Implementing Data Masking: A Practical Guide for Protecting Sensitive Information
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...

Choosing between managed databases and self-hosted solutions is a critical decision impacting operational efficiency, cost, and adaptability for any o...
This comprehensive guide explores the transformative power of Zero Trust Network Access (ZTNA) in modern cybersecurity, outlining its core principles...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...
Runbooks are critical for standardizing processes and improving operational efficiency by providing clear, documented procedures for IT tasks and issu...
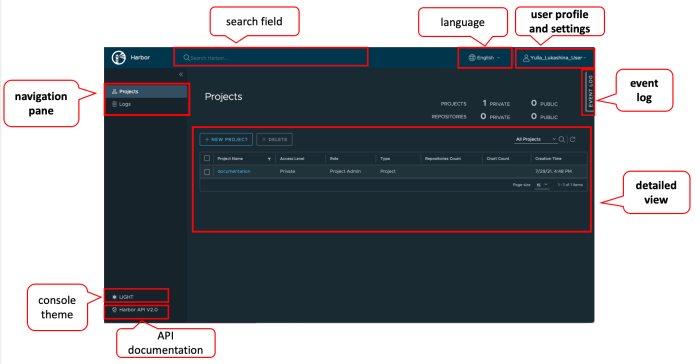
In the dynamic world of software development, container registries play a crucial, yet often overlooked, role. Serving as a secure and organized repos...
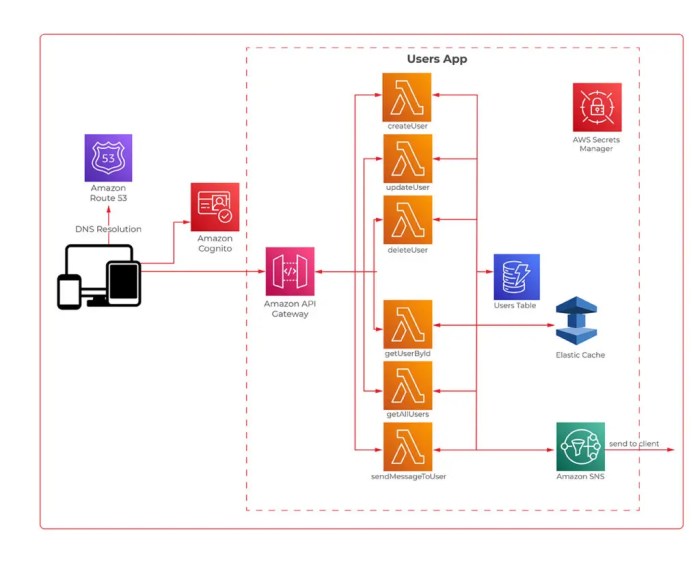
This comprehensive guide delves into the strategic design and implementation of multi-cloud serverless architectures, exploring the core fundamentals...

Optimizing application performance often involves caching strategies, and the cache-aside pattern is a powerful method to reduce database load and imp...
This article delves into the crucial practice of cache invalidation, a key element in optimizing web performance and user experience. Understanding an...

Ensuring data consistency is paramount when designing and deploying microservices architectures. This comprehensive guide explores the challenges of m...
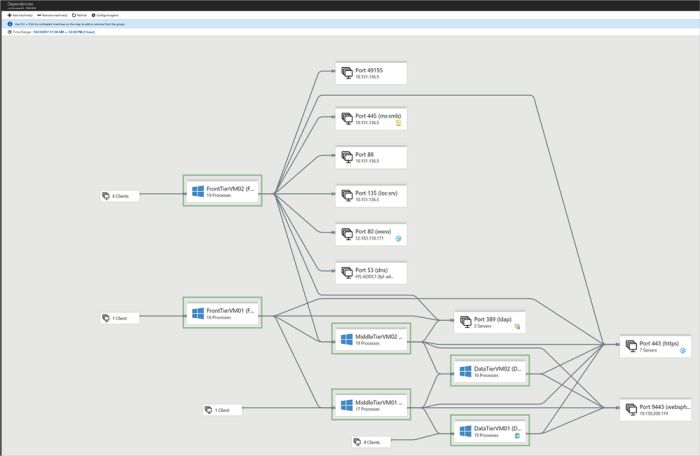
Migrating applications effectively requires a thorough understanding of their internal dependencies. This blog post explores application dependency an...