
Understanding the CVE Database: A Comprehensive Guide
This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...
152 posts in this category

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...
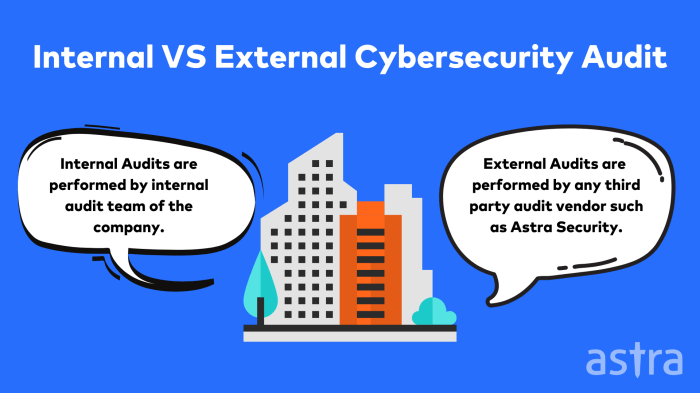
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.

This comprehensive guide explores Interactive Application Security Testing (IAST), detailing its fundamental principles, advantages, and practical imp...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...