
Security Challenges in Serverless Computing: A Comprehensive Guide
This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...

This article provides a comprehensive guide to Service Level Objectives (SLOs) and Service Level Indicators (SLIs), explaining their crucial roles in...
Successfully migrating to the cloud requires more than just technical prowess; it demands a deep understanding of your organization's culture and its...

This guide provides a comprehensive framework for calculating and managing error budgets, essential for ensuring the reliability of complex systems. I...

Cloud migration offers significant benefits, but it also presents numerous challenges that can impact project success. This comprehensive article expl...

Digital Rights Management (DRM) is a critical component of the digital landscape, serving to protect intellectual property in the realm of content cre...
Navigating the complexities of migration requires careful attention to legal and contractual obligations across various domains. This comprehensive gu...

This article dissects the "Replace Architecture" anti-pattern, outlining its characteristics, motivations, and detrimental consequences for software d...
This article delves into the powerful combination of Event-Driven Architecture (EDA) and serverless computing, exploring how they synergistically crea...

Data masking and tokenization are essential security practices for safeguarding sensitive data while maintaining its usability. This article delves in...
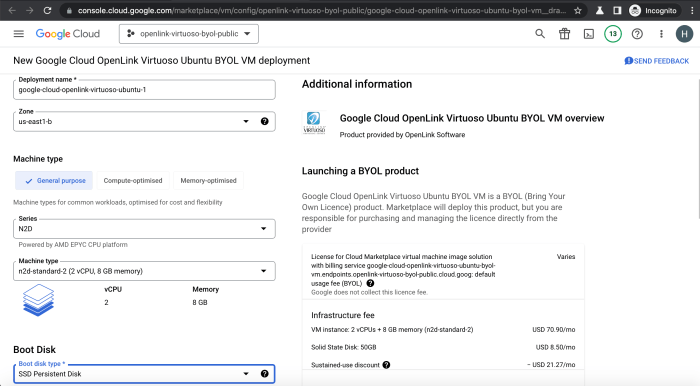
This article provides a comprehensive overview of Bring Your Own License (BYOL) in the cloud, exploring its core concepts, benefits, and potential cha...

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...