Serverless Step Functions: Orchestrating Workflows with Ease
This article provides a comprehensive overview of serverless Step Functions, detailing their core components, benefits, and practical applications in...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive overview of serverless Step Functions, detailing their core components, benefits, and practical applications in...

This article provides a comprehensive guide to reviewing and refining your FinOps practices to maximize cloud spending efficiency. It emphasizes the i...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...
This article outlines a comprehensive strategy for designing a secure cloud landing zone, a critical foundation for any organization adopting cloud se...

This guide provides a comprehensive approach to identifying and managing untagged resources in your cloud environment. By understanding the process of...

Migration projects often face resistance to change, stemming from psychological factors and concerns about the unknown. To ensure a successful transit...

Application modernization offers a strategic pathway to improved efficiency, scalability, and a stronger competitive edge in today's dynamic technolog...

To thrive in a competitive environment, engineering teams must prioritize cost-aware decision-making. This guide provides a comprehensive overview of...
Application migration presents two key strategies: replatforming and refactoring. Understanding the distinctions between these approaches is critical...
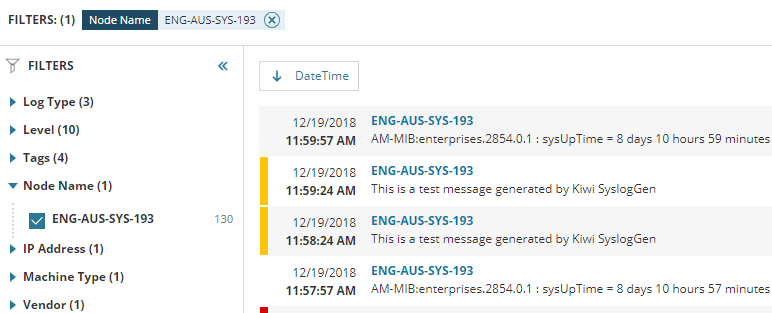
Modern businesses can leverage the power of real-time insights by treating raw log data as dynamic event streams. This approach, explored in detail, e...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...

Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...