
Key Management Service (KMS): Definition, Benefits, and Best Practices
In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
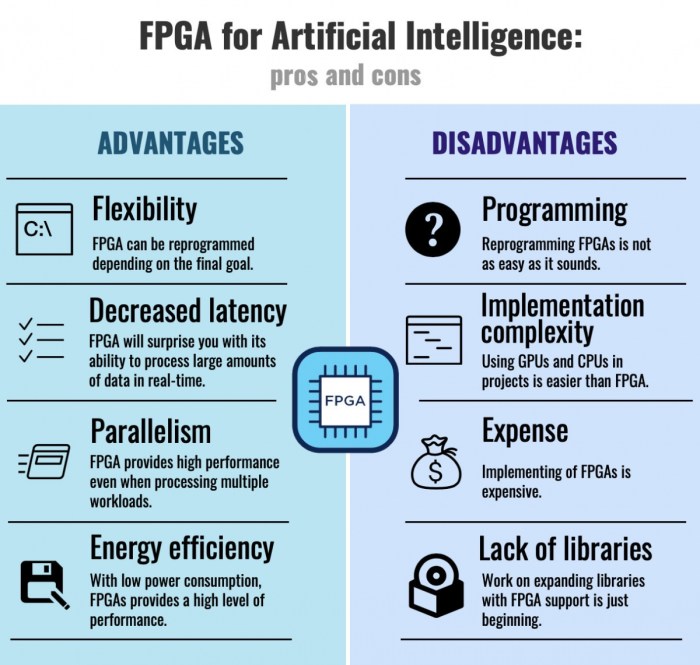
This article explores the significant advantages of Integrated Development Platforms (IDPs) in boosting developer productivity, covering key areas suc...

This article provides a comprehensive overview of designing scalable machine learning architectures, essential for handling large datasets and complex...
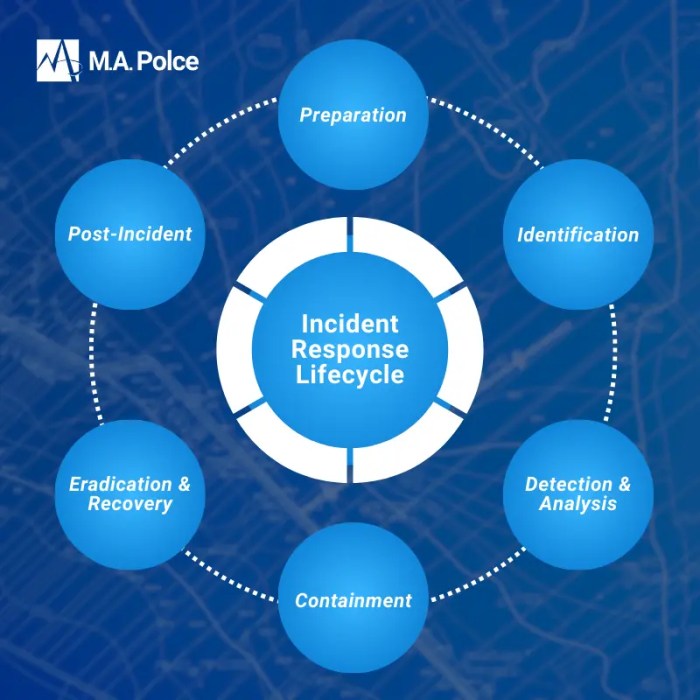
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...

Building a real-time data processing architecture is essential for applications requiring immediate insights. This guide explores the critical aspects...
This comprehensive guide provides a roadmap for creating a successful developer portal, covering everything from defining its core purpose and feature...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...
This article delves into the 'analysis paralysis' anti-pattern, a common pitfall in project planning that can severely impact timelines, budgets, and...

Cloud Development Kits (CDKs) are transforming cloud infrastructure management by enabling developers to define their cloud setups using familiar prog...
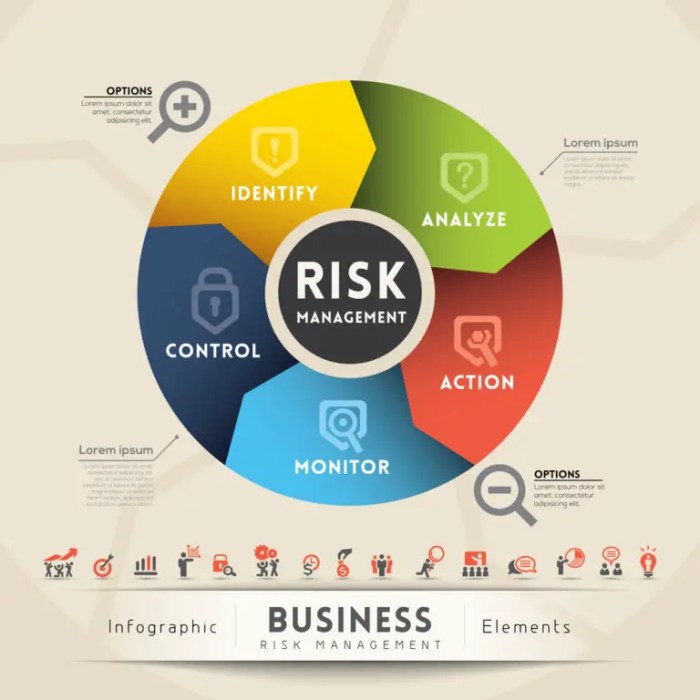
Cybersecurity Key Risk Indicators (KRIs) serve as vital early warning signals, enabling organizations to proactively manage and mitigate evolving cybe...

Serverless environments, while offering scalability and agility, introduce unique security challenges due to their ephemeral and distributed nature. T...

This comprehensive guide explores the critical practice of API versioning, outlining various strategies from Semantic Versioning to Header Versioning,...