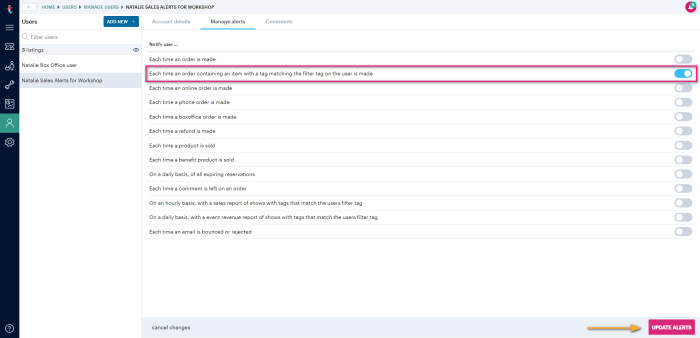
Automate Your Budget: Setting Up Cost Alerts and Notifications
Effectively managing cloud spending is crucial, and this guide provides a clear roadmap for establishing automated cost alerts and notifications. Lear...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Effectively managing cloud spending is crucial, and this guide provides a clear roadmap for establishing automated cost alerts and notifications. Lear...

Cloud-based database schema transformation is a vital process for optimizing database structures, ensuring they align with evolving business needs and...
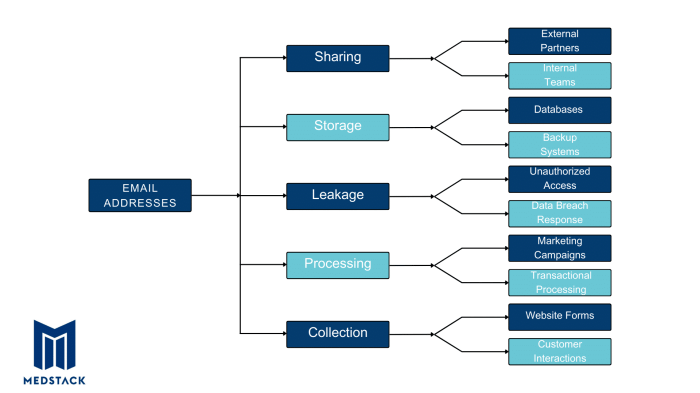
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...

Infrastructure as Code (IaC) is transforming modern IT by allowing infrastructure management through code, automating processes and enhancing efficien...

Understanding cloud environments requires diligent monitoring of key metrics across resource utilization, network performance, application behavior, a...

This article explores vital strategies for significantly improving deployment frequency, a key metric in modern software development. It examines the...
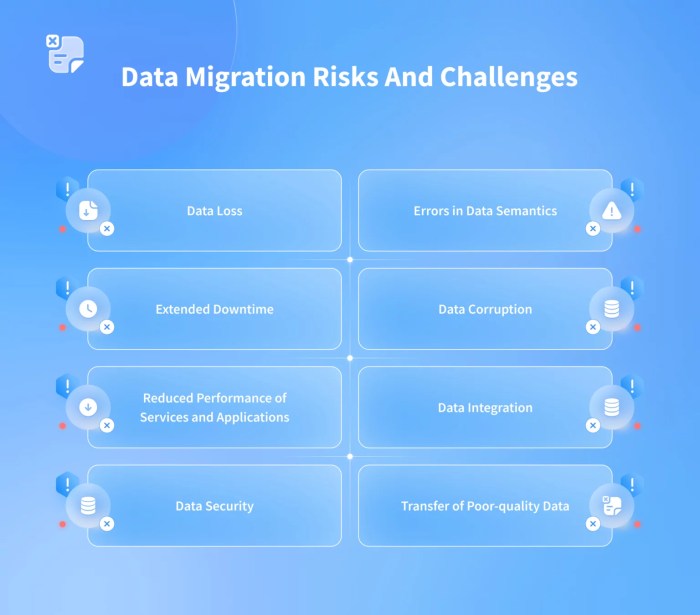
Data migration, the process of moving data across different systems, introduces significant security challenges that must be addressed. This article e...
This comprehensive guide offers a deep dive into the vast ecosystem of community resources available to serverless developers, from online forums and...

This comprehensive guide explores the essential strategies for continuous cloud optimization, covering crucial areas like cost management, performance...
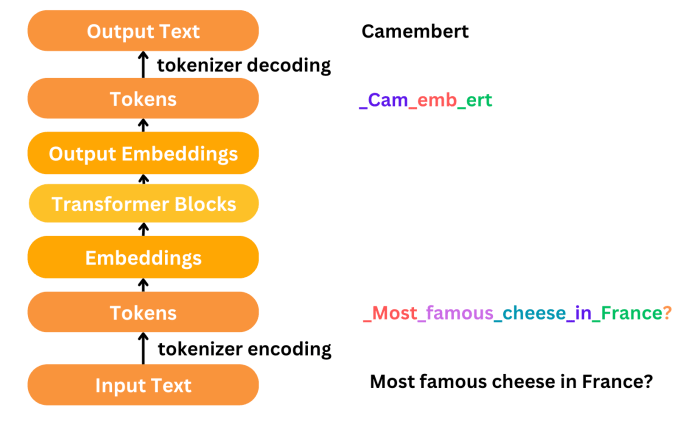
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
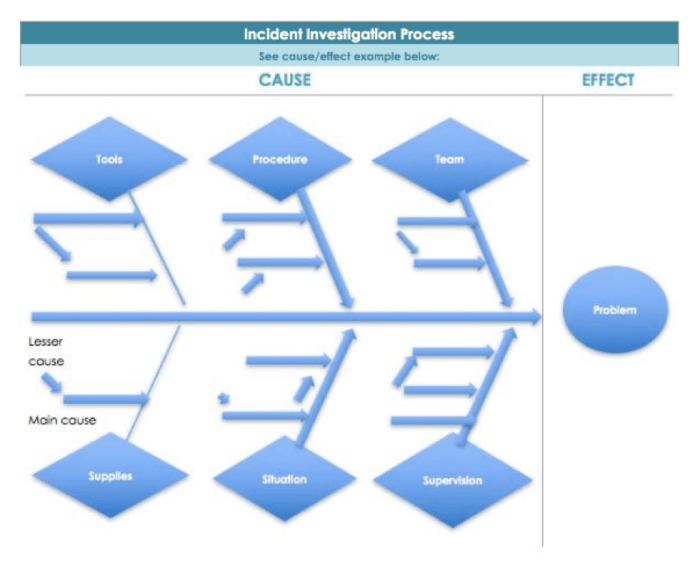
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...