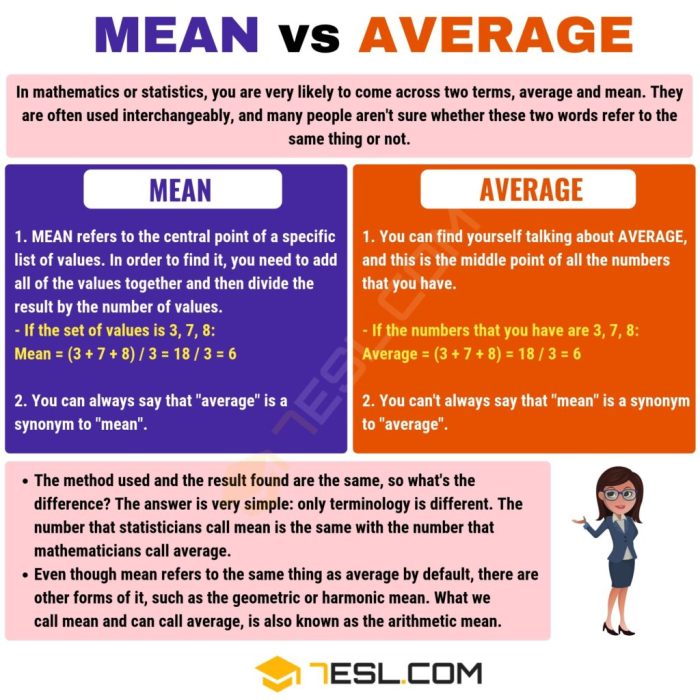
Mean Time to Recovery (MTTR): Definition, Calculation, and Importance
Mean Time to Recovery (MTTR) is a critical metric that measures the average time required to restore a system or component after a failure, directly i...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Mean Time to Recovery (MTTR) is a critical metric that measures the average time required to restore a system or component after a failure, directly i...

Cloud computing's benefits hinge on the reliability of its underlying systems. This guide provides a comprehensive overview of designing robust cloud...
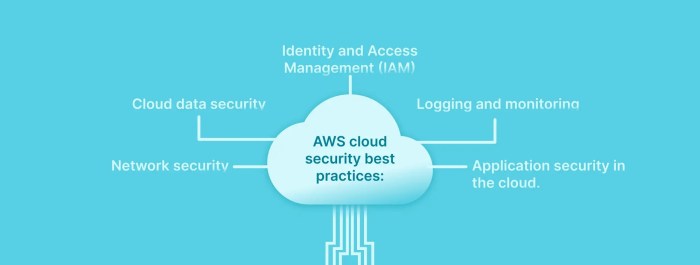
Embarking on a cloud migration requires a robust security strategy to protect your data and infrastructure. This comprehensive guide outlines essentia...
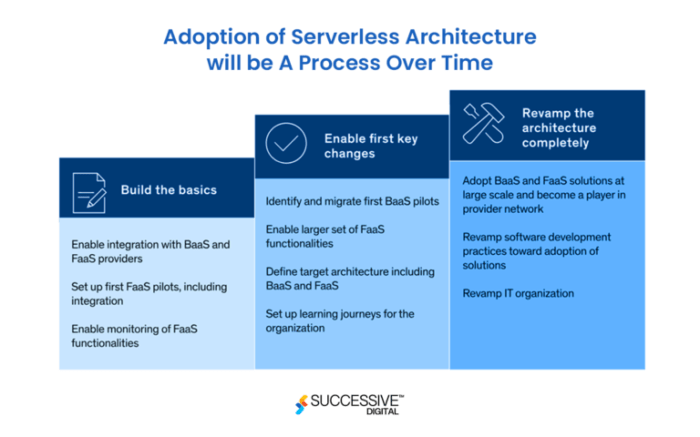
This article delves into the essential role of CloudEvents in the modern serverless landscape, exploring how this standard promotes interoperability a...
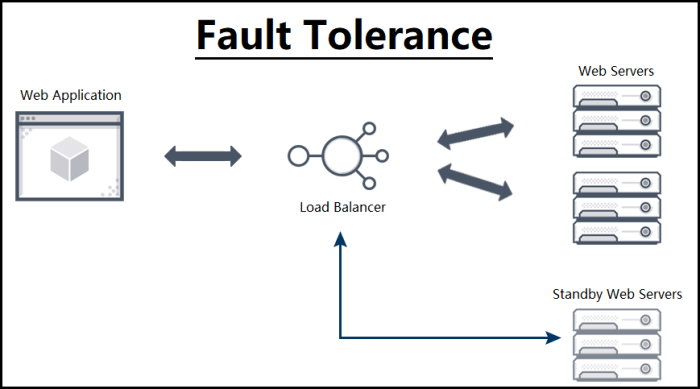
This guide provides a comprehensive overview of designing for fault tolerance in cloud environments, a critical aspect often overlooked in modern appl...

This article offers a comprehensive overview of data partitioning strategies, essential for scaling and managing large datasets effectively. It explor...
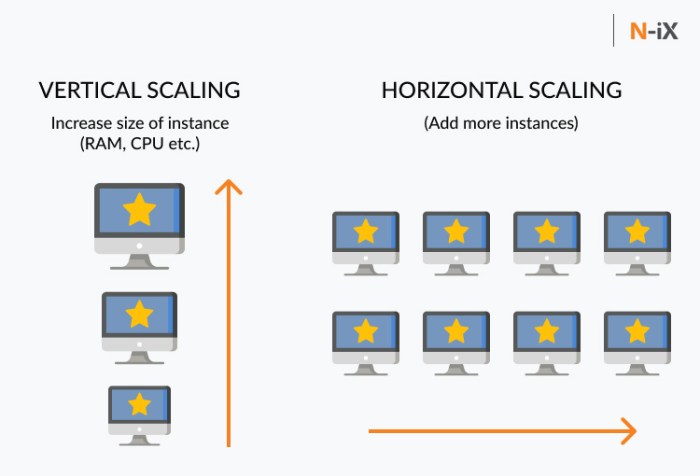
This article delves into the world of serverless databases, exploring their core concepts, evolution, and advantages over traditional systems. You'll...

Optimizing cloud resource utilization is essential for cost-effectiveness in today's digital environment. This guide, "Strategies for Minimizing Idle...

The cloud architect plays a vital role in designing and implementing cloud solutions, a crucial function for modern business success. This guide explo...

Sticky sessions are a fundamental technique in web application architecture that directs a user's requests to the same server within a cluster, mirror...
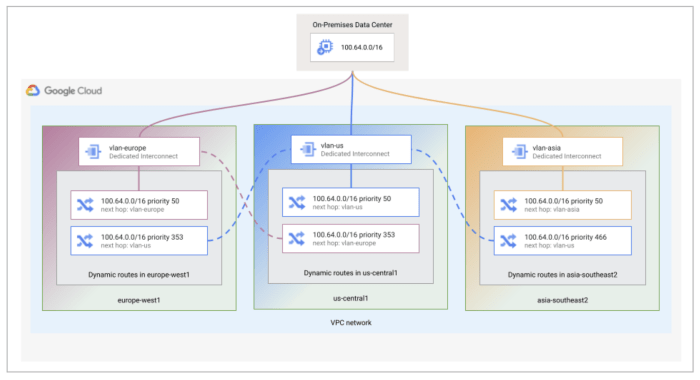
Cloud application performance hinges on efficient network paths, making optimization a critical priority for modern organizations. This article explor...
This article provides a thorough exploration of phishing attacks, outlining their deceptive tactics and potential impact on your digital security. Lea...