Conducting Effective Cloud Security Risk Assessments: A Step-by-Step Guide
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...
152 posts in this category

This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...

This article provides a comprehensive guide to preventing SQL injection attacks specifically within cloud application environments. It covers critical...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...

Cloud-based businesses are increasingly vulnerable to Distributed Denial of Service (DDoS) attacks, which can disrupt online services and lead to subs...
In today's cloud-centric world, understanding Data Loss Prevention (DLP) solutions is critical for safeguarding sensitive information. This article pr...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...
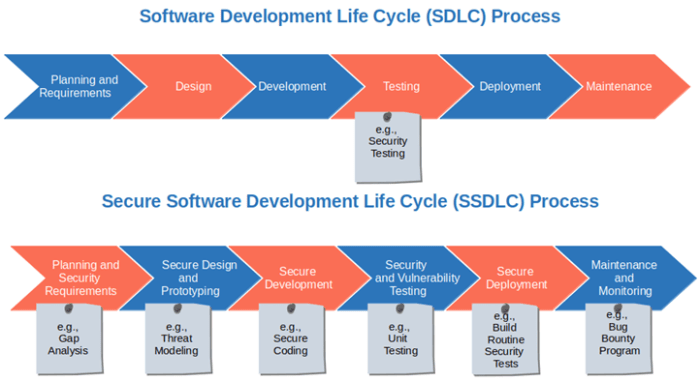
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...