating a CRM system is a complex undertaking, requiring careful planning and execution to ensure a successful transition. This comprehensive guide...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Migrating a CRM system is a complex undertaking, requiring careful planning and execution to ensure a successful transition. This comprehensive guide...
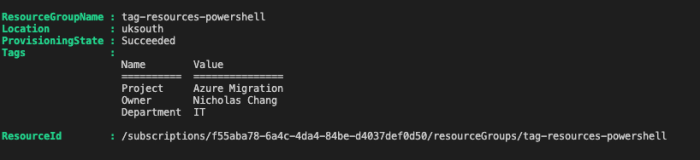
Automating the tagging of new resources is crucial for effective content management and organization. This guide provides a comprehensive overview of...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...
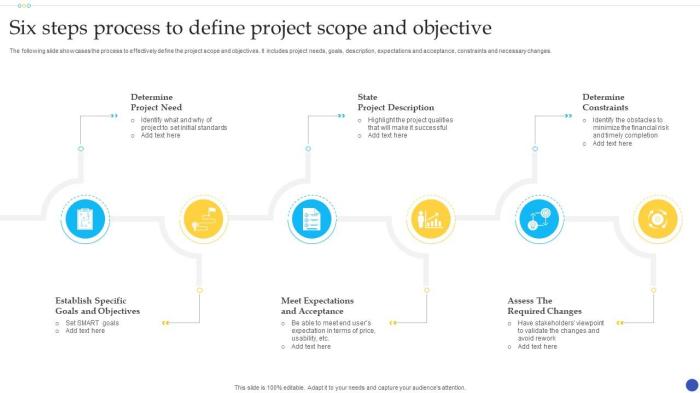
To successfully navigate a FinOps journey, establishing clear goals for each iteration is crucial. This involves more than just cutting costs; it's ab...

The KISS (Keep It Simple, Stupid) principle is a powerful concept advocating for clarity and efficiency by prioritizing ease of understanding and exec...

This comprehensive article explores the critical practice of cloud cost anomaly detection, providing a detailed overview of its definition, benefits,...

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...
This comprehensive guide delves into the essential practice of end-to-end (E2E) testing for web applications, a critical step in ensuring application...
Optimizing cloud database costs is crucial for efficient IT budgeting and sustainable business growth. This comprehensive guide explores the key facto...
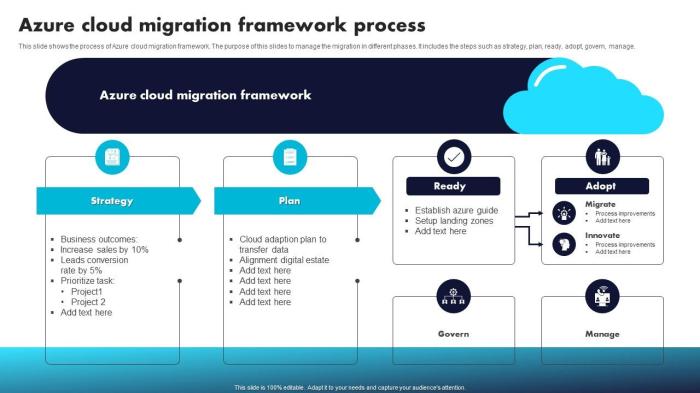
Successfully navigating a cloud migration requires a robust cloud governance framework to mitigate risks and ensure compliance. This comprehensive gui...

Containerizing legacy applications, with their inherent complexities and technical debt, requires a strategic approach. This process begins with under...
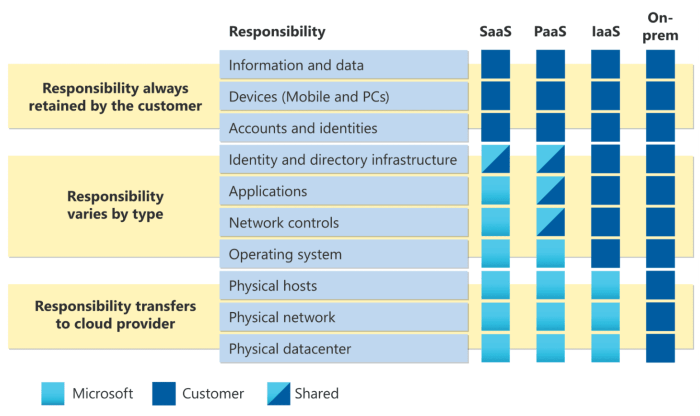
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...